IaC Security Scanner - Generative AI app with PartyRock
The AI-Powered IaC Security Scanner using PartyRock
Published Feb 26, 2024
Infrastructure-as-code (IaC) release security is growing in importance because to the speed at which the digital world is developing. By meeting this important requirement, the AI-Powered IaC Security Scanner indicates a substantial advancement in the field of IaC security.
The IaC Security Scanner with AI Powered is not a simple tool to use. It has native support for numerous IaC systems, such as Kubernetes, Terraform, and AWS CloudFormation. As a result, your IaC installations are safe across all platforms and support a wide range of compatibilities.
Key Features of AI-Powered IaC Security Scanner
- In-Depth Vulnerability Assessment
- Compliance with Industry Standards
- User-Friendly Interface
All you need to do is visit the Party Rock Website to sign up, and the magic happens in mere seconds.
Step #1 : Sign In
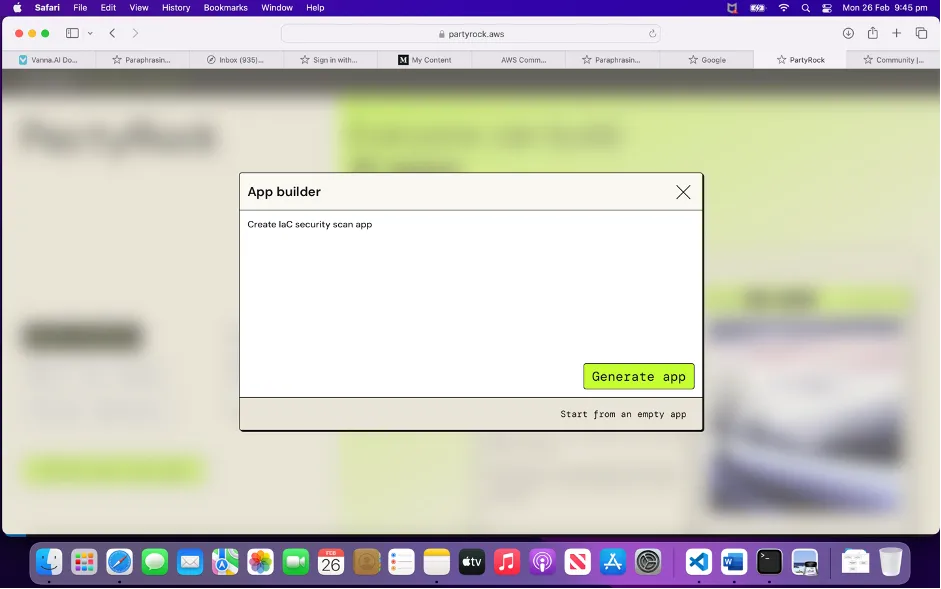
Step #2 : Write your Prompt with your Idea
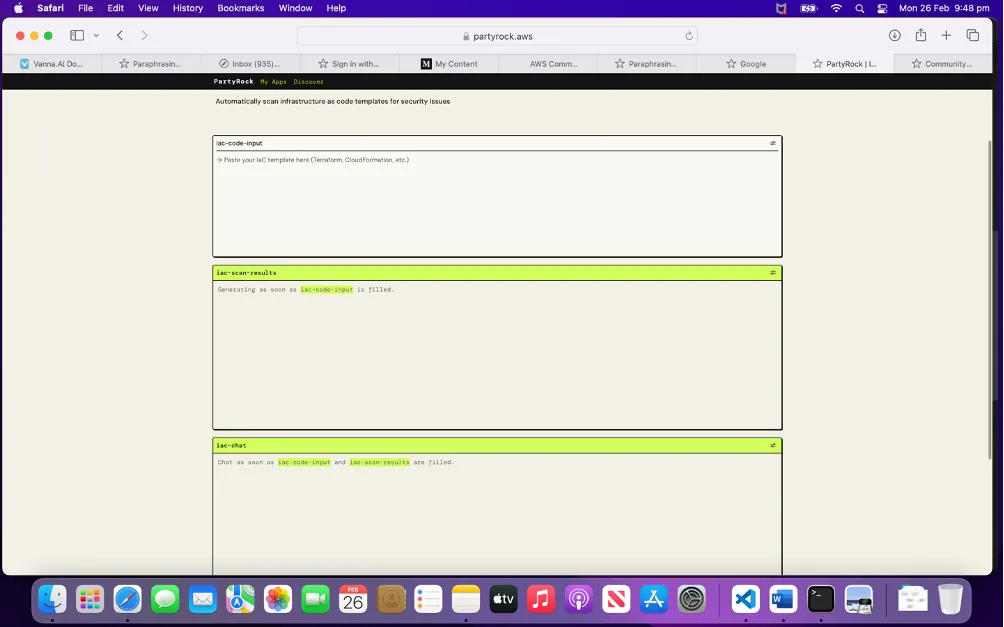
Generated App
Test the app with sample Terraform code
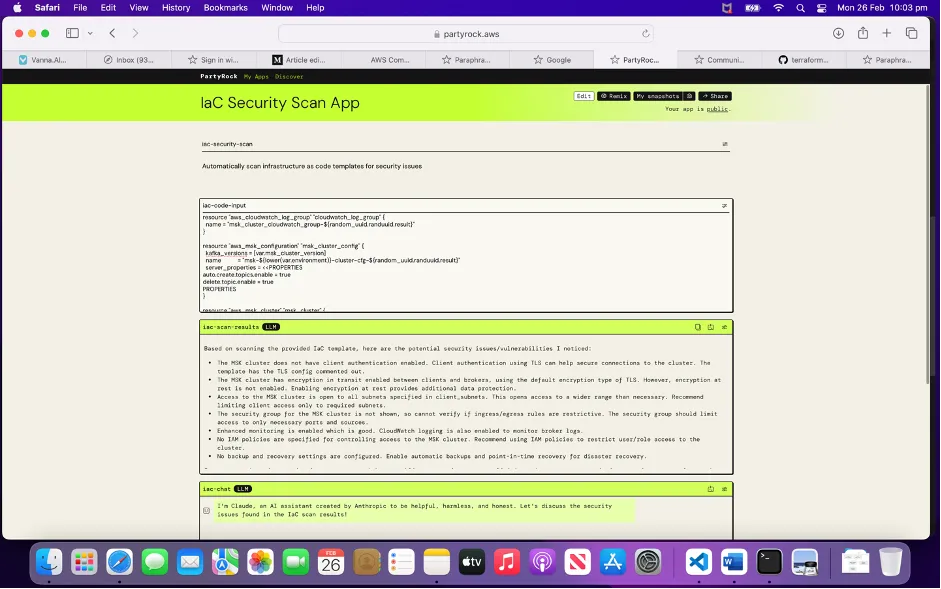
Published App : https://partyrock.aws/u/selvapal/UI-aMM_I3/IaC-Security-Scan-App
Sample code used for testing
