Snyk – Splunk Integration via Cloudwatch Log Group
This post outlines the basic steps in pushing centralized snyk audit logs and issues into Splunk via a cloudwatch log group which is set as a target. This deployment can be replicated and/or re-invented for other 3rd party tools by leveraging the "Partner event sources" in Amazon Eventbridge
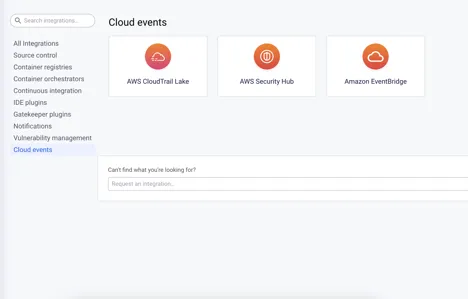
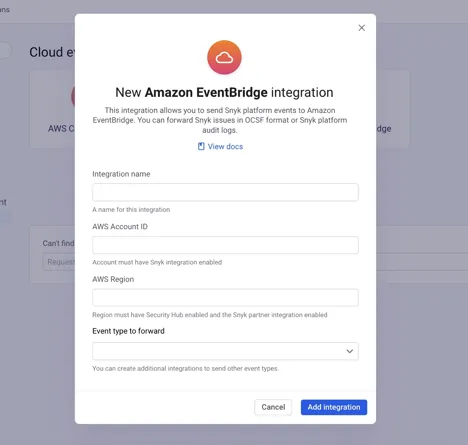
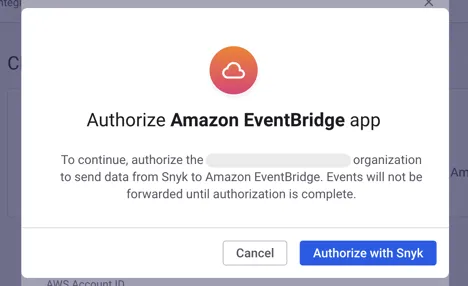
- Go to the EventBridge console.
- Navigate to the Partner event sources page under the Integration section.
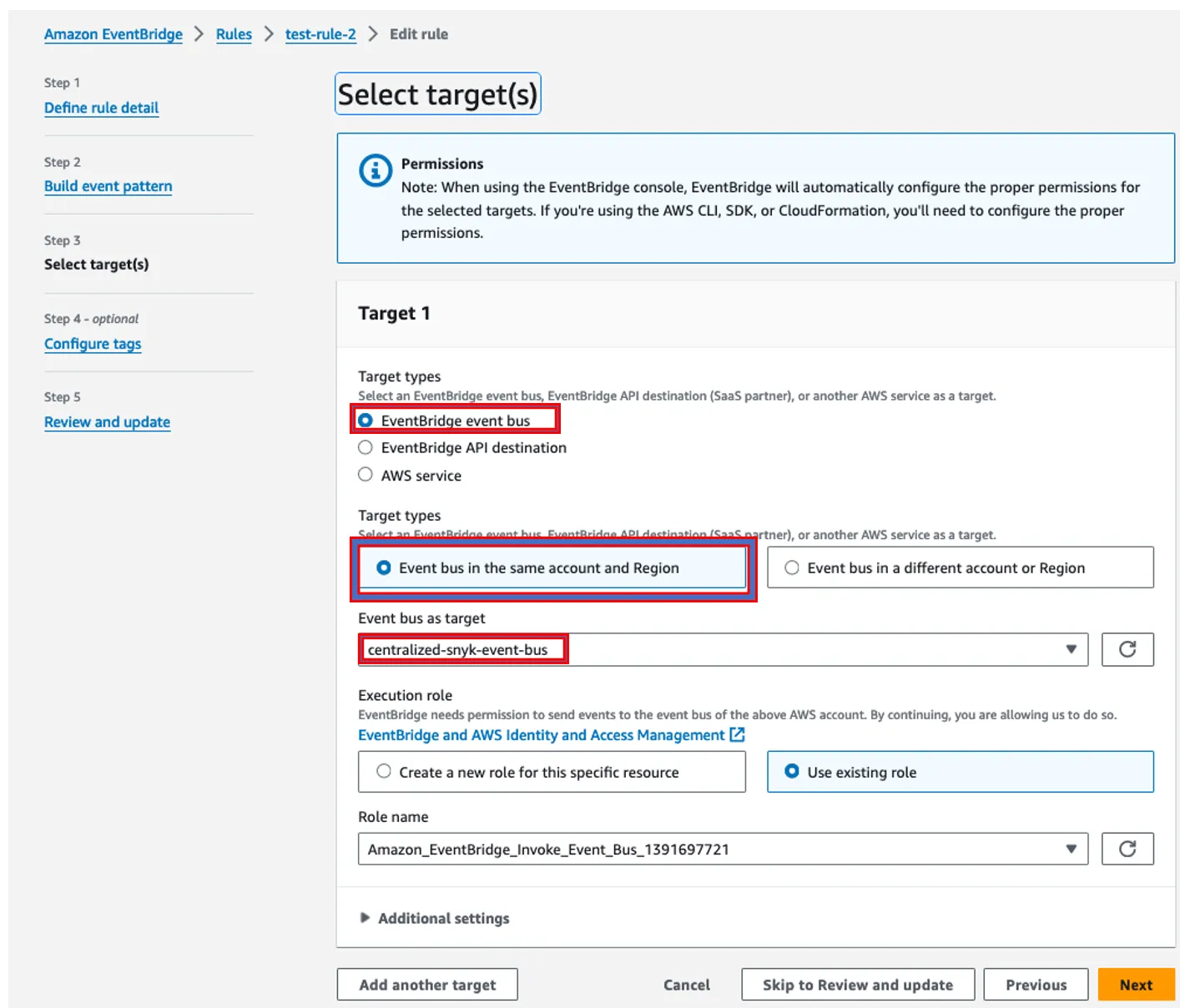
- Deploy cloudformation template to create an eventbridge rule with the centralized event bus.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
AWSTemplateFormatVersion: '2010-09-09'
Description: Creates eventbridge rules and delivers Snyk events via Amazon EventBridge to CloudWatch Logs from the Centralized Event Bus
Resources:
Testing:
Type: AWS::Events::Rule
Properties:
EventBusName: <replace with your eventbus name>
EventPattern:
"source": [{"prefix": aws.partner/snyk.io}]
account:
- !Ref AWS::AccountId
Targets:
- Arn: <replace with arn of your eventbus>
Id: <replace with your snyk-centralized-eventbus-id>
RoleArn: !GetAtt SnykEventBridgeSenderRole.Arn
# EventBridge IAM Role to send events to an event bus
SnykEventBridgeSenderRole:
Type: AWS::IAM::Role
Properties:
RoleName: SnykEventBridgeSenderRole
AssumeRolePolicyDocument:
Version: "2012-10-17"
Statement:
- Effect: Allow
Principal:
Service: events.amazonaws.com
Action: sts:AssumeRole 