Integrate external AWS accounts into AWS IAM Identity Center for central access management with independent billing using SAML 2.0
Centralize access management of multiple AWS accounts without merging billing consolidation
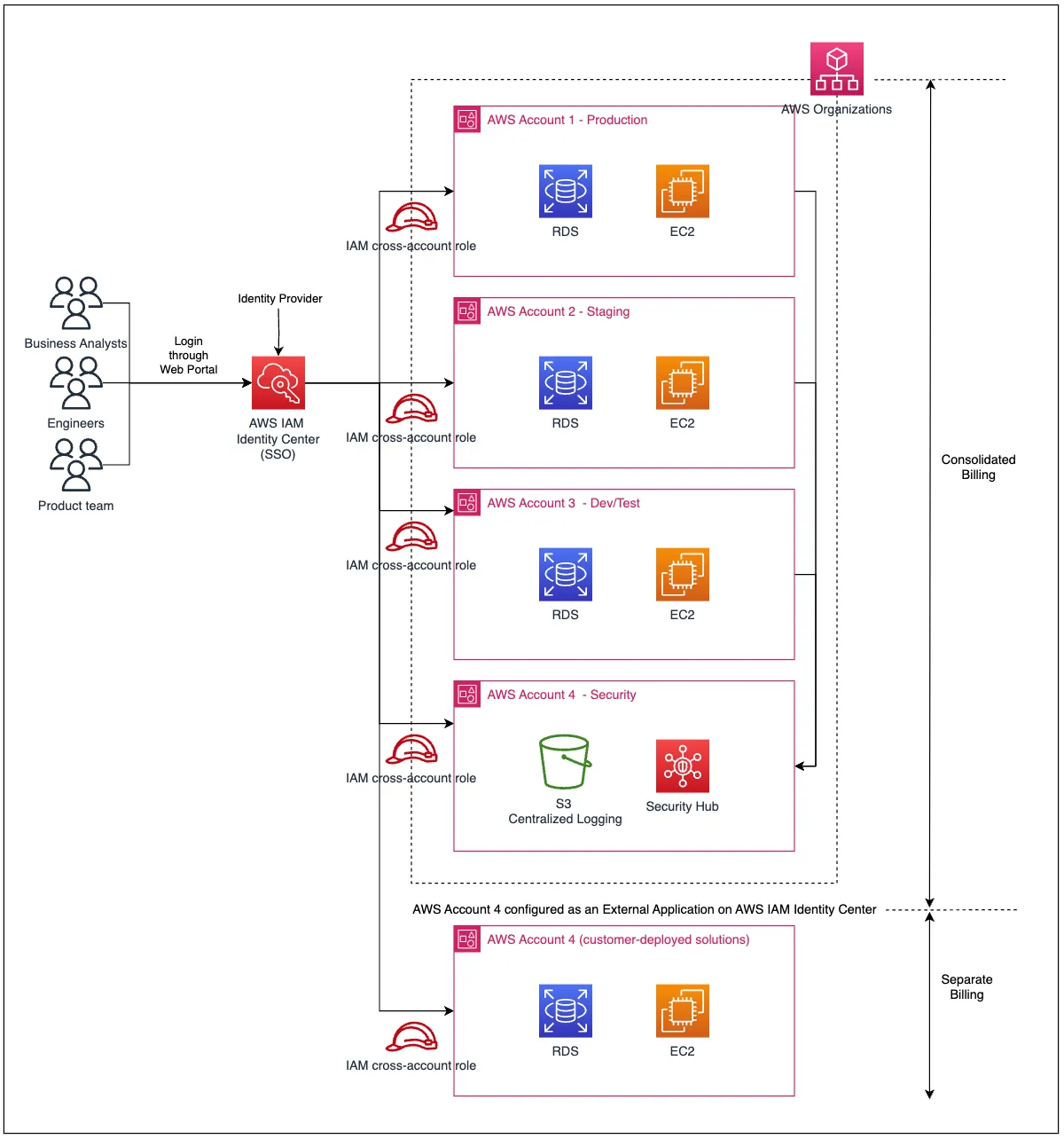
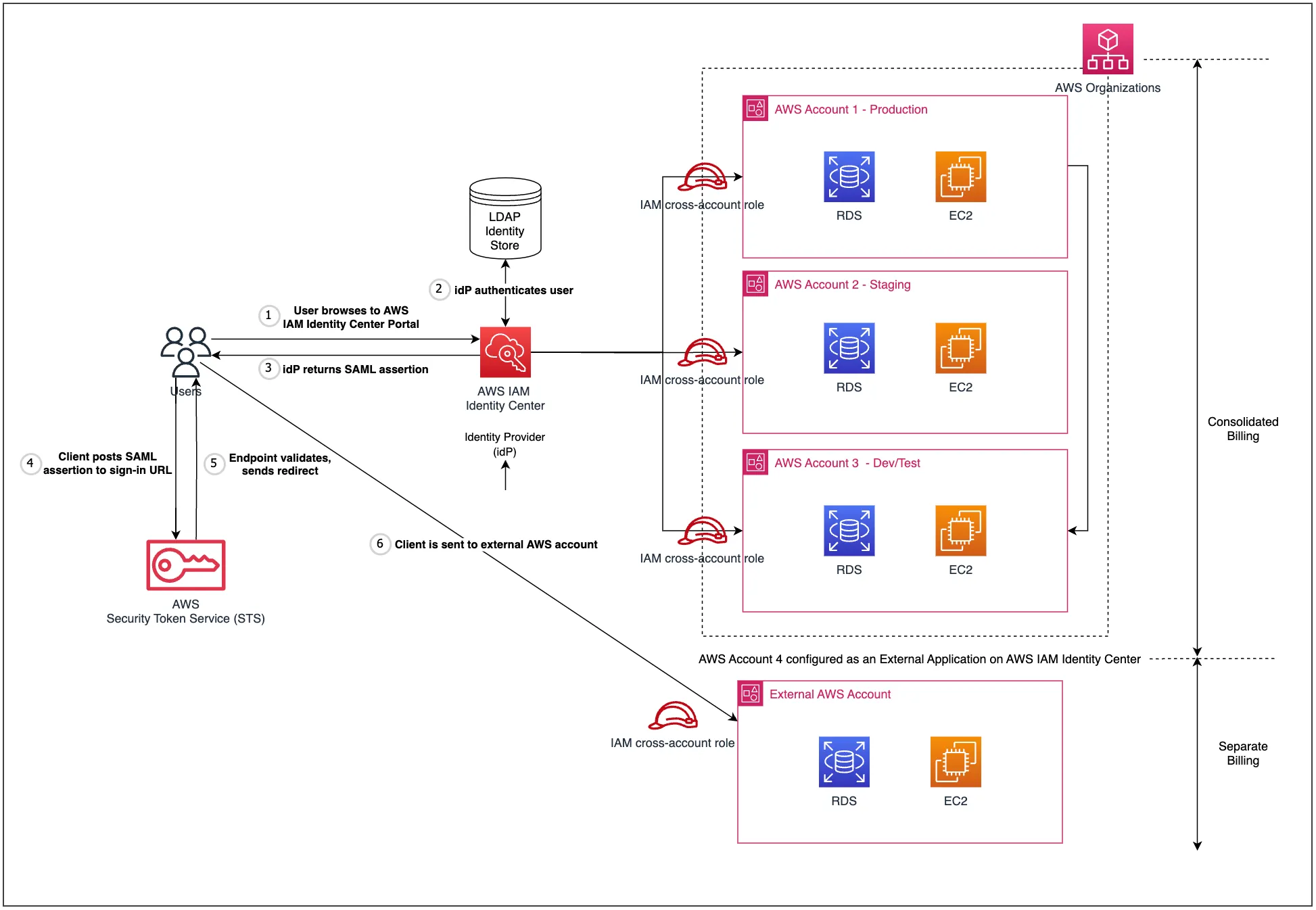
The architecture diagram in Figure 1 showcases the solution set-up of the integration. By configuring IAM identity center to integrate an external AWS account using SAML, you can manage sign-in security for the external account using the same Identity Provider and SSO mechanism implemented for the AWS organization. This allows multiple separate AWS entities (multiple AWS external accounts can be integrated in the same way) to enjoy central access management with a single identity mechanism.
