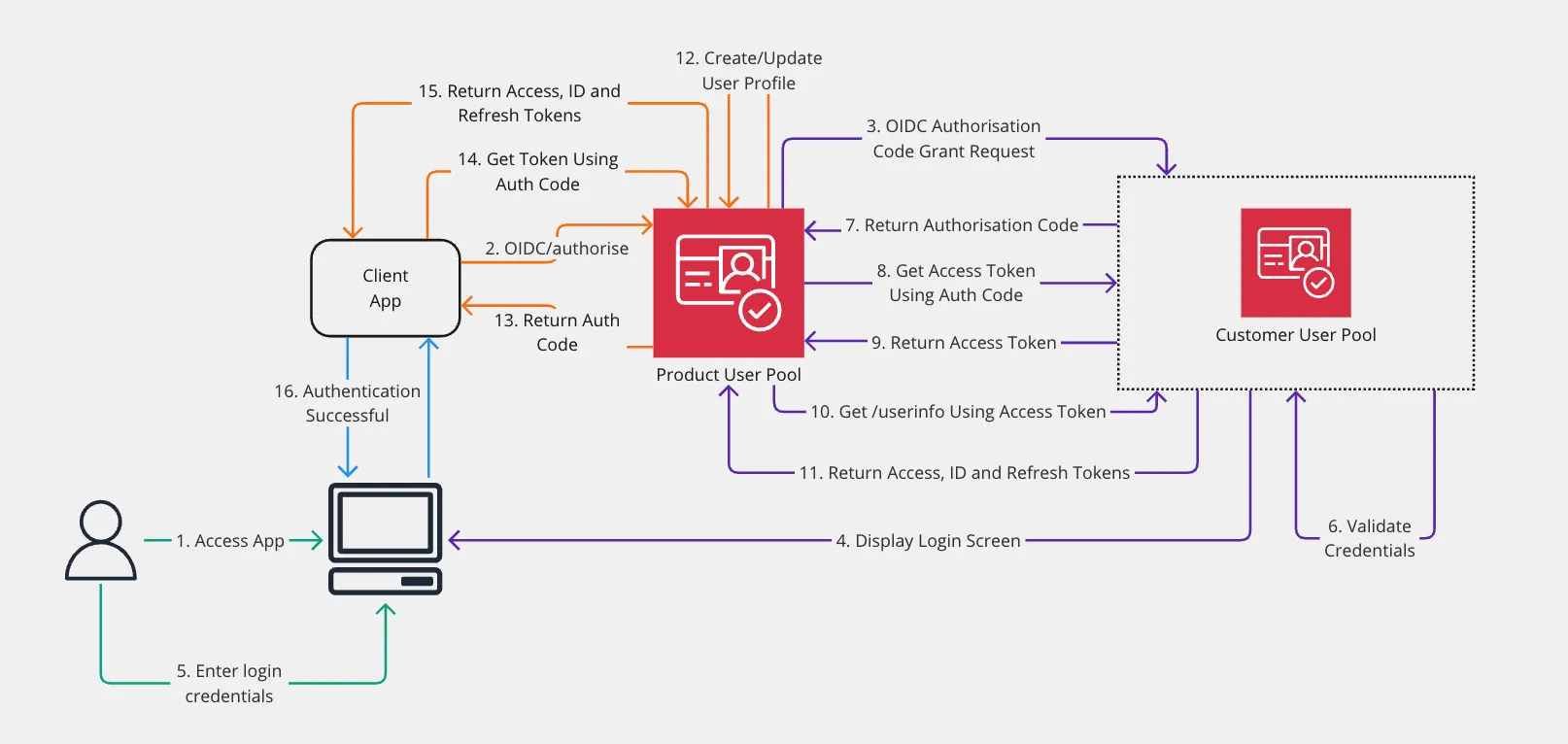
How to add Cognito as OIDC Identity Provider in Cognito
This post will look at how to setup AWS Cognito to use an OpenID Connect (OIDC) identity provider of another Cognito user pool.
For users federated through SAML 2.0 or an OpenID Connect (OIDC) identity provider, Amazon Cognito user pools has a free tier of 50 MAUs per account or per AWS organization.
For users who sign in through SAML or OIDC federation, the price for MAUs above the 50 MAU free tier is $0.015.
