The Safe Room | S5 - E2 | Tactics to Prevent Data Exfiltration: Locking Down S3
In this episode of The Safe Room, we explore the critical topic of data exfiltration within AWS environments. We'll explore how data can be illicitly extracted from S3 buckets and discuss strategies for detection and prevention. Our focus will be on understanding the services that can be exploited for data exfiltration, and the configurations necessary to detect and prevent such incidents.

- Understanding Data Exfiltration in AWS S3: We start by defining data exfiltration and discussing its significance in the context of AWS S3. This includes an overview of how data can be illicitly transferred or accessed, which sets the stage for understanding the depth of this issue.
- Methods of S3 Data Exfiltration: Next, we explore the various tactics that attackers employ to exfiltrate data. This segment sheds light on the common vulnerabilities and misconfigurations that can lead to such security breaches, supported by real-world scenarios and examples.
- Live Demonstration of a Data Breach: In a compelling live demonstration, we simulate a data exfiltration scenario from an S3 bucket. This practical illustration not only highlights how easily data breaches can occur but also serves as a powerful visual aid in understanding the mechanics behind such incidents.
- Detecting and Alerting Unusual Activities: The focus then shifts to detection strategies. We discuss how to utilize AWS tools and services to monitor S3 buckets for unusual activities, and how to effectively set up alerts in AWS to notify of potential breaches.
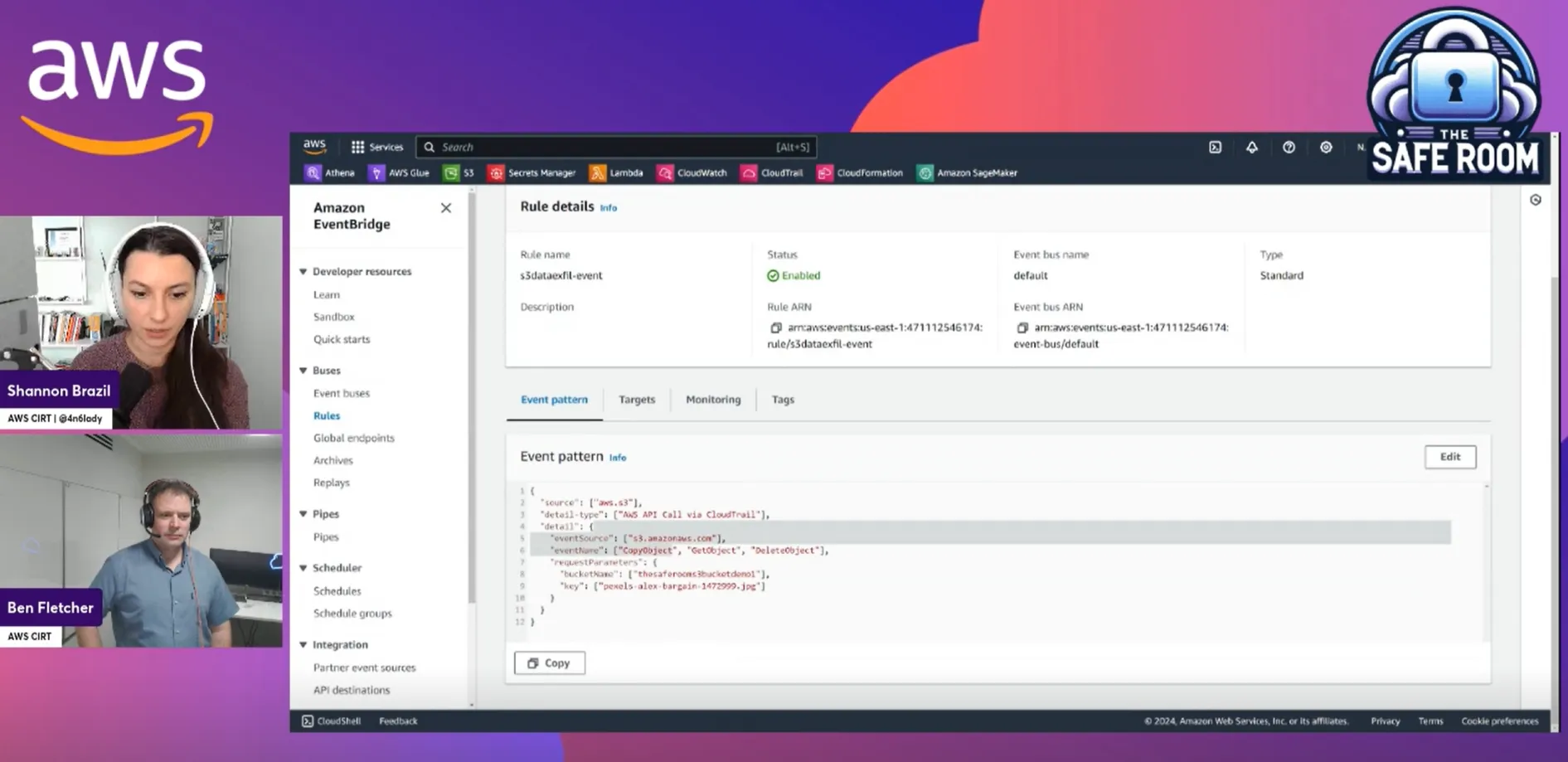
- Preventive Measures and Best Practices: One of the most critical parts of the episode is our deep dive into prevention strategies. We cover best practices for securing S3 buckets, including configuring bucket policies, access controls, and encryption. This segment is designed to equip viewers with the knowledge to not only identify risks but also implement robust security measures.

- Ben Fletcher: LinkedIn
Any opinions in this post are those of the individual author and may not reflect the opinions of AWS.