- Step 1: Add the external AWS account as an application to AWS Identity Center in primary account
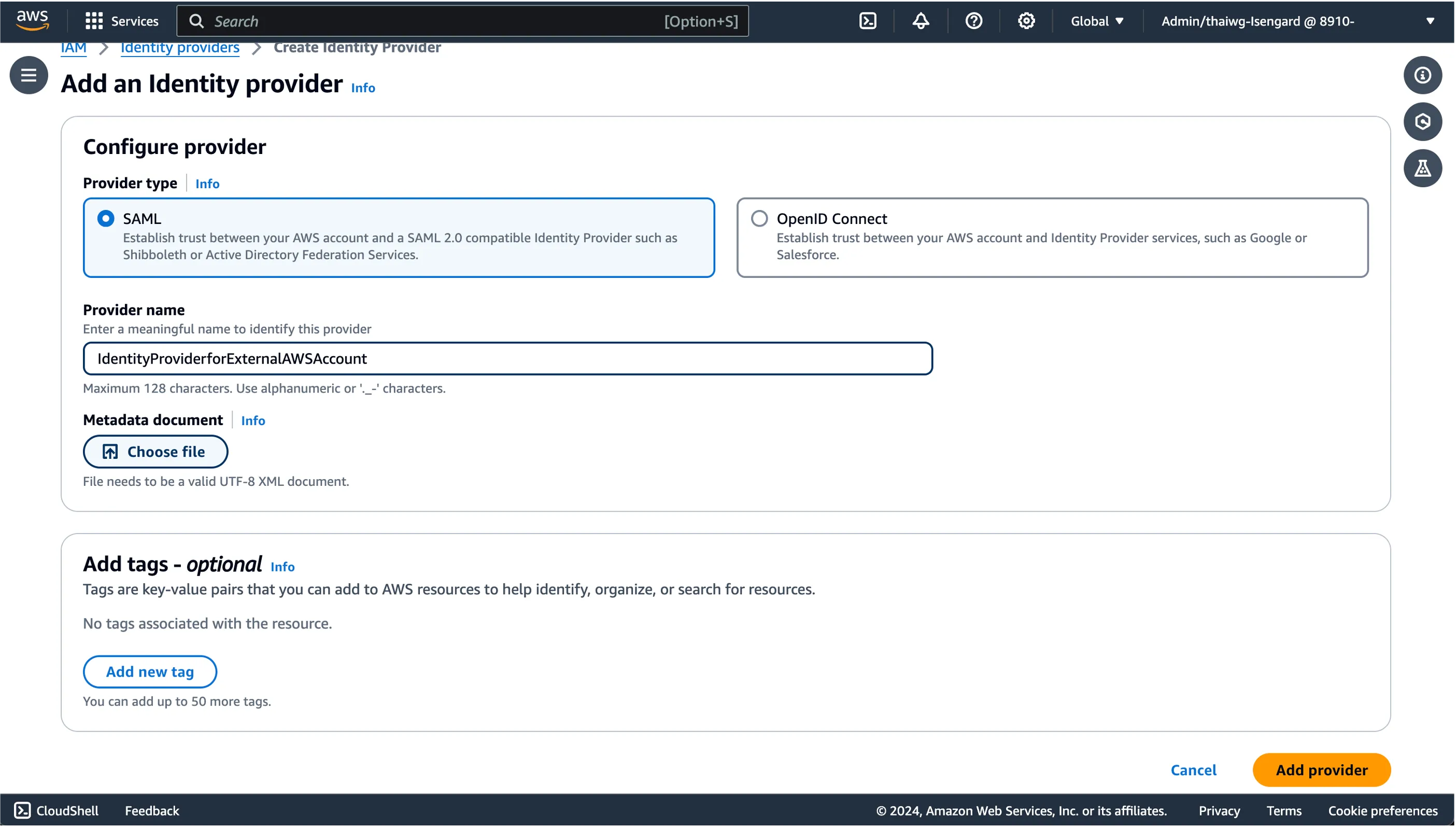
- Step 2: Create a SAML Identity Provider in external AWS account
- Step 3: Create an IAM Policy in external AWS account
- Step 4: Create an IAM role for SAML Federation in external AWS account
- Step 5: Configure access details of created IAM role in the IAM Identity Center of primary account
- Step 6: Verify the SSO integration
- Access to the primary AWS account’s IAM Identity Center console with permissions to manage applications.
- An external AWS Account outside your Organization with admin permissions for AWS IAM.
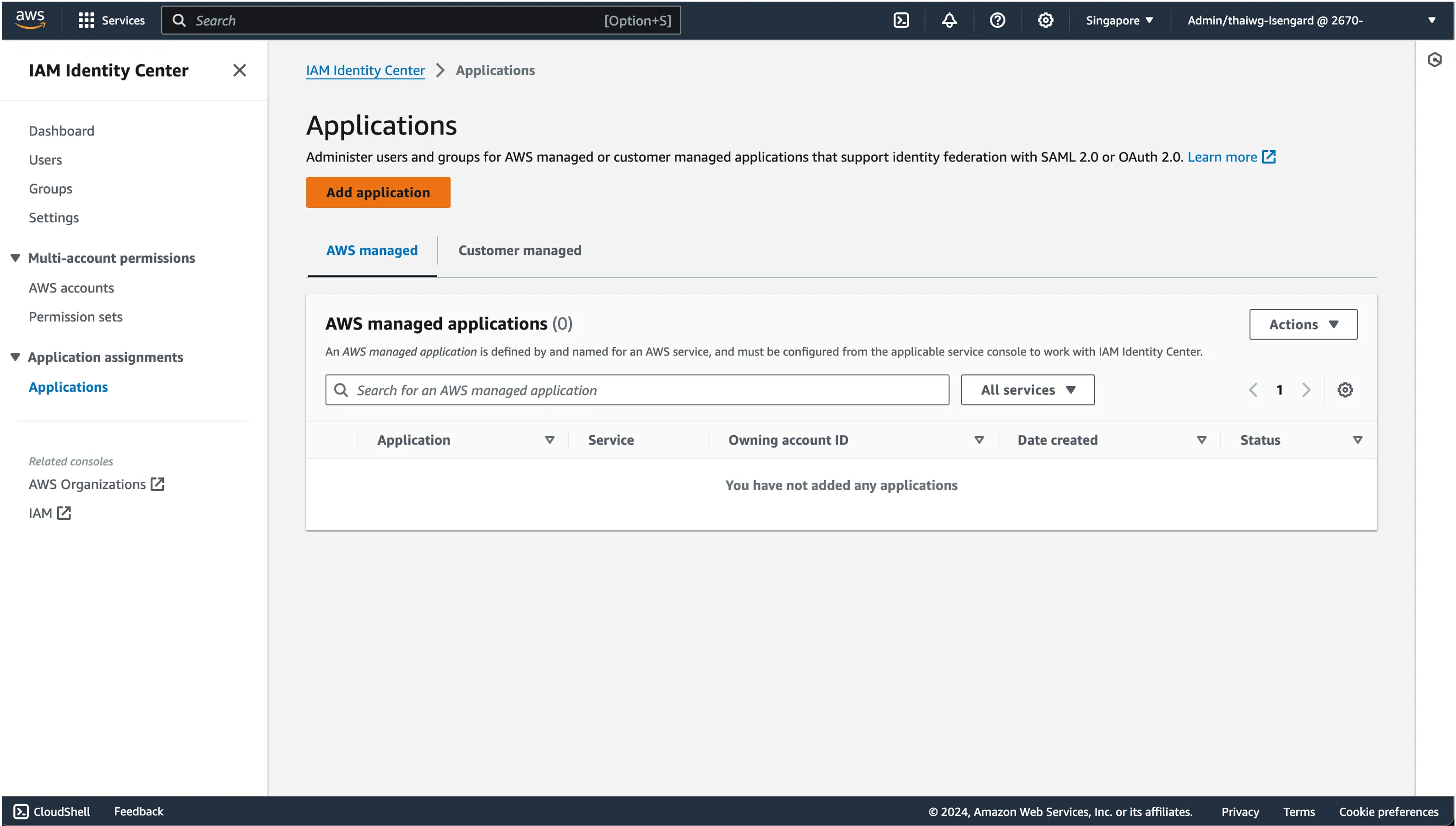
Select “I want to select an application from the catalog”.
In the search bar, type "External AWS Account". Select it and click Next.
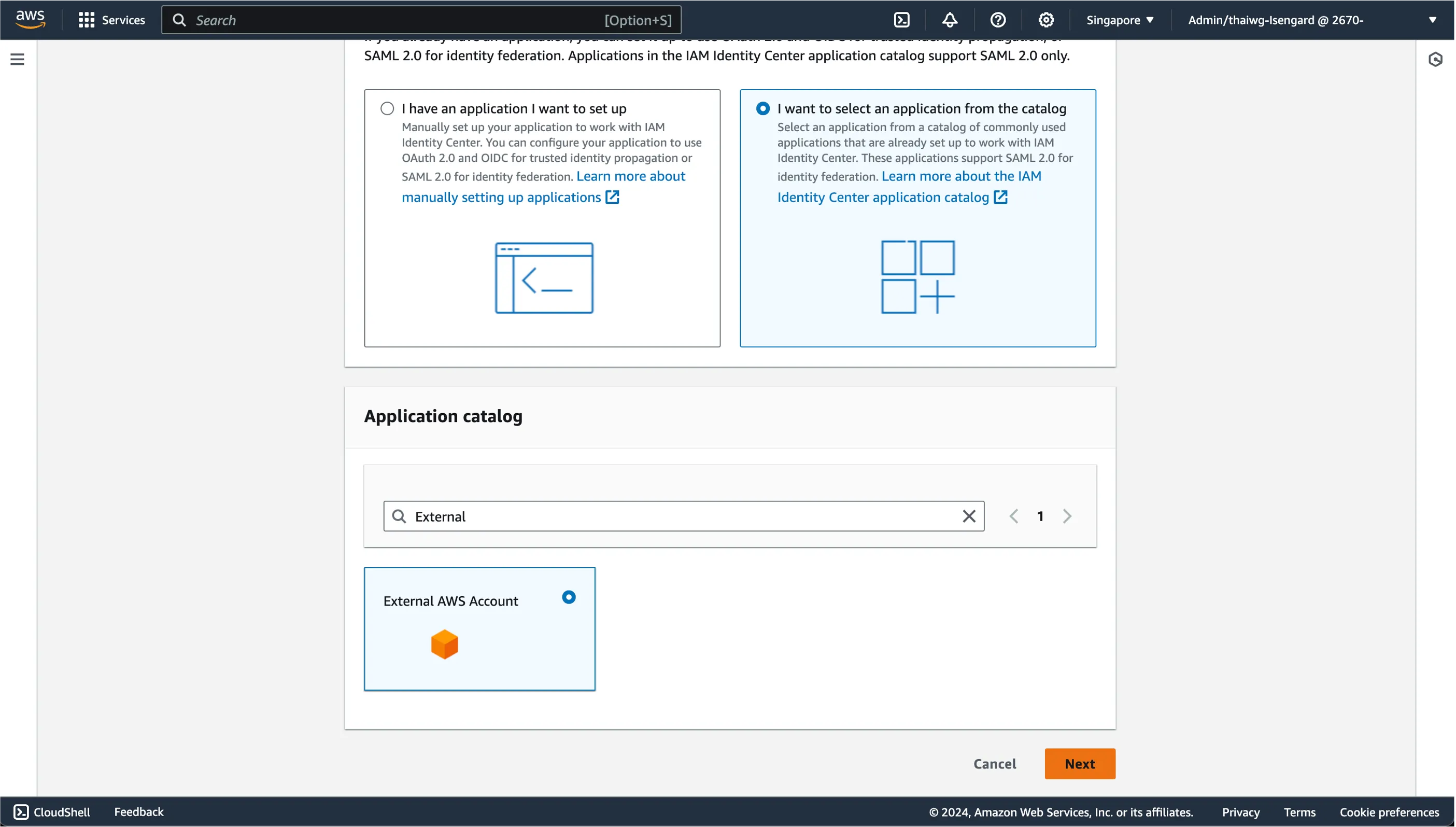
In the next page, Provide a Display name to identify the external AWS account and a proper description associated with it.