- Head to AWS Cognito and click
Create user pool. - Select
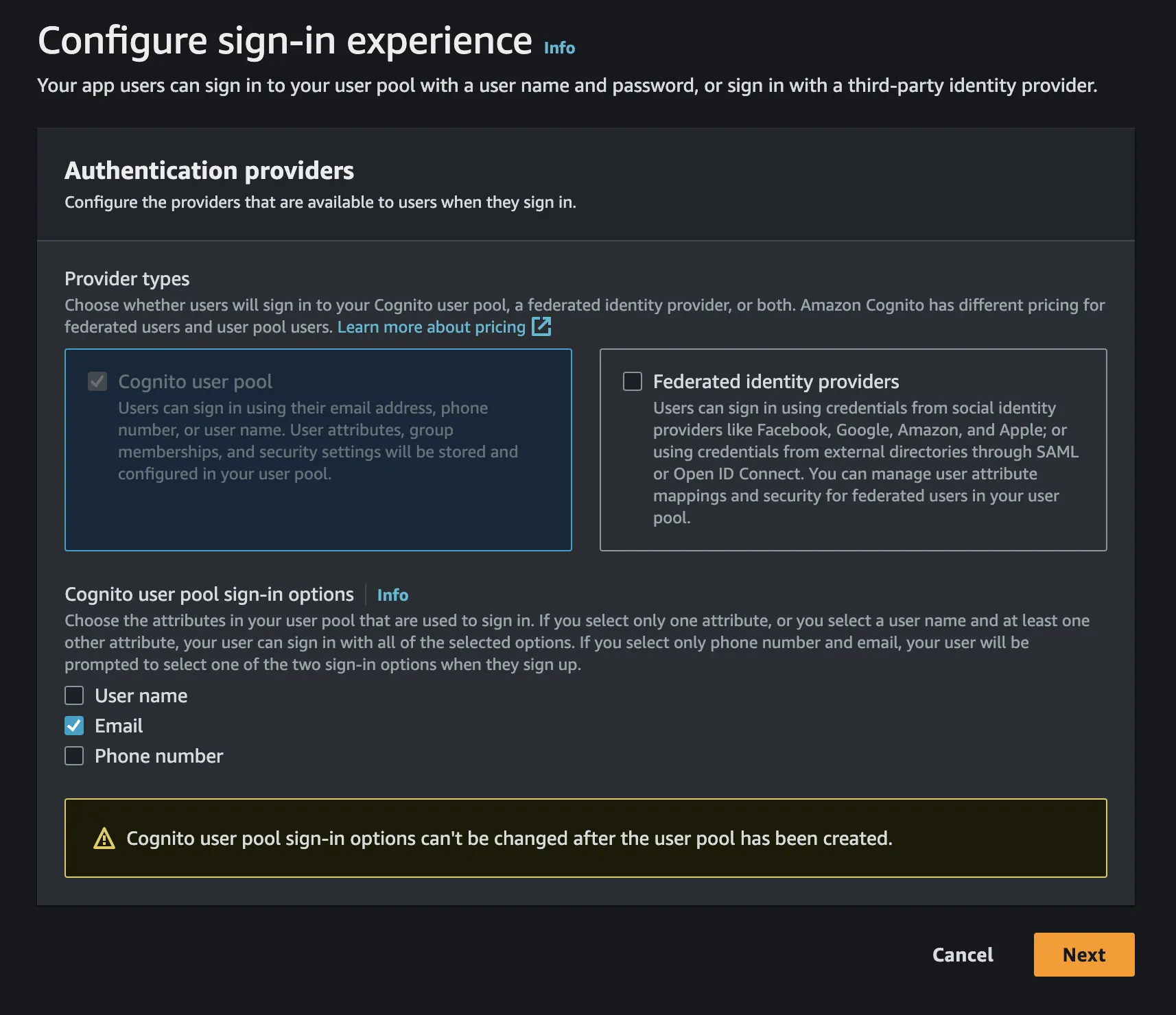
Provider typesto be onlyCognito user pooland sign-in options to be whatever suits your use case (I chose email):
- Follow through the next steps setting up your password policy, MFA, User account recovery and Sign-up experience as you desire.
