Automate the Account Factory for Terraform setup
And understand the mechanics behind the scenes
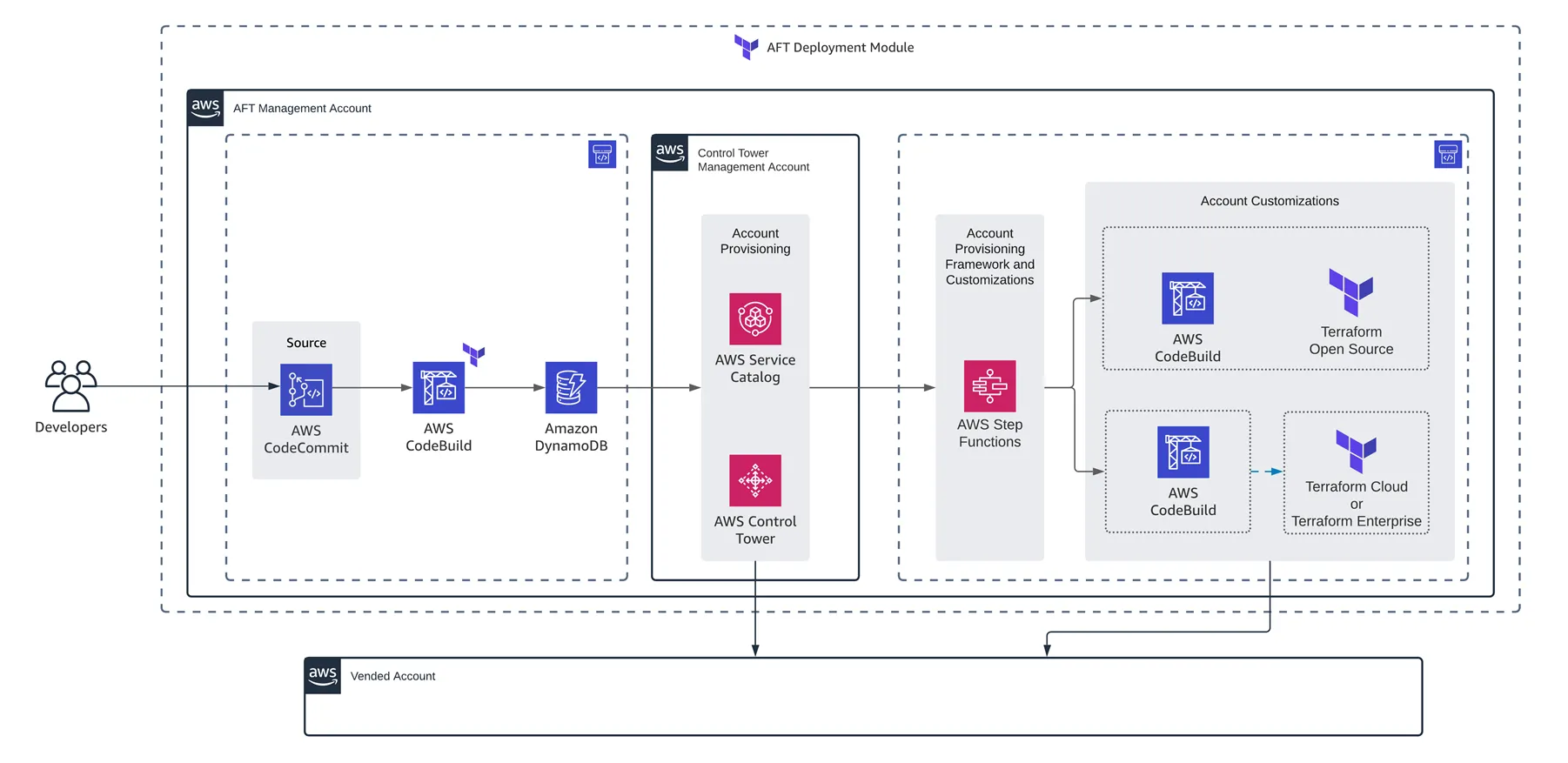
- Control Tower: AFT uses Control Tower Landing Zones to vend new AWS Accounts. Actually, Control Tower introduces the term of Account Factory. We could imagine the AFT as a Terraform implementation of an Account Factory, but it could be others available.
- Service Catalog: this service is used to prepare and deploy IaC templates in AWS, like for instance let Account Factories to create AWS accounts on-demand.
- Source Repositories, CodeBuild and CodePipeline: as shown in the diagram above, the user (like a Developer, for instance) will push an IaC commit on a Git repository, that will trigger a CI/CD pipeline to vend and customize on-demand AWS accounts (known as vended accounts). We'll dig on that later.