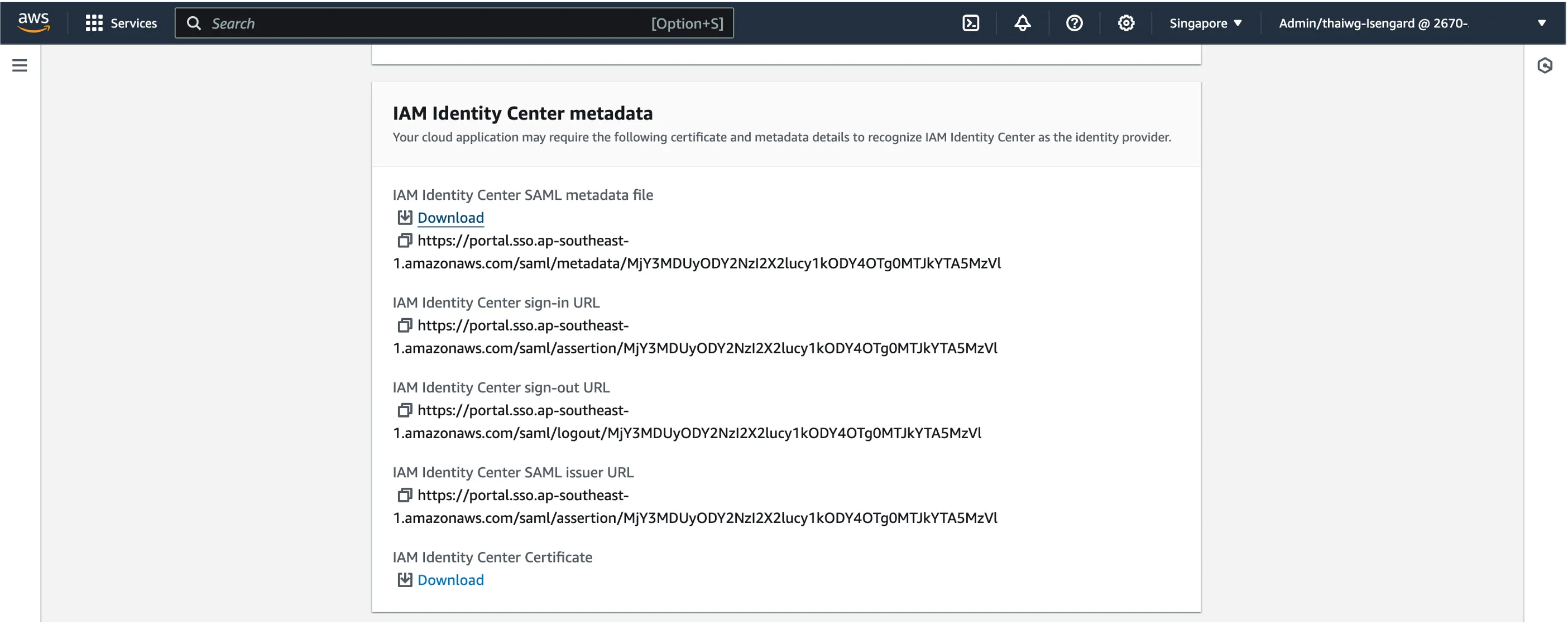
Scroll down to IAM Identity Center meta data and download the IAM Identity Center SAML metadata.
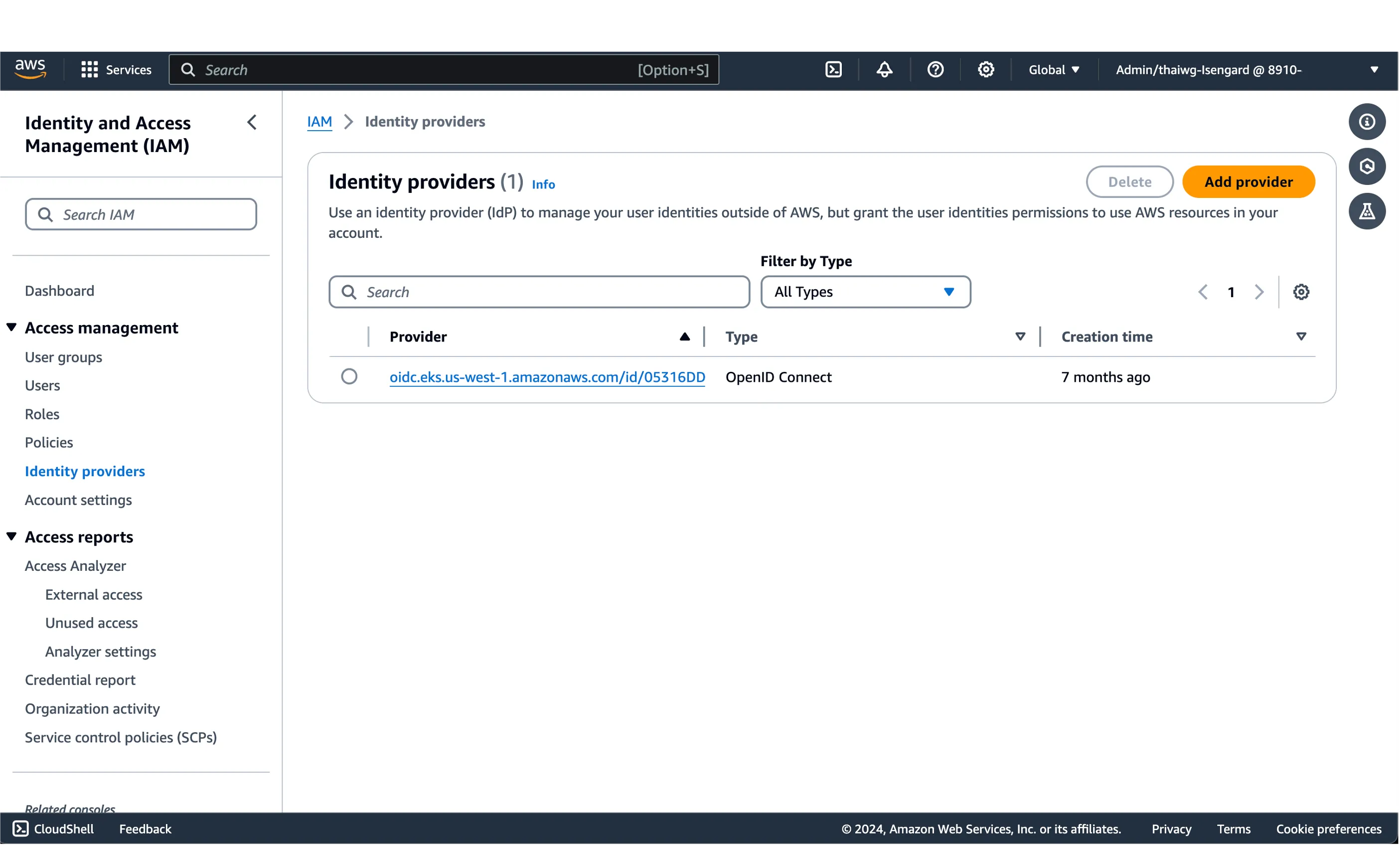
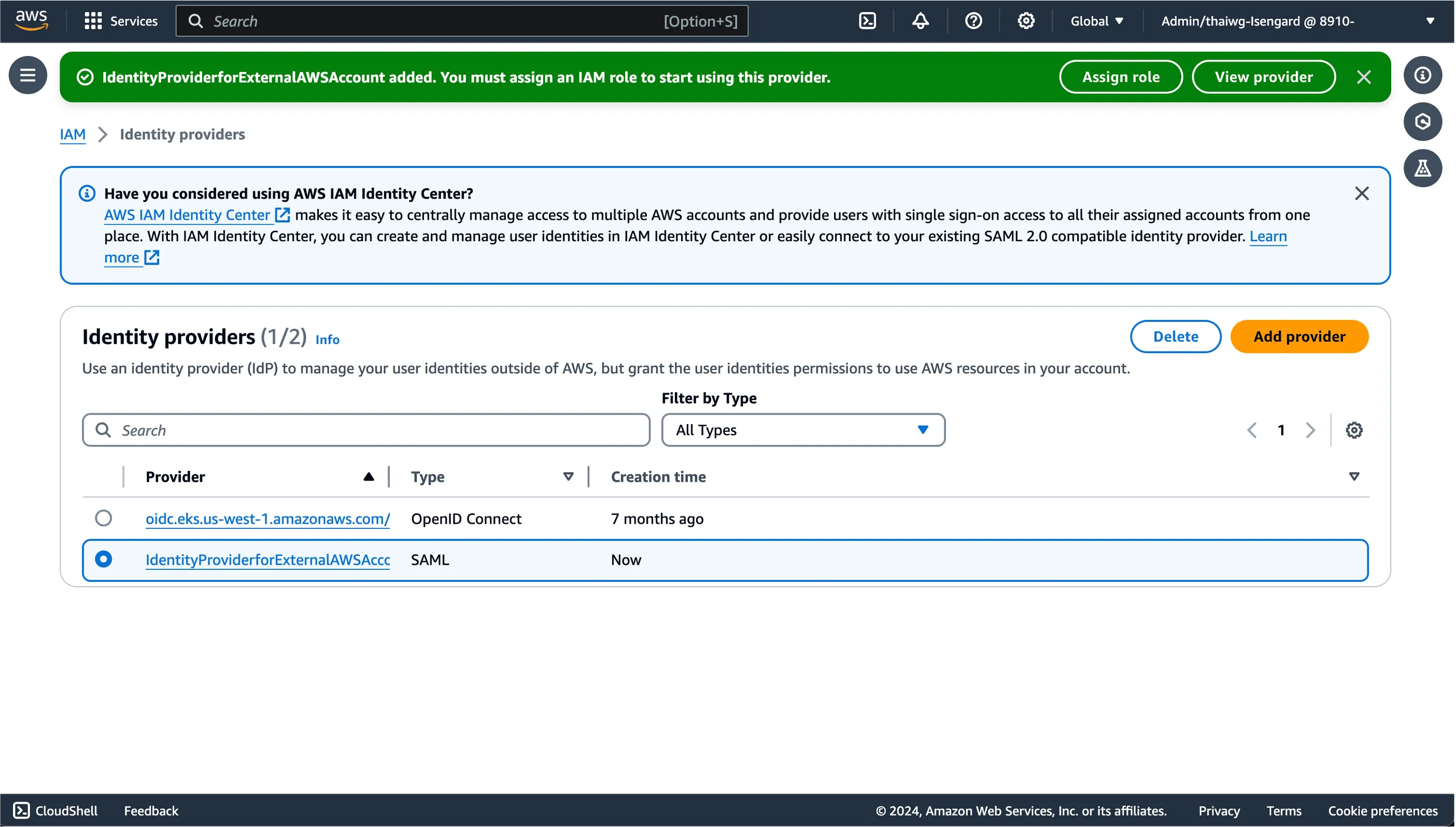
You should see your newly created SAML Identity Provider show up on your IAM dashboard.