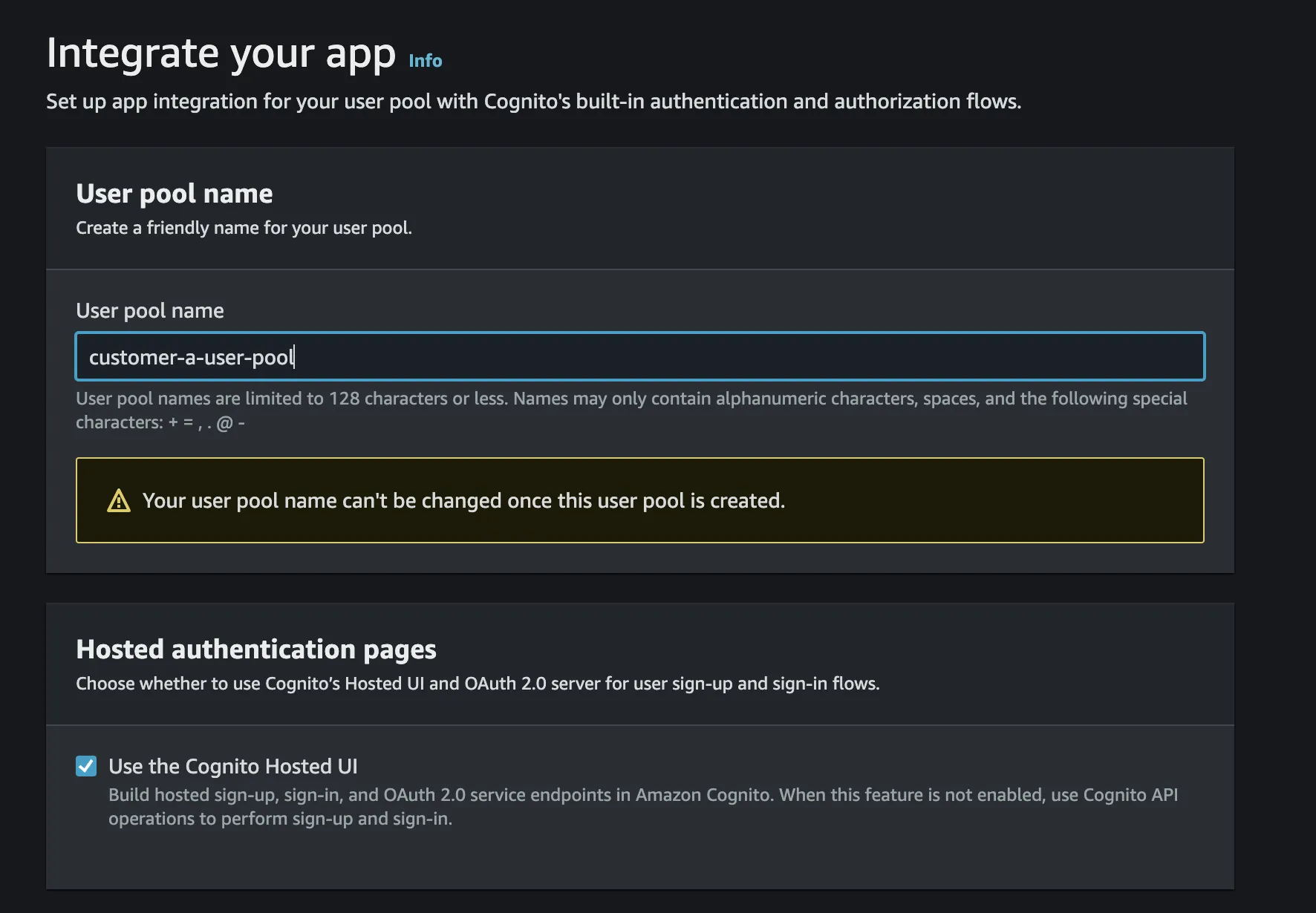
- On the
Integrate your apppage enter your desired user pool name. - Tick
Use the Cognito Hosted UI
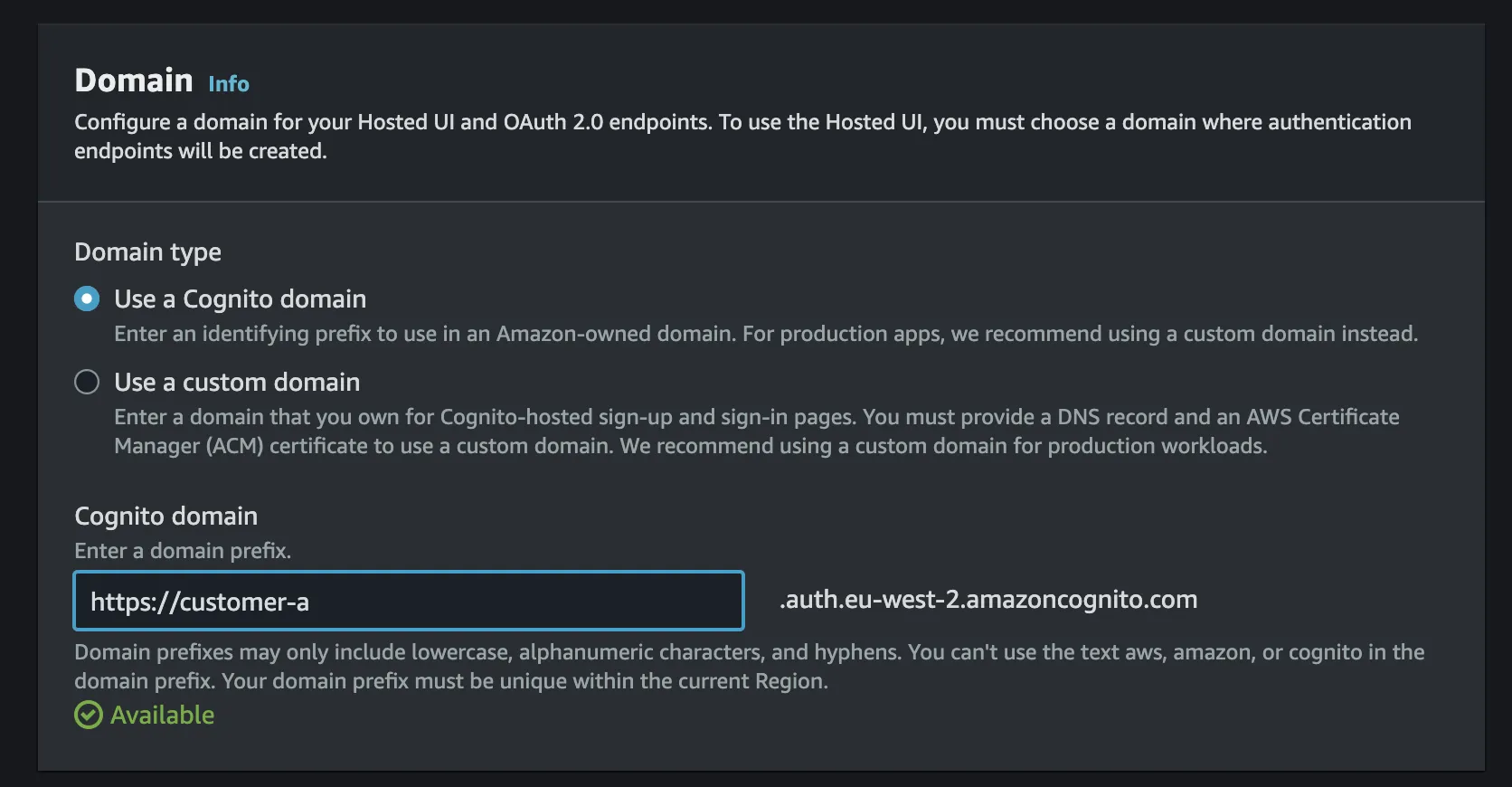
- Select the domain setup you want but using a cognito domain is fine if you don't have a custom domain.
- Set up the client app as follows:
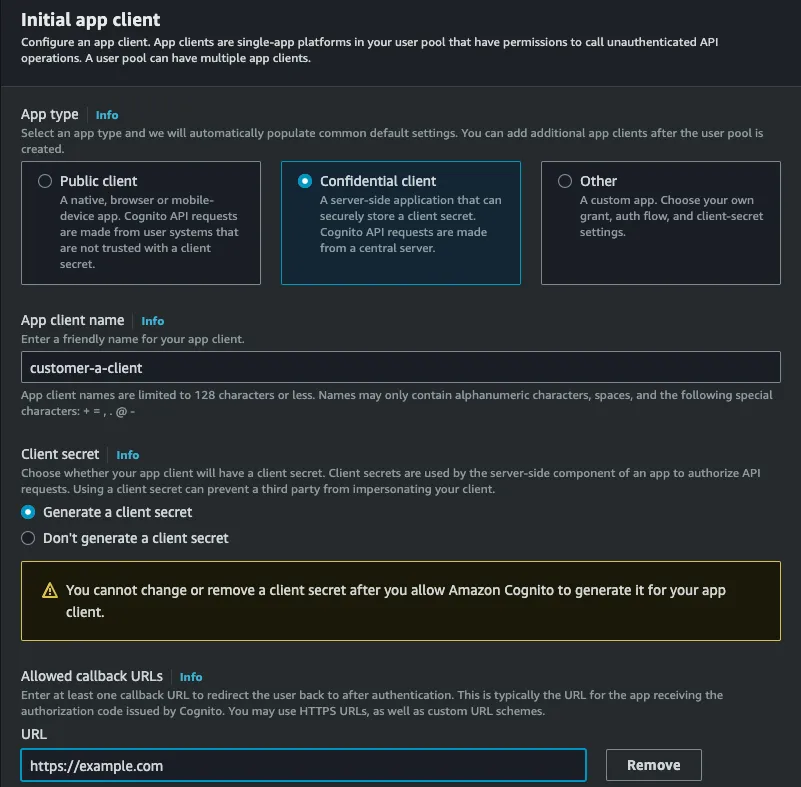
https://example.com but we will come back to change this later.- In the
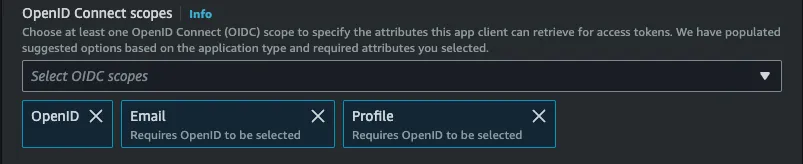
Advanced app client settingsyou can leave everything as it is except adjust the scope as follows:
- Review and create your user pool!