- (existing) 💰Control Tower Management Account: this is the root AWS account of our Organization (also known as the management account, paying account or billing account) and will be used to start configuring the module using a Landing Zone. Imagine this account as the seed (or origin) AWS account.
- (new) 🐙 AFT Management Account: this will be an AWS account dedicated to host & orchestrate the vending and customization of new AWS accounts requested as code by IaC users (e.g. Developers). It will be created using Service Catalog from the Control Tower Management account.
- (new) 🤖 Shared Accounts: the AFT makes use of an Audit account and a Log Archive account for centralized security, compliance and long-term storage of logs.
- (new) 🚀 Vended Accounts: as the name says, these are the new AWS accounts created and customized by AFT, in a on-demand basis.
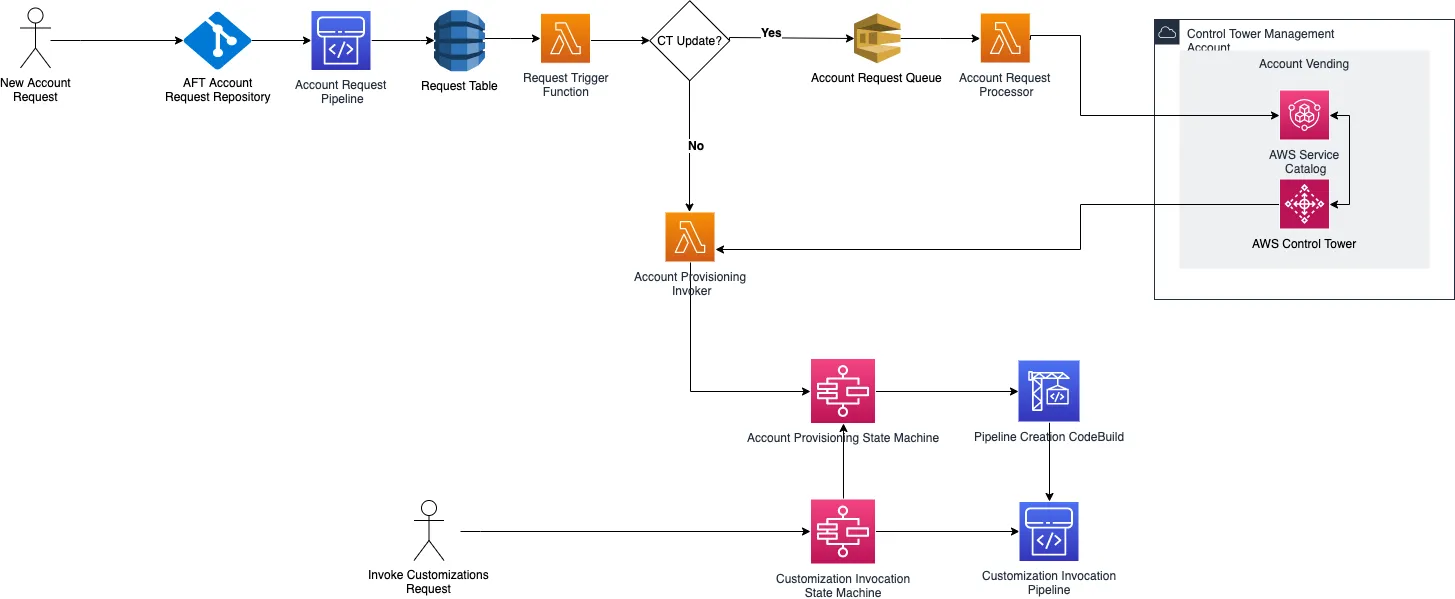
- To vend new AWS accounts:
- A new AWS account request is received as a
git pushoperation. As of today, the AFT supports several git repositories, like CodeCommit, Bitbucket, GitHub, GitHub Enterprise, GitLab and GitLab Self Managed. - That
git pushtriggers a new CodePipeline pipeline, that invokes lambda functions to use Control Tower and Service Catalog to vend a new AWS account. The orchestration of these functions and the pipelines is made by Step Functions. - After the new AWS account is vended, two groups of customizations pipelines are invoked:
- Global customizations: definitions to be applied across all vended AWS accounts, like base VPC configurations, IAM roles, S3 buckets, or anything needed to be deployed by default in all our accounts. These customizations will be defined by us in Terraform, and hosted in a git repository.