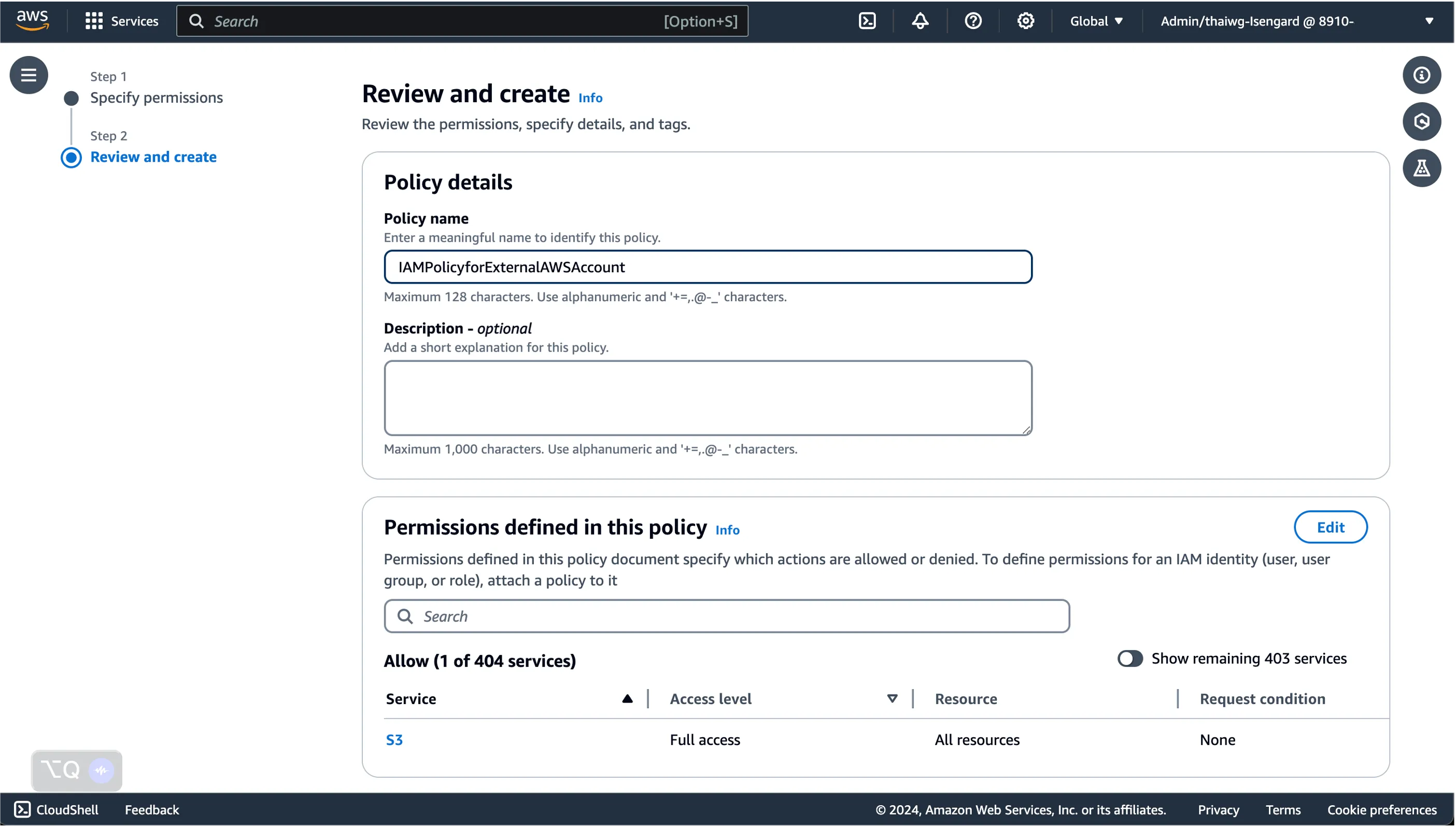
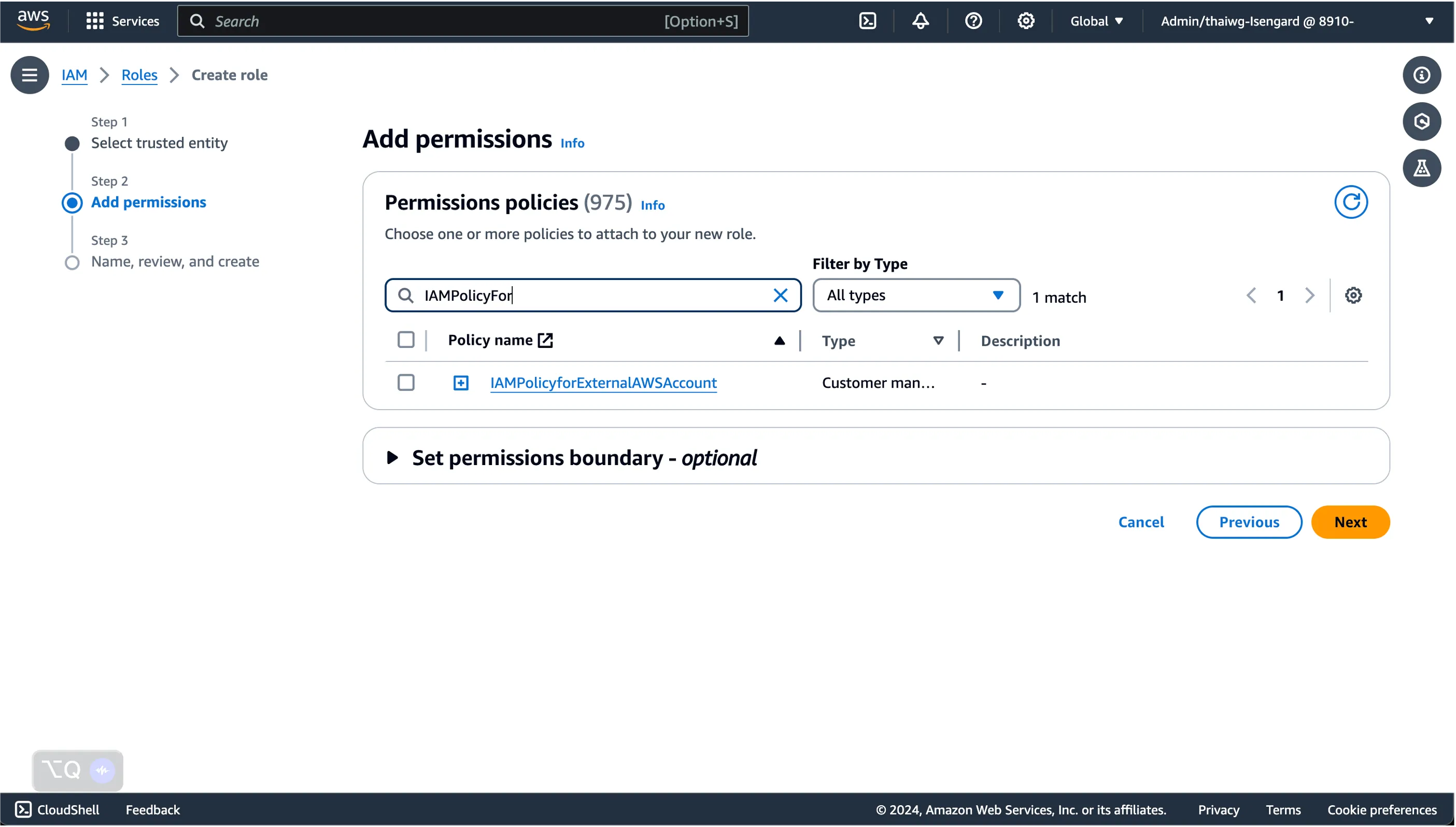
Here, we can start defining fine-grained permissions to resources we want to grant to users accessing this external AWS account from our primary AWS account.
