Fortifying IAM Practices: Progamatic Approaches to AWS IAM User Detail Retrieval
We can retrieve comprehensive user data, including creation timestamps, which can be achieved using either AWS CLI commands or through the AWS Management Console's graphical user interface (GUI). Additionally, we can access specific user details such as attached policies and authorization levels through these methods. However, when the need arises for auditing purposes to gather all users' attached policies, programming becomes the preferred and more efficient approach for obtaining this information.
Published Mar 16, 2024
AWS Identity and Access Management (IAM) is a AWS service that helps you securely control access to AWS resources. It enables you to manage users, groups, roles, and permissions to ensure that only authorized individuals or systems can interact with your AWS infrastructure.
- Security: IAM allows you to implement the principle of least privilege by granting only the necessary permissions to users, groups, or roles.
- Compliance: IAM helps organizations meet regulatory compliance requirements by enforcing access controls and auditing access to resources.
- Centralized Management: IAM provides a centralized platform for managing access to AWS resources across multiple users, applications, and services.
- Granular Control: IAM offers granular control over permissions, allowing you to define fine-grained policies to restrict or allow access to specific resources and actions.
- Integration: IAM seamlessly integrates with other AWS services, enabling you to control access to various AWS resources and services.
- Multi-User Environments: Use IAM in environments with multiple users, such as organizations, teams, or projects, to manage access to AWS resources securely.
- Role-Based Access Control (RBAC): Implement IAM for role-based access control, allowing you to assign permissions to roles rather than individual users, simplifying access management.
- Resource Isolation: Use IAM to isolate and protect resources by restricting access based on user roles, groups, or policies.
- Secure Application Access: Utilize IAM to control access to AWS resources for applications running on EC2 instances, Lambda functions, or other services, ensuring secure application interactions.
- Compliance and Auditing: Use IAM to enforce access controls, monitor user activity, and generate audit logs to demonstrate compliance with regulatory requirements.
- Least Privilege: Follow the principle of least privilege when designing IAM policies, granting users or roles only the permissions they need to perform their tasks.
- Security Best Practices: Implement security best practices, such as enabling multi-factor authentication (MFA), rotating access keys regularly, and using IAM roles for cross-account access.
- Policy Management: Regularly review and update IAM policies to align with changing security requirements and organizational needs.
- Monitoring and Logging: Enable AWS CloudTrail to capture API activity and AWS Config to monitor resource configurations, helping you track changes and detect unauthorized access attempts.
We will use a Python script utilizes the boto3 library to interact with the AWS Identity and Access Management (IAM) service. It retrieves account authorization details, including information about users and their attached managed policies. The script loops through each user and prints their details, including username, user ID, policy names, and policy ARNs.
- Install Boto3: Ensure that the boto3 library is installed. You can install it using pip or pip3 as per your enviorment - pip3 install boto3
- Configure AWS Credentials: Before running the script, configure your AWS credentials. You can set up credentials using the AWS CLI or by setting environment variables.
- Run the Script: Execute the Python script on your local machine using a Python interpreter: python <script_name>.py
You will get similar output as per your enviorment
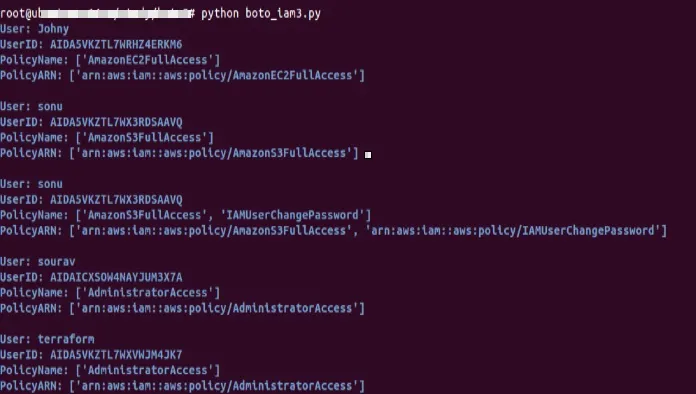
Before running the script , consider the below points
- No Error Handling: The script uses a generic
exceptblock to catch exceptions. This approach can hide potential errors and make troubleshooting difficult. It's recommended to handle specific exceptions separately for better error management. - No Authentication Validation: The script assumes that valid AWS credentials are configured on the local machine. However, it does not validate the authentication status or check for potential credential issues. Implementing proper authentication validation can enhance security.
- Insecure Credential Management: Storing AWS credentials directly in code or environment variables can pose security risks, especially if shared or exposed inadvertently. It's recommended to use secure credential management practices, such as AWS IAM roles or AWS Secrets Manager, to mitigate these risks.
- Potential Information Leakage: Printing detailed user information, including usernames and policy details, to the console may expose sensitive data. Ensure that the script's output is handled securely, especially in production environments, to prevent unauthorized access to sensitive information.
AWS IAM is a critical service for managing access to AWS resources securely, providing granular control over permissions, centralized management, and compliance enforcement. By understanding when and why to use AWS IAM, organizations can enhance their security posture, streamline access management, and maintain regulatory compliance and maintain audit data ready.