- Account customizations: these definitions will apply to certain groups of vended AWS accounts, for example access restrictions for S3 in Production, NAT Gateways, EventBridge rules to monitor the Health of some resources, or any other specific needs for a subgroup of vended AWS accounts. These customizations work the same way as the Global customizations, which is by using Terraform modules (folders) in a separate git repository.
- Update existing vended AWS account:
- After pushing the changes to the AWS account request git repo, the user has to invoke the customizations State Machine (using Step Functions) that will trigger both Global customizations and Account customizations pipelines. These pipelines will run the Terraform projects affected by the AWS account, to update their definitions.
- (required) Account Request repo: this repo will host all AWS vended accounts, and must be accesible by Users (e.g. Developers) to request new AWS accounts. Sample repo.
- (required) Global Customizations repo: this repo will host all Global Customizations, as a Terraform module/folder. Sample repo.
- (required) Account Customizations repo: this repo will host account or group-specific Account Customizations, as Terraform modules/folders. Sample repo.
- (required) Account Provisioning Customizations repo: this repo will host all account or group-specific provisioning-time Account Customizations, as Terraform modules/folders. Sample repo.
- (recommended) AFT setup repo: as mentioned in the title of this Article, we'll set up the AFT using a code-driven approach. It would be good to version these commands/definitions in a Git repo to not lose our commands.
☑️ 2. Create Log Archive AWS Account
☑️ 3. Create Audit AWS Account
☑️ 4. Enable Landing Zone in our AWS Region
☑️ 5. Create AFT Management Account
☑️ 6. Deploy AFT Module
☑️ 7. Post-deployment and Next Steps
AWSControlTowerAdminAWSControlTowerStackSetRoleAWSControlTowerCloudTrailRoleAWSControlTowerConfigAggregatorRoleForOrganizations
AdminAccess in the 💰Control Tower Management Account to create each Role and their respective trust policy & permissions.aft-log-archive.create-account CLI command using the 💰Control Tower Management Account with AdminAccess:+ sign when setting up the email of our new AWS account. That trick helps us to have multiple email addresses signed in AWS, but all of them will arrive to the same email inbox without the plus sign suffix, which in this case would be your-email@domain.com.create-account command from above will display a new account creation Id:111111111111 for the next steps.create-account CLI command in the 💰Control Tower Management Account with AdminAccess:list-create-account-status command to get the AWS account status:222222222222 as soon as it gets successfully created.create-landing-zone CLI command.landing-zone.json:governedRegionsfield defines on which region(s) our Landing Zone will be deployed.organizationStructure.securityandorganizationStructure.sandboxare new Organizational Units (OUs) to be created automatically by thecreate-landing-zonecommand in our root AWS account:- The Security OU will be named
aft-sharedin this example, and will host both Audit and Log Archive AWS accounts (both 🤖 shared accounts). Both accounts will be moved automatically by thecreate-landing-zonecommand after creating this new OU. - The Sandbox OU will be named
aft-accountsin this example, and will host all 🚀 vended AWS accounts and also the 🐙 AFT Management AWS account.
centralizedLogging.accountIdwill include the AWS account Id of our new 🤖 Log Archive account, which in this example is111111111111.centralizedLogging.configurationswill define the retention period of the Log S3 buckets.securityRoles.accountIdwill include the AWS account Id of our new 🤖 Audit account, which in this example is222222222222.
create-landing-zone command using the 💰Control Tower Management Account with AdminAccess:
get-landing-zone-operation command. In my experience, it's much easier to see the UI to explore if any problems are found during the process.create-landing-zone command, using the wrong account to do so, reaching AWS account creation limits, fix incorrect IAM Roles, ... In all of these cases we have to find the cause of the issue (sometimes looking at the CloudFormation logs) and re-run the create-landing-zone command over and over again.AWS Control Tower Account Factory and can be found in the Management Console or using the servicecatalog search-products command of the AWS CLI.AdminAccess, to run the search-products command:ProductViewSummaries[0].ProductId field to identify the AWS Control Tower Account Factory product. Actually, we can modify the previous command to get the Id only:list-provisioning-artifacts command for this:AWSAdministratorAccess role. You can use the IAM Identity Center to get temporary programmatic credentials for this role in the 💰Control Tower Management Account.AWSServiceCatalogEndUserAccess role in our 💰Control Tower Management Account, to run this command:aft-accounts.json. That file includes some parameters to be given to our new Service Catalog product, which are related to the E-mail & OU of that new AWS account to be created:AWSAdministratorAccess role in the 💰Control Tower Management Account to get new AWS account Id:333333333333.AWSAdministratorAccess role in the 💰Control Tower Management Account:terraform apply again after fixing the issue.