- Let's get a user added to this customer's user base when we are still in the area. Keep note of the user's details as you will need them later of course.
- Head to AWS Cognito and click
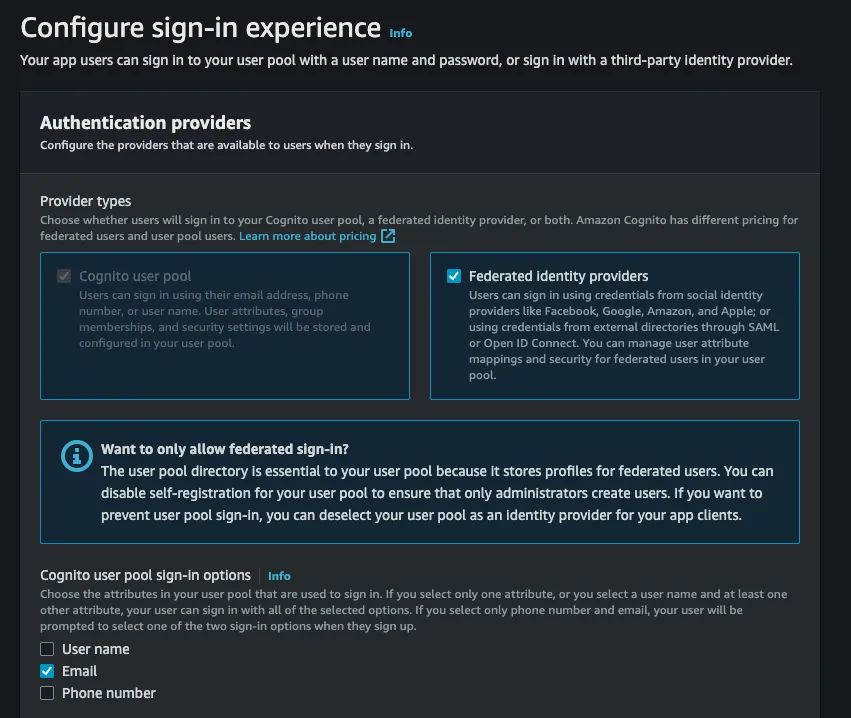
Create user pool - On the
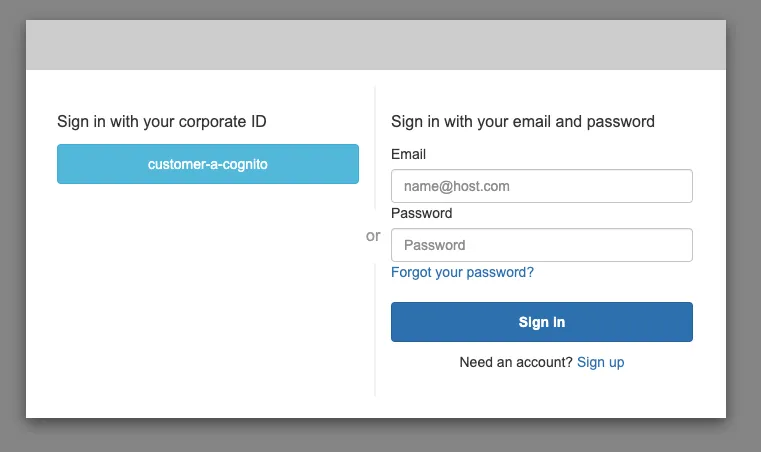
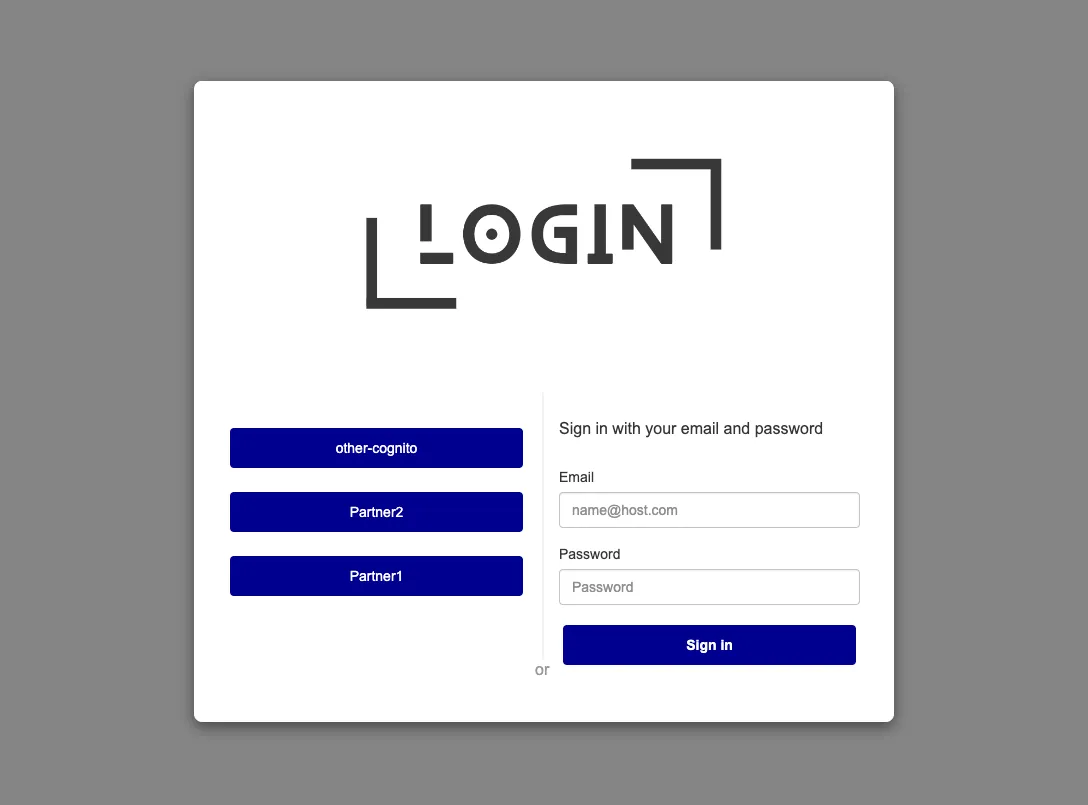