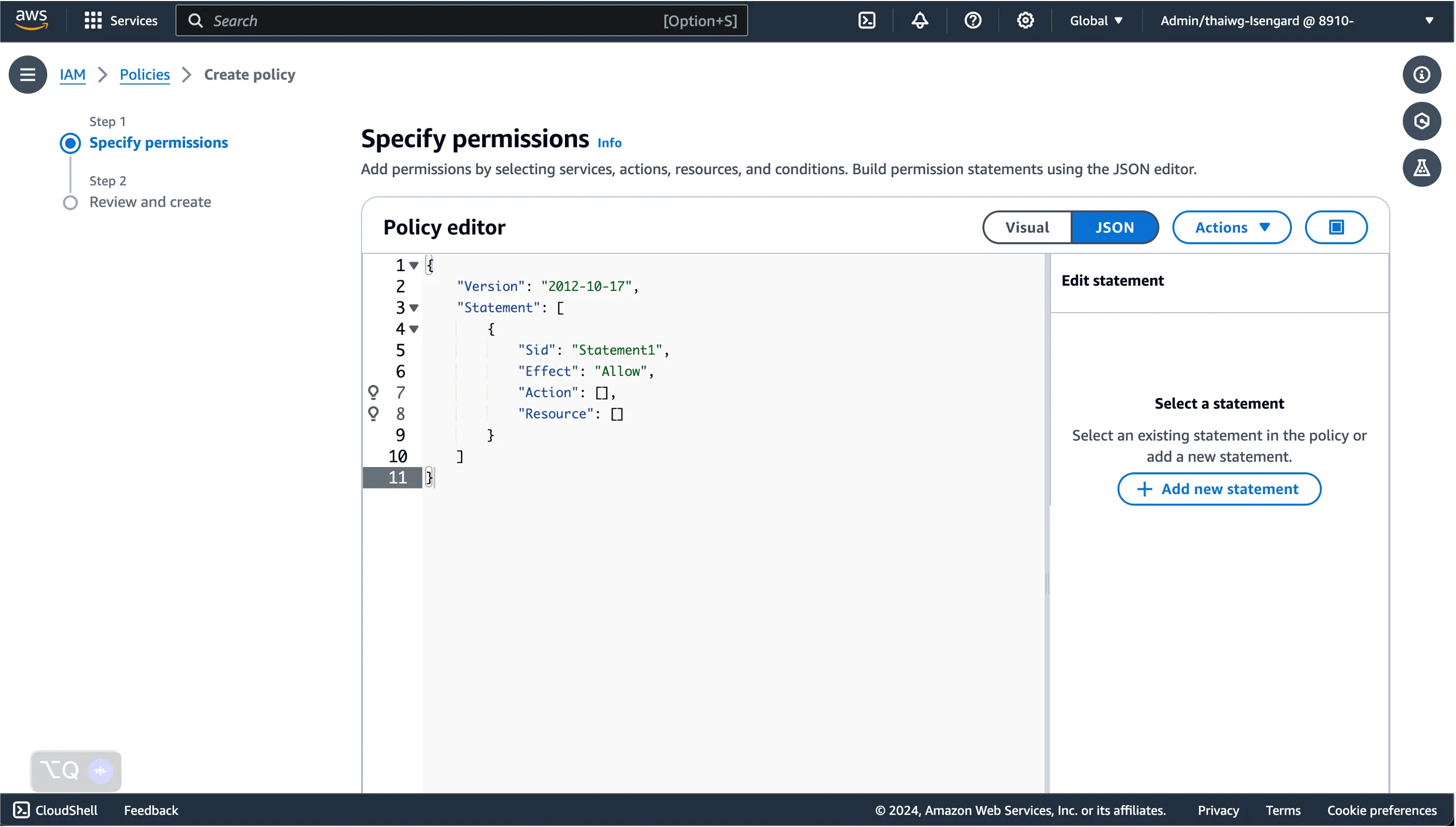
Once done, click Next, and provide a name for the policy so we can identify it later.
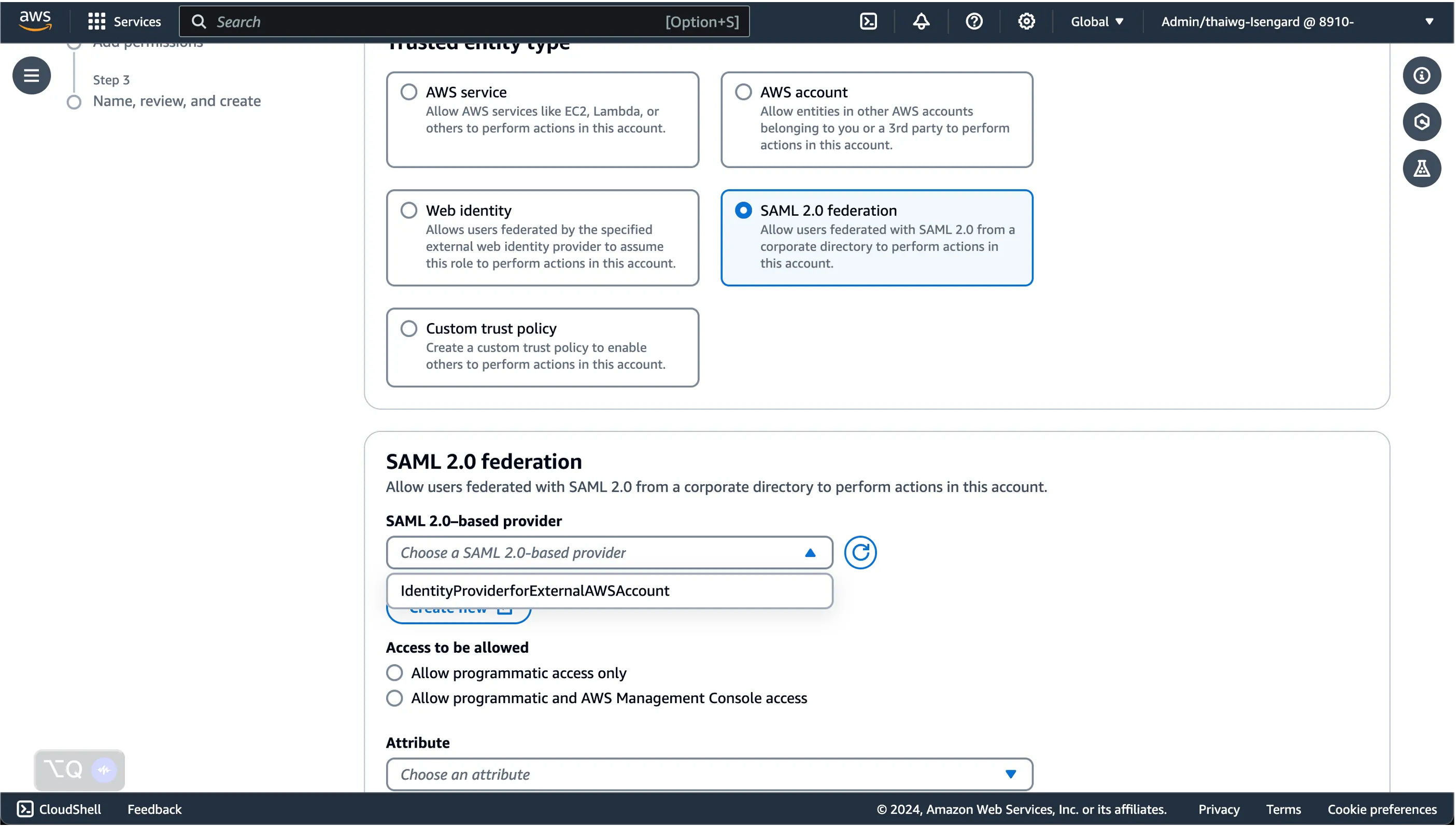
Here, select SAML 2.0 federation as the Trusted entity type, and choose the SAML Identity Provider we created from the step before.
