Infrastructure protection on AWS for Beginners
"Blending AI and AWS security, this image embodies the future of cloud protection: robust, innovative, and seamlessly integrated."
- AWS Shield: A managed Distributed Denial of Service (DDoS) protection service that safeguards web applications running on AWS. It helps protect your applications against volumetric and state-exhaustion DDoS attacks.
- AWS WAF (Web Application Firewall): Helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. You can use AWS WAF to create custom rules for traffic filtering based on IP addresses, HTTP headers, or URI strings.
- AWS Firewall Manager: A security management service that makes it easier to centrally configure and manage firewall rules across your accounts and applications in AWS Organization. It simplifies your AWS WAF, AWS Shield Advanced, and AWS Network Firewall administration.
- AWS Network Firewall: A managed service that makes it easy to deploy essential network protections for all of your Amazon Virtual Private Clouds (VPCs). It provides granular control over network traffic and allows you to build scalable network security services.
- Amazon GuardDuty: A threat detection service that continuously monitors for malicious activity and unauthorized behavior to protect your AWS accounts and workloads. It uses machine learning to detect anomalies from multiple data sources like VPC Flow Logs, CloudTrail logs, and DNS logs.
- A Stateless Rule Group
- A Firewall Policy
- The VPC it will be deployed in
- The subnet where the firewall endpoint will be
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
{
"RuleGroupName": "MyStatelessRuleGroup",
"RuleGroup": {
"RulesSource": {
"StatelessRulesAndCustomActions": {
"StatelessRules": [
{
"RuleDefinition": {
"MatchAttributes": {
"Sources": [
{ "AddressDefinition": "0.0.0.0/0" }
],
"Destinations": [
{ "AddressDefinition": "0.0.0.0/0" }
]
},
"Actions": [
"aws:pass"
]
},
"Priority": 1
}
],
"CustomActions": []
}
}
},
"Type": "STATELESS",
"Description": "Example stateless rule group",
"Capacity": 10,
"Tags": [
{
"Key": "ExampleKey",
"Value": "ExampleValue"
}
]
}
aws network-firewall create-rule-group --cli-input-json file://stateless-rule-group.json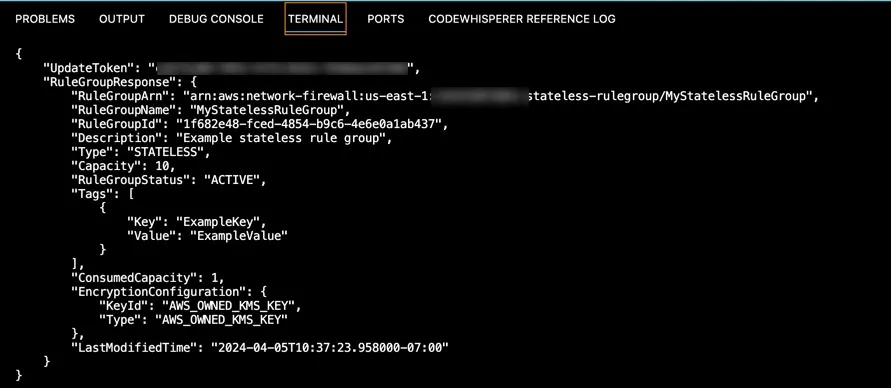
- Create a JSON file (e.g., firewall-policy.json) that defines your AWS Network Firewall policy. Here is an example of a simple policy note that we reference the ResourceArn of the Stateless Rule group we created:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
{
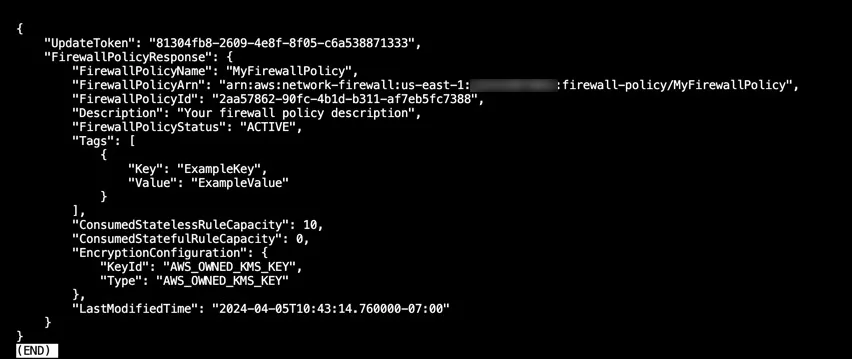
"FirewallPolicyName": "MyFirewallPolicy",
"FirewallPolicy": {
"StatelessDefaultActions": [
"aws:pass"
],
"StatelessFragmentDefaultActions": [
"aws:drop"
],
"StatelessRuleGroupReferences": [
{
"ResourceArn": "arn:aws:network-firewall:us-east-1:1234567890:stateless-rulegroup/MyStatelessRuleGroup",
"Priority": 1
}
],
"StatefulRuleGroupReferences": []
},
"Description": "Your firewall policy description",
"Tags": [
{
"Key": "ExampleKey",
"Value": "ExampleValue"
}
]
}create-firewall-policy command: Execute the following AWS CLI command to create the Network Firewall policy:aws network-firewall create-firewall-policy --cli-input-json file://firewall-policy.json- Next, verify the creation: After running the command successfully, you will receive a response containing details about the newly created Network Firewall policy, including the policy ARN.