Configure sign-in experiencescreen selectFederated identity providersas an option and the sign-in options whatever suits you:
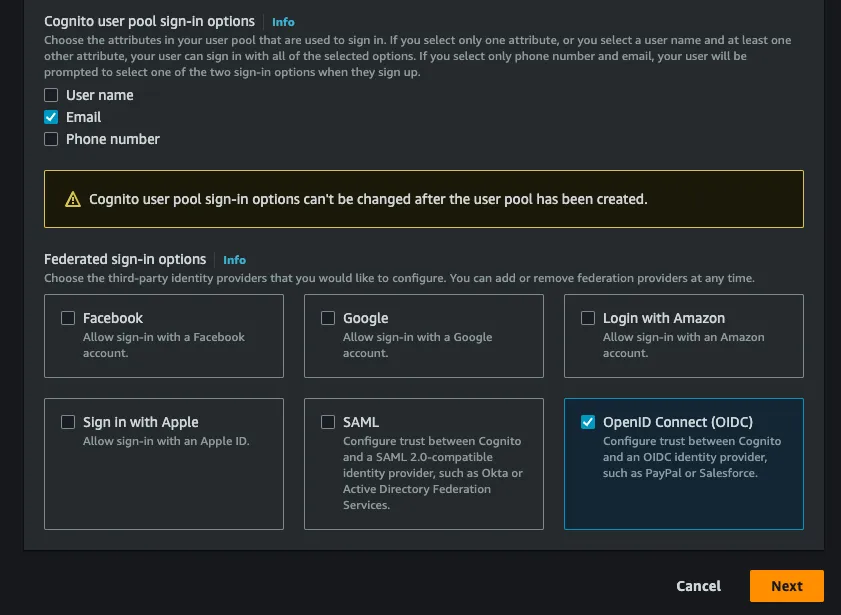
- For
Federated sign-in optionstickOpenID Connect (OIDC)
- Follow through the next steps setting up your password policy, MFA, User account recovery and Sign-up experience as you desire.