Following which, determine whether you would like to provide access to the AWS Management Console through this role, or only programmatic access by selecting the associated option.
Finally, provide the IAM role with an appropriate name for us to identify it later.
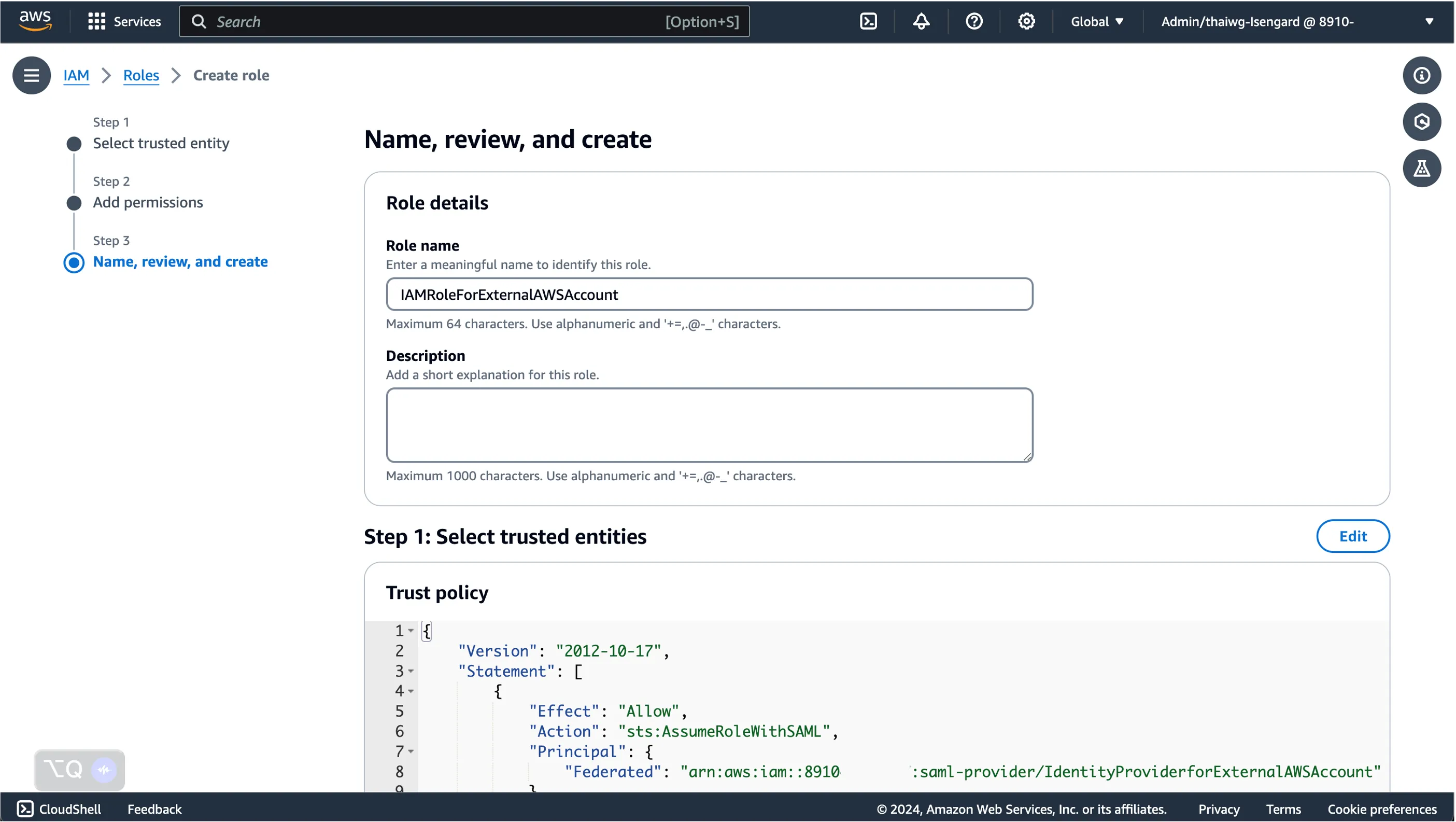
Here is where we will provide details of our SAML Identity Provider and IAM Role of our external AWS account to allow the SAML Federation to work.
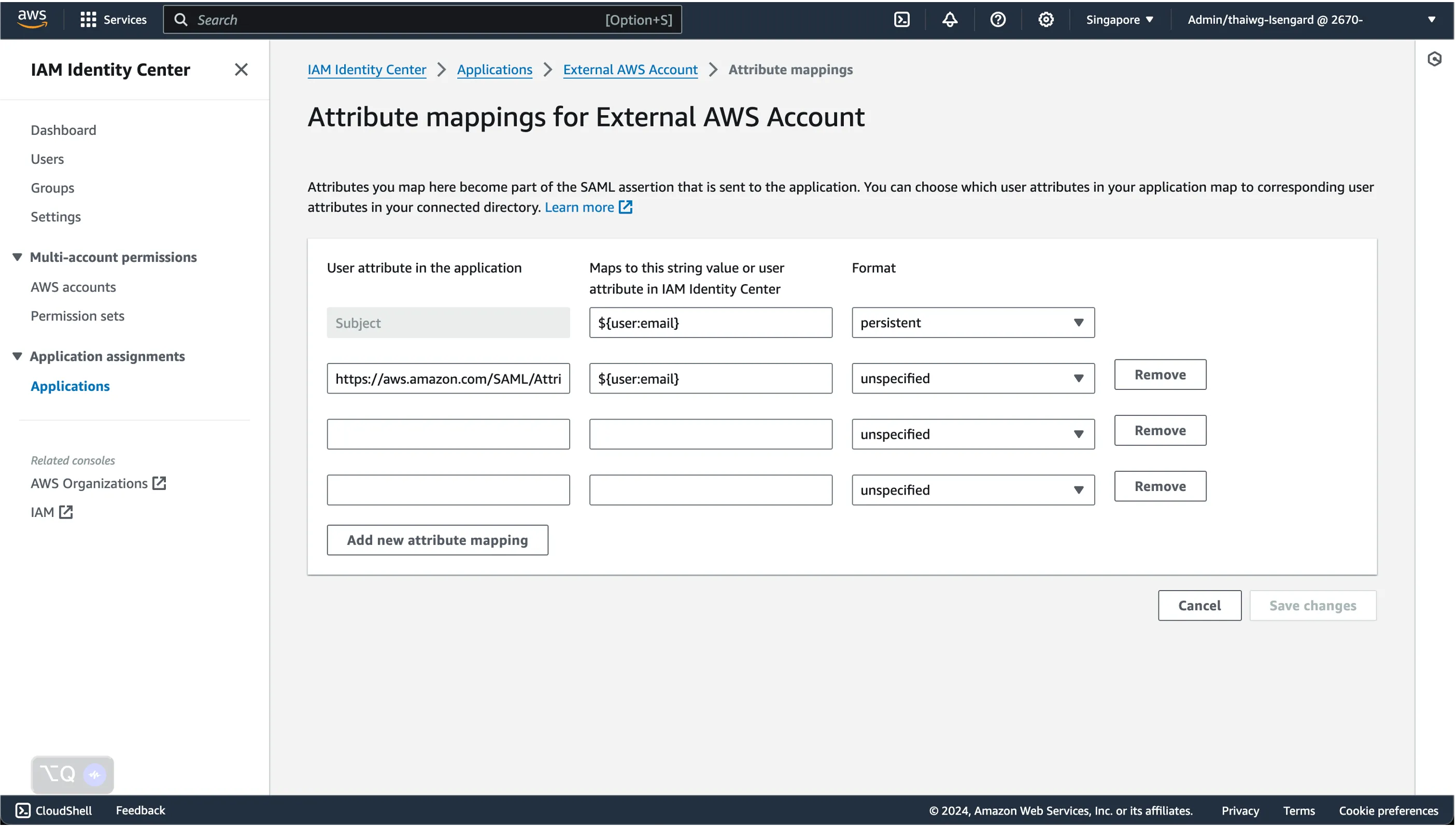
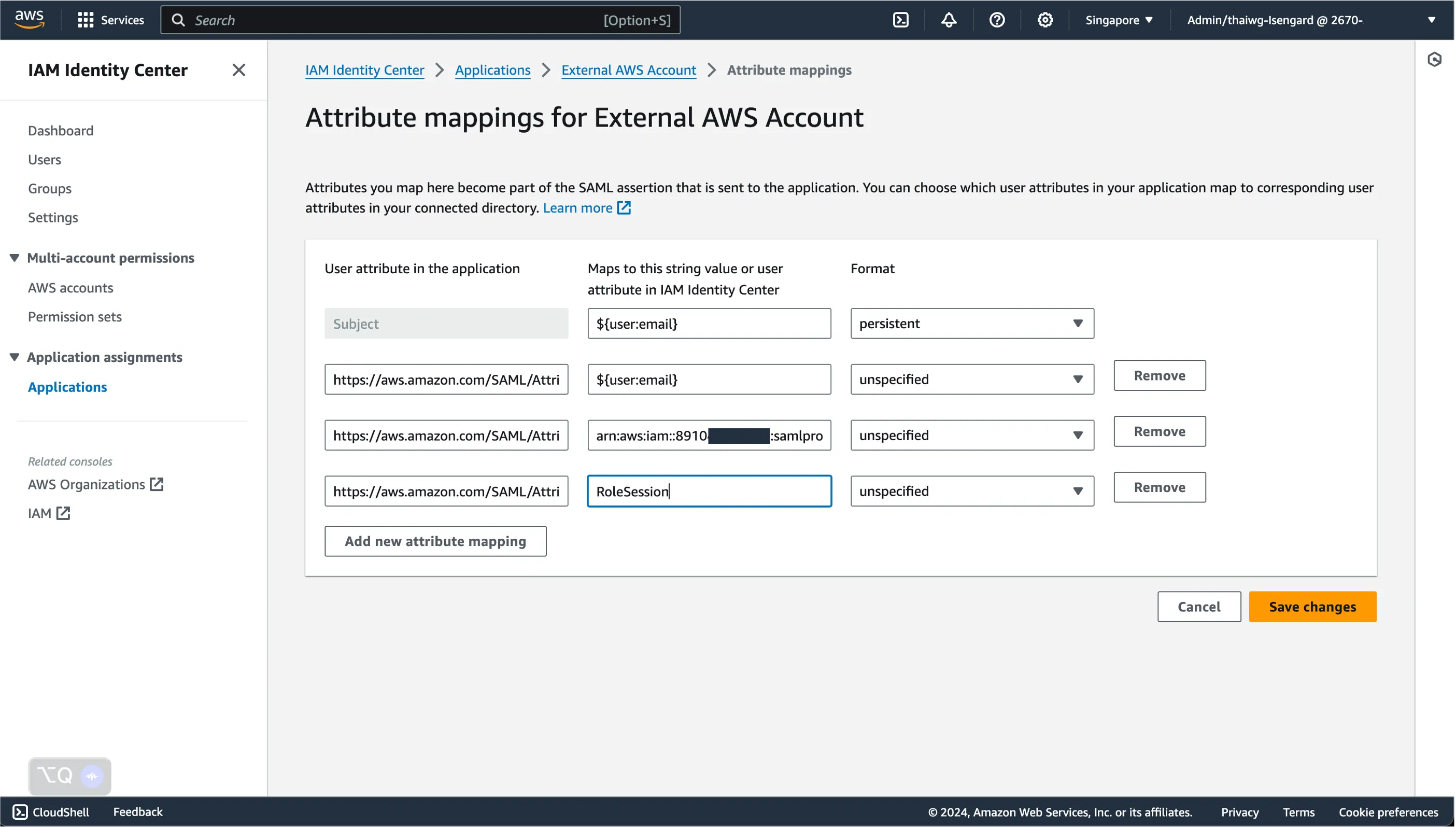
Fill in the 2 new attribute mappings with the following details - replace the values of the following parameters:
- ACCOUNTID is the AWS Account ID of the external AWS account
- SAMLPROVIDERNAME is the name of the SAML Identity Provider created in the external AWS account
