Ideal Cloud Security - Your Security Means "Guardrail" or "Restriction"?
We have to clearly distinguish and utilize them accordingly.
Published Mar 24, 2024
I have worked in cybersecurity, especially cloud security, and I eventually got an understanding of essential security postures.
In my opinion, the general cloud security configurations can be classified into two components.
One is the "Guardrail" and the other is "Restriction".
Let's consider the specifics, taking AWS security as an example.
Many AWS account users are familiar with the IAM best practice of applying the principle of least privilege.
To grant only the permissions required to perform a task, you can generate policies based on your access activity that is logged in AWS CloudTrail. IAM Access Analyzer analyzes the services and actions that your IAM roles use, and then generates a fine-grained policy that you can use. After you test each generated policy, you can deploy the policy to your production environment. This ensures that you grant only the required permissions to your workloads. For more information about policy generation, see IAM Access Analyzer policy generation.
This means granting restricted permissions when issuing IAM users or IAM roles to mitigate the effects of credential leakage. In various working environments, the principle should be adapted and potentially effective. For instance, it can prevent misconfigurations, such as unintended public settings for S3 buckets.
However, the prerequisite of the minimum permission requires the strictly secure management of admin users and roles. (Note: Using IAM roles is more recommended for administration operations)
The principle's purpose is to mitigate an unfortunate scenario. So, IAM roles with strong permissions are needed for daily operations and are essential identities. As you know, they cannot be deleted. Thus, we can't abandon the management of all IAMs, and specific IAMs with minimum permissions are just like security guardrails.
The guardrail always helps junior-tier engineers, but it's different from improving of the whole security posture.
So, how can we achieve ultimate security?
The key is understanding the policy evaluation logic, in other words, the priority of permissions. I believe the picture below represents the most critical concept of AWS security.
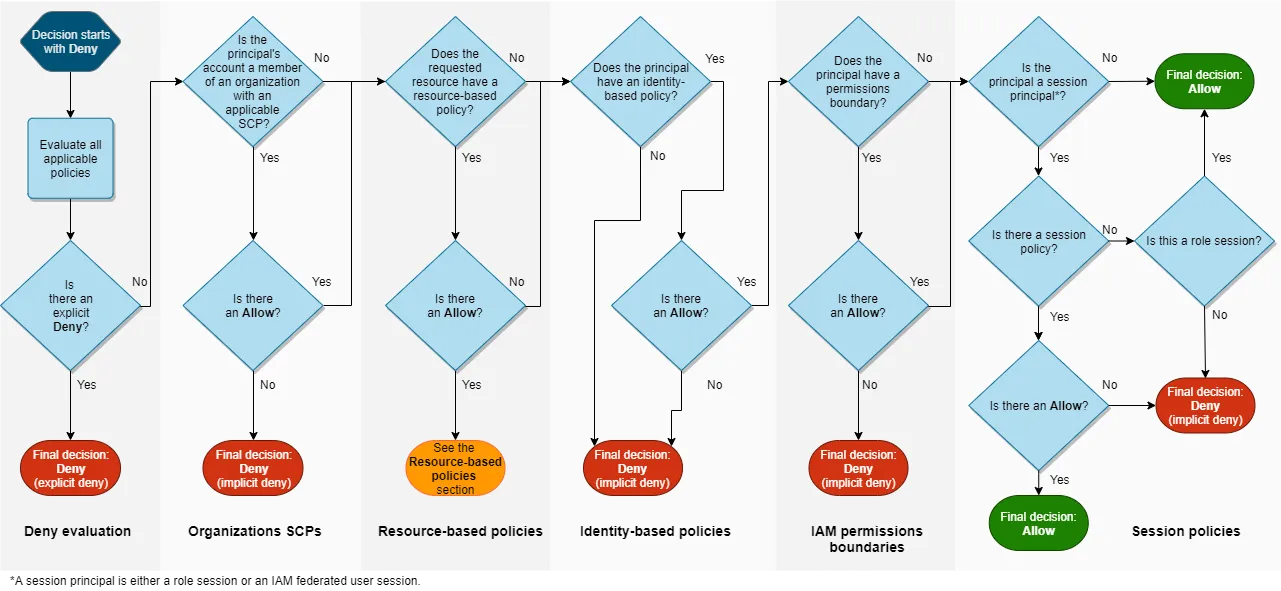
Assume that a principal sends a request to AWS to access a resource in the same account as the principal's entity. The AWS enforcement code decides whether the request should be allowed or denied. AWS evaluates all policies that are applicable to the request context. The following is a summary of the AWS evaluation logic for policies within a single account.
In this case, the answer to the restriction of the administrator role is not complex. You just use AWS Organizations' Service Control Policies (SCP) feature.
The reason is that SCP works on an upper layer of IAM.I snipped the explanation of SCP in this post, but its fundamental function is the restriction for all IAM entities of the AWS account.
It's really a ”restriction” for IAM permissions.
When thinking about cloud security, many people may imagine some features of "restriction". However, it may only work as a "guardrail" to prevent operational mistakes. It is essential to clearly distinguish between these and use them appropriately. This is important for not only security engineers but also the managers who direct them.