- Next you will be presented with a
Connect federated identity providersscreen - this is where the magic happens. Here fill in the client id and client secret from your customer's user pool's app client. (i.e. the client app we created in the steps above)
App Integration tab of your Customer's user pool and then selecting the client you created: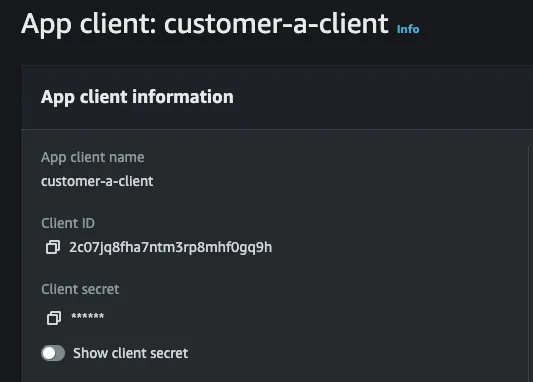
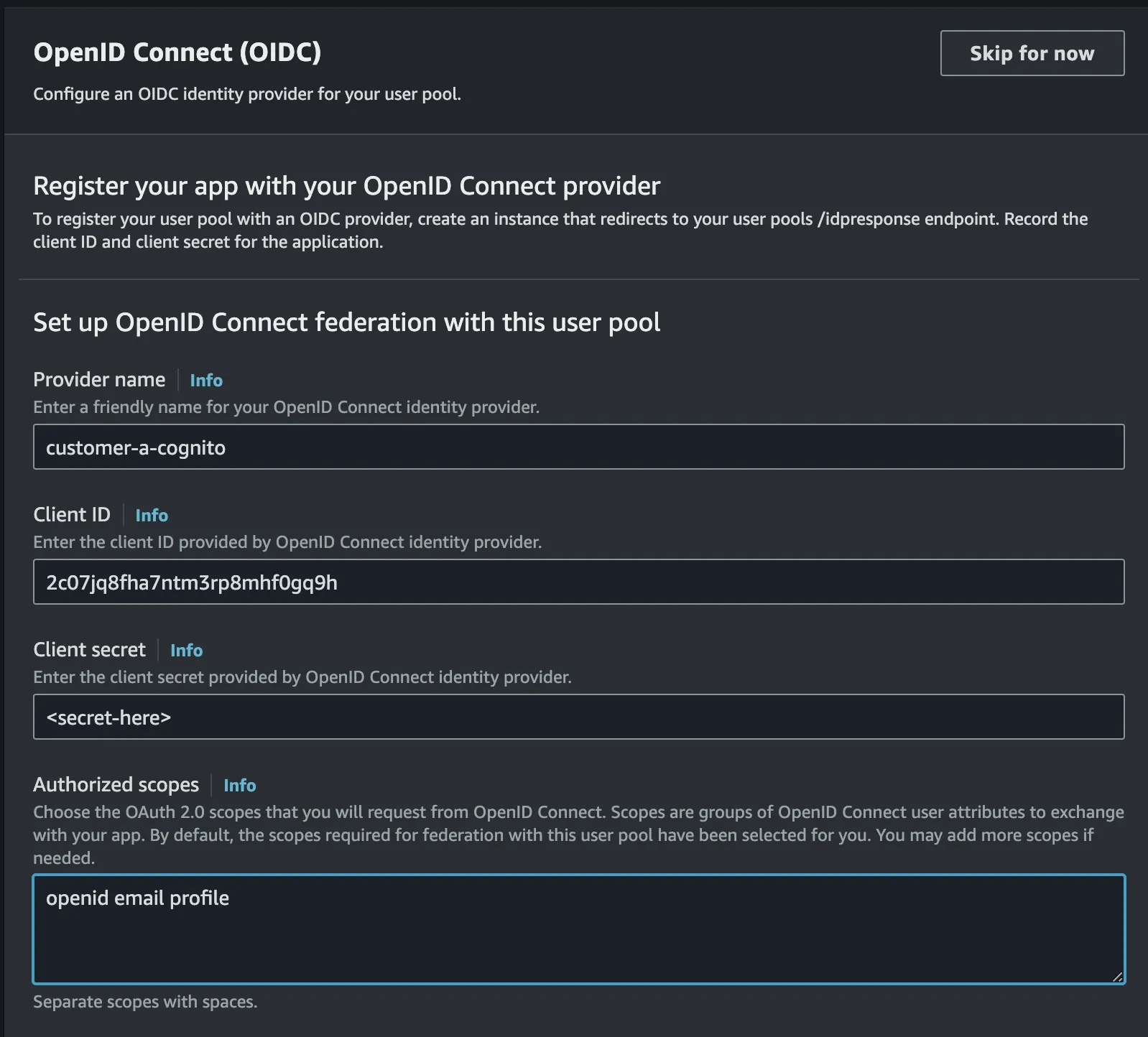
- Keep
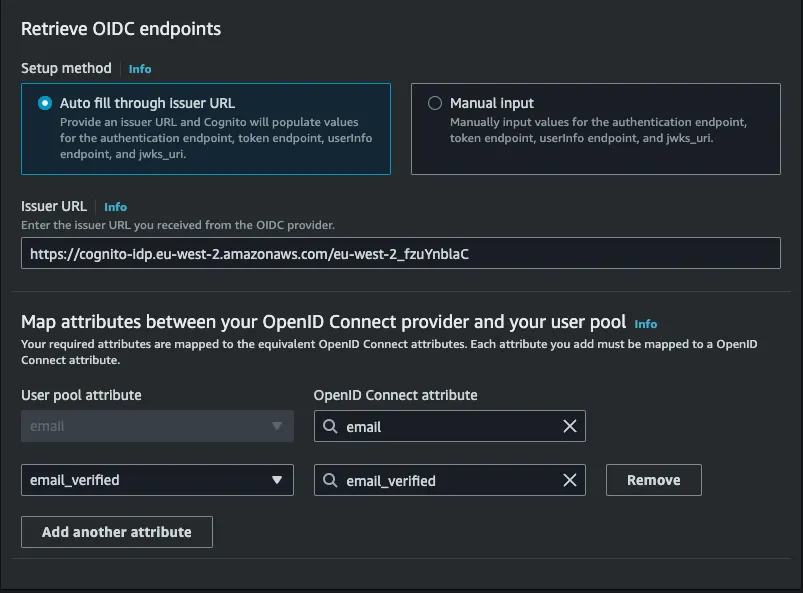
Attribute request methodasGET - Setup the issuer url where the url will be:
https://cognito-idp.{region}.amazonaws.com/{customerUserPoolId}
- Add the
emailattribute andemail_verifiedas shown here:
- Name your user pool, for example,