- ROLENAME is the name of the IAM Role created in the external AWS account
| https://aws.amazon.com/SAML/Attributes/Role | arn:aws:iam::ACCOUNTID:saml-provider/SAMLPROVIDERNAME,arn:aws:iam::ACCOUNTID:role/ROLENAME | unspecified |
|---|---|---|
| https://aws.amazon.com/SAML/Attributes/RoleSessionName | <ROLE_SESSION_NAME> must match [a-zA-Z_0-9+=,.@-]{2,64} | unspecified |
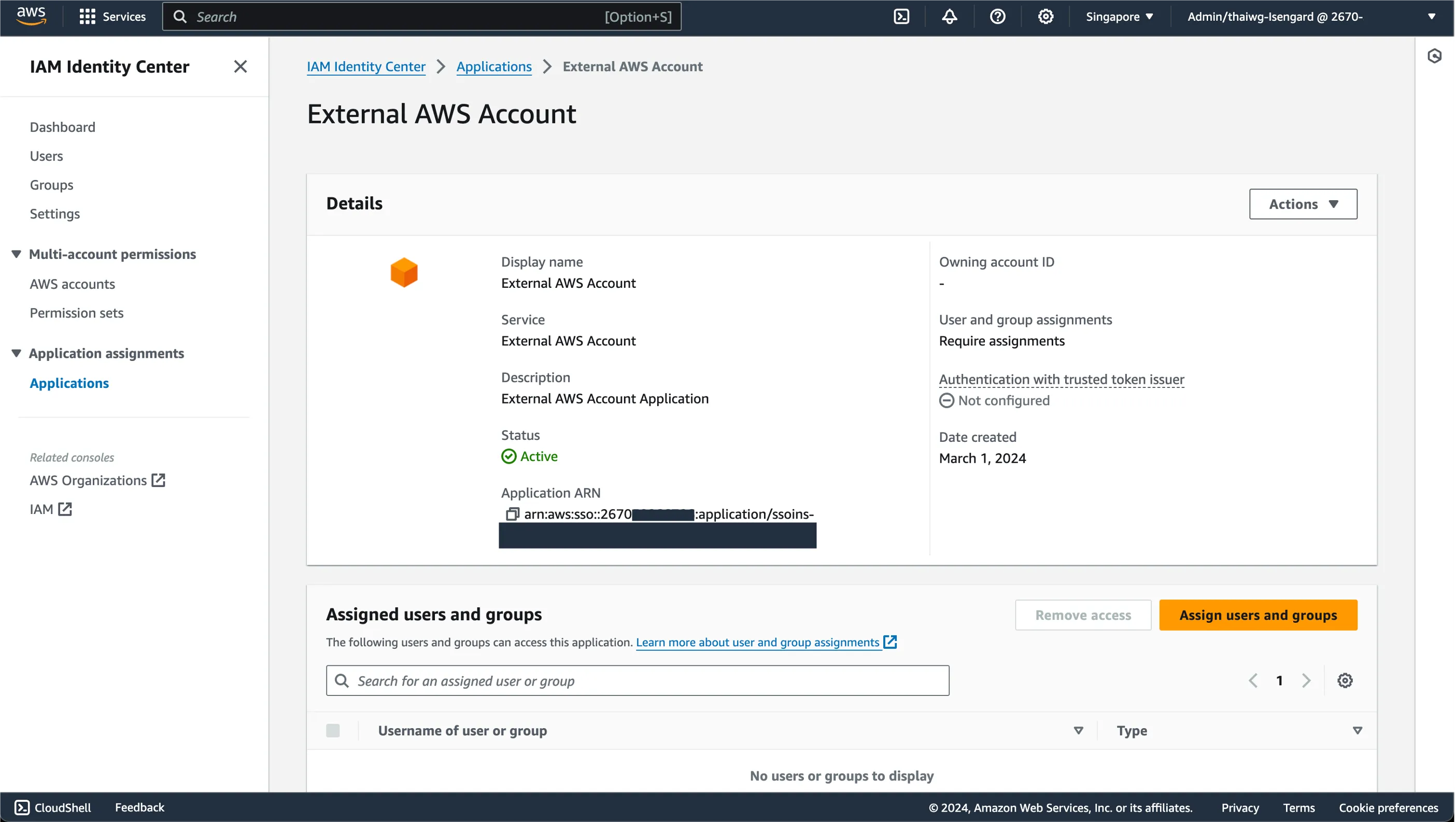
Now that we have the integration configured, we will assign this access to specific users or groups in our IAM Identity Center.
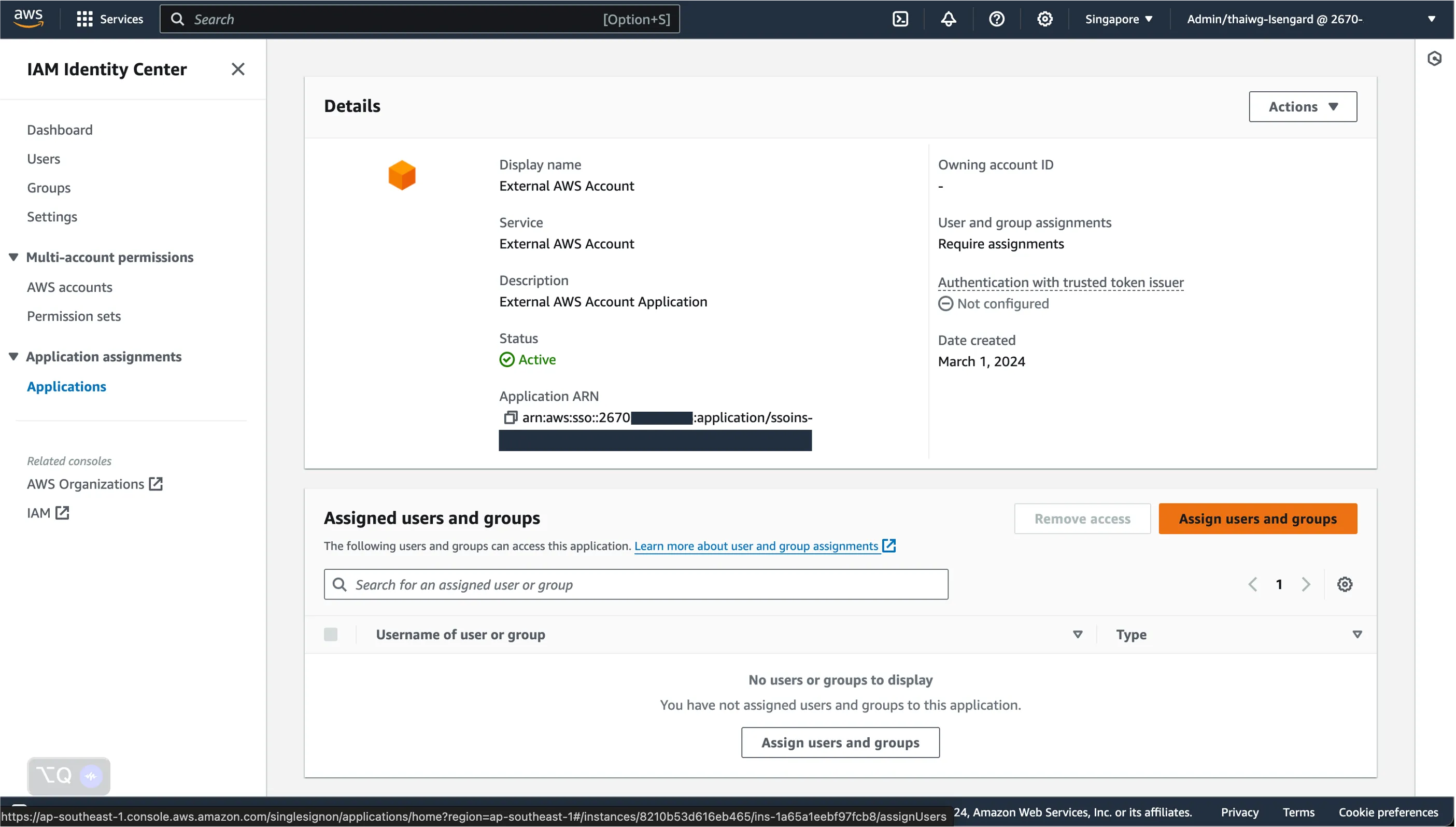
Depending on your set-up and use-case, assign individual users and / or groups you want to allow access to this External AWS account.