--firewall-name my-firewall \
--firewall-policy-arn arn:aws:network-firewall:us-east-1:1234567890:firewall-policy/MyFirewallPolicy \
--vpc-id vpc-0ae0891d4aeae8506 \
--subnet-mappings SubnetId=subnet-0a3e07fcd0545df5c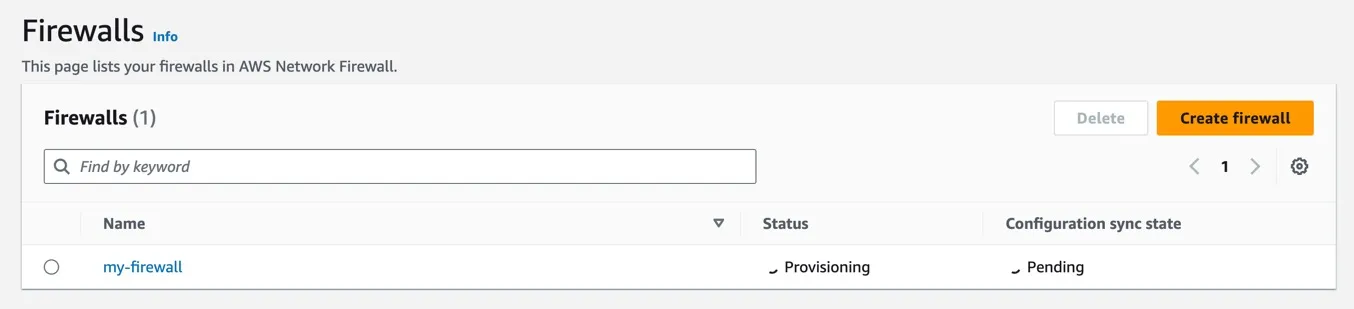
- Threat Detection and Information Retrieval:
- A RAG model can continuously monitor logs and alerts generated by AWS services like CloudTrail, GuardDuty, and CloudWatch.
- Upon detecting an anomaly or a potential security threat, it can instantly retrieve relevant information from a vast collection of security advisories, white papers, AWS documentation, internal documentation, and known threat databases.
- Contextual Analysis and Threat Assessment:
- Using the retrieved information, the RAG model can assess the context and severity of the detected threat by comparing it against known patterns, vulnerabilities, and exploits.
- This includes analyzing the potential impact of the threat on the infrastructure, considering factors like the affected AWS services, data sensitivity, and compliance requirements.
- Automated Response Generation:
- Based on the analysis, the RAG model can generate recommended actions or automate responses. This could range from isolating affected instances, updating security groups, deploying AWS WAF rules to mitigate DDoS attacks, or initiating backups in response to ransomware threats.
- For complex issues requiring human intervention, the model can draft detailed incident reports, including the threat's nature, affected resources, recommended mitigation strategies, and reference to similar past incidents and how they were resolved.
Any opinions in this post are those of the individual author and may not reflect the opinions of AWS.