product-user-pool. - Setup your app client as you require. It is not required at this point to generate a client secret for this user pool. You can add one if you want but I wouldn't recommend it if you plan to use this user pool in a webapp or mobile app.
- In the advanced settings, ensure the following:
Identity providers to include your newly created IDP: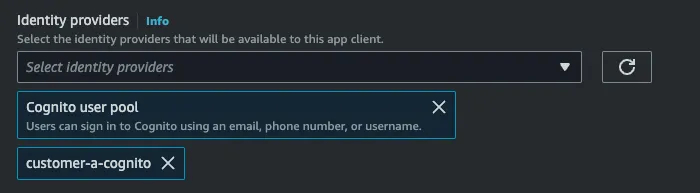

- Review and create your second user pool!
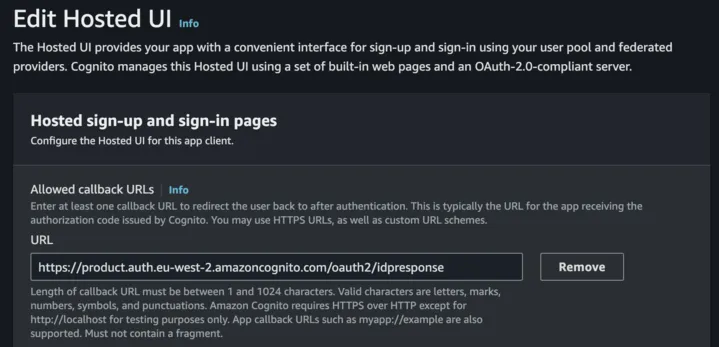
- One last step, we need to go to the Customer user pool and adjust the allowed callbacks for the client.
- Head to the
App integrationtab and then click into your client and go to the hosted UI settings. - Set the allowed callbacks to be the following:
https://{productCognitoDomain}/oauth2/idpresponse