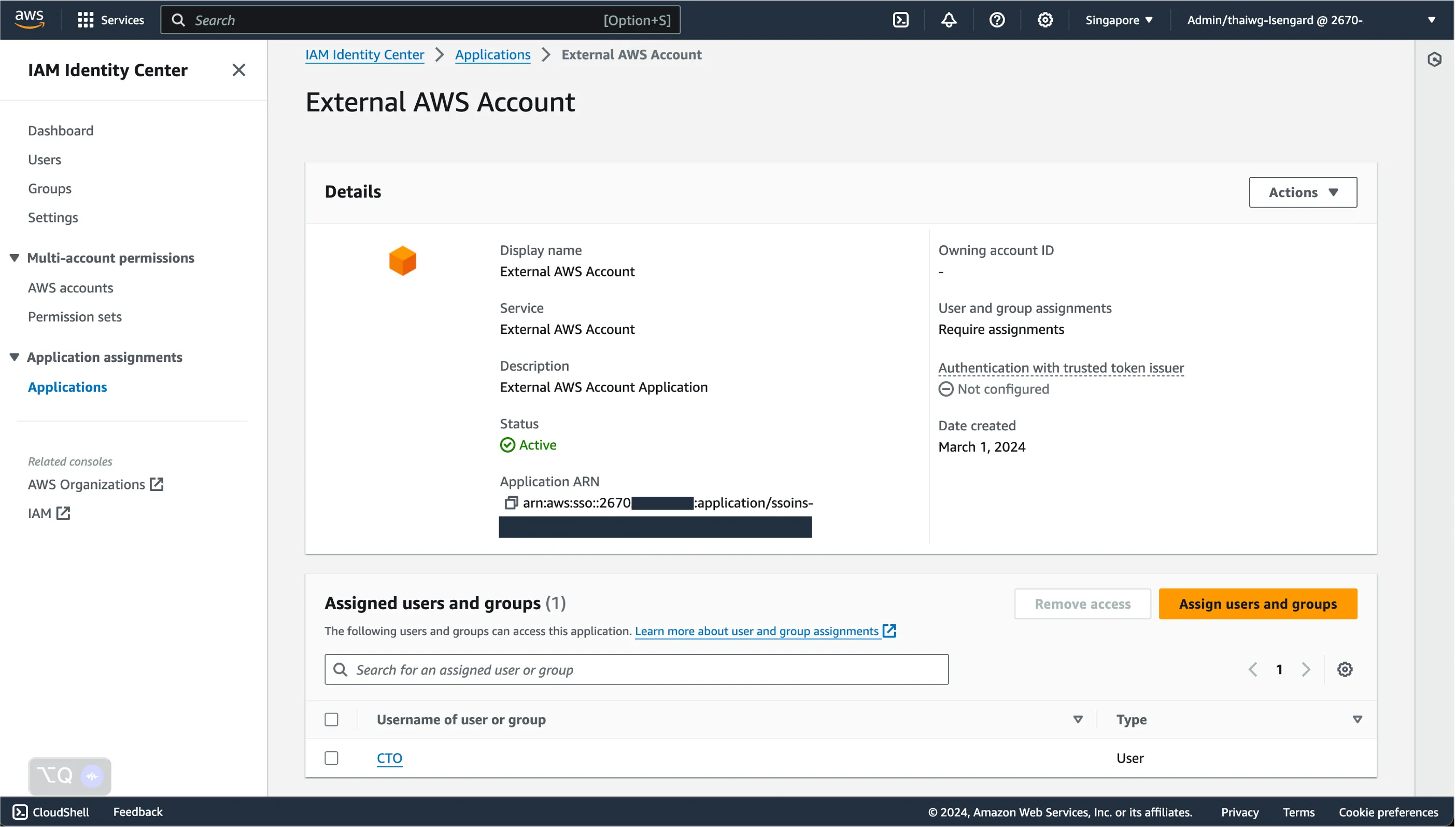
You should be able to see the name of the external AWS account show up as a separate application on your access portal.
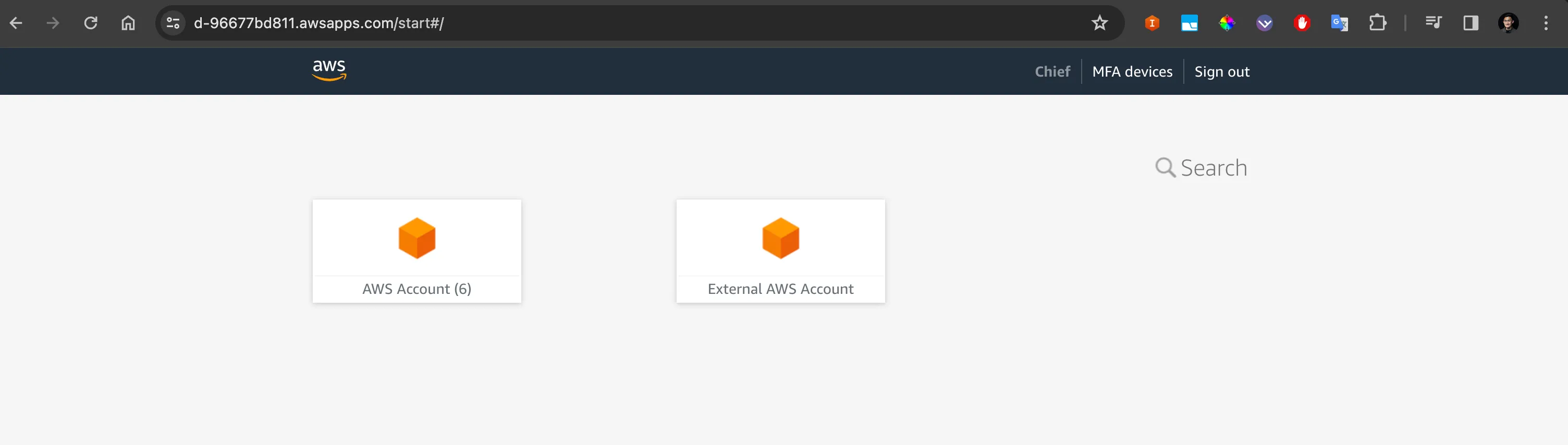
Click on it, and you will now be directed to the External AWS account.
And...there we have it!
SAML, which stands for Security Assertion Markup Language, is a standardized protocol used for exchanging authentication and authorization data between identity providers (IdPs) and service providers (SPs). Essentially, it's a set of rules and formats that allow different systems to communicate securely about who you are and what you're allowed to do.
When integrating an external AWS account into an existing IAM Identity setup, SAML assertions hands over crucial authentication and authorization data between IdPs and SPs.
Here's how it works:
- User Authentication: When a user attempts to access the external AWS account or its resources, they are redirected to the primary AWS account’s IAM system for authentication. This authentication mechanism is carried out using the same IdP configured within the primary AWS account’s IAM Identity Center set-up.
- Generation of SAML Assertion: Upon successful authentication, the IAM system generates a SAML assertion (remember - a digitally signed XML document) containing information about the user's identity and permissions.
- Transmission to external AWS account: This SAML assertion is then securely transmitted to the external AWS account environment, where the AWS Security Token Service (STS) validates the assertion's authenticity and extracts the user's identity and attributes.
- Authorization: Based on the information in the SAML assertion, AWS determines the user's access rights and permissions within the external AWS account.
- Access Granted: If everything checks out, the user is granted access to the requested AWS resources, with their permissions managed according to the IAM policies configured for the external account. This is the same process when a user assumes an IAM role to access resources within a single AWS account.
Any opinions in this post are those of the individual author and may not reflect the opinions of AWS.
