Protect API Gateway with Amazon Verified Permissions
In this post we'll look at Amazon Verified Permissions (AVP) a serverless service for easy management and enforcement of application permissions, and how to use it to secure Amazon API gateway API together with Cognito User Pools.
Published Apr 12, 2024
Amazon Verified Permissions (AVP) was presented during re:Inforce 2022. AVP is a fully managed serverless service that simplifies managing and enforcing application permissions. It uses Cedar policy language, which is one fastest growing policy language at the moment.
AVP is the perfect service to use for implementation of you application permissions. It's a great tool when implementing a centralized policy decision point (PDP). Isolation of tenants in a SaaS solution is made easy with AVP.
Up until now, protecting your API Gateway API with Amazon Cognito User Pools and AVP has been hard to do. With this new feature release this is now made easy.
In this post we'll look at this new feature and continue my series on securing API Gateway, Secure your API Gateway APIs with Auth0, Secure your API Gateway APIs mutual TLS, and Secure your API Gateway APIs with Lambda Authorizer.
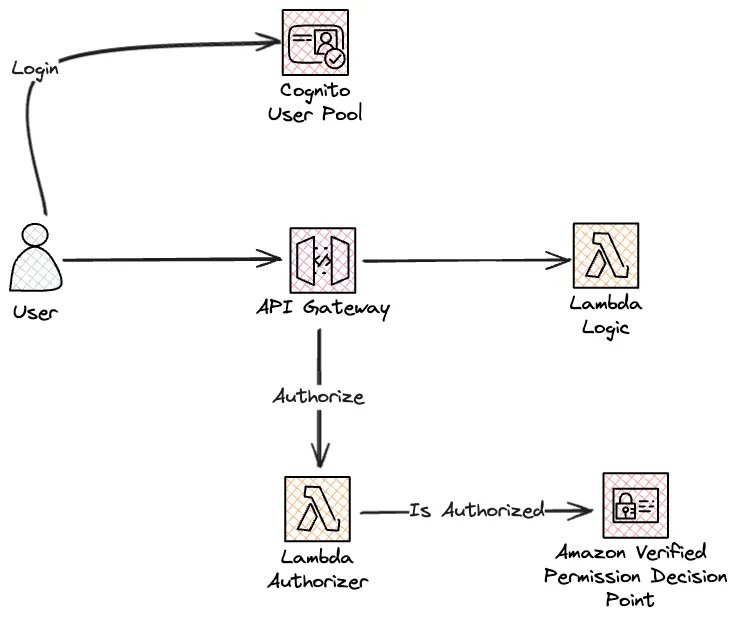
There are three parts in this setup. Amazon Cognito User Pool, API Gateway and Amazon Verified permissions decision endpoint. Users will call Cognito to logon and get their tokens. The tokens will be sent to API Gateway API in the Auth header, and we'll have a Lambda Authorizer to call AVP to verify the access.
The first thing we need to do is create an Cognito User Pool.
Before we can continue the first thing we need is an Cognito User Pool. Let's create the pool using the below CloudFormation template.
When the user pool is created we need to create two groups, trainers and riders. Let's do this from the console this time, navigate to Cognito section, locate the user pool and click on it.
From here select the Groups tab and create the two groups, trainers and riders.
Next up, create the API.
Next part we need is the Api Gateway API. Right now it's only REST api that is supported, hopefully there will be support for HTTP api in the future as well.
Let's use CloudFormation and SAM to create the API that we need.
This will create an REST Api Gateway API with nine resources.
If you click the unicorn service api you should see the created resources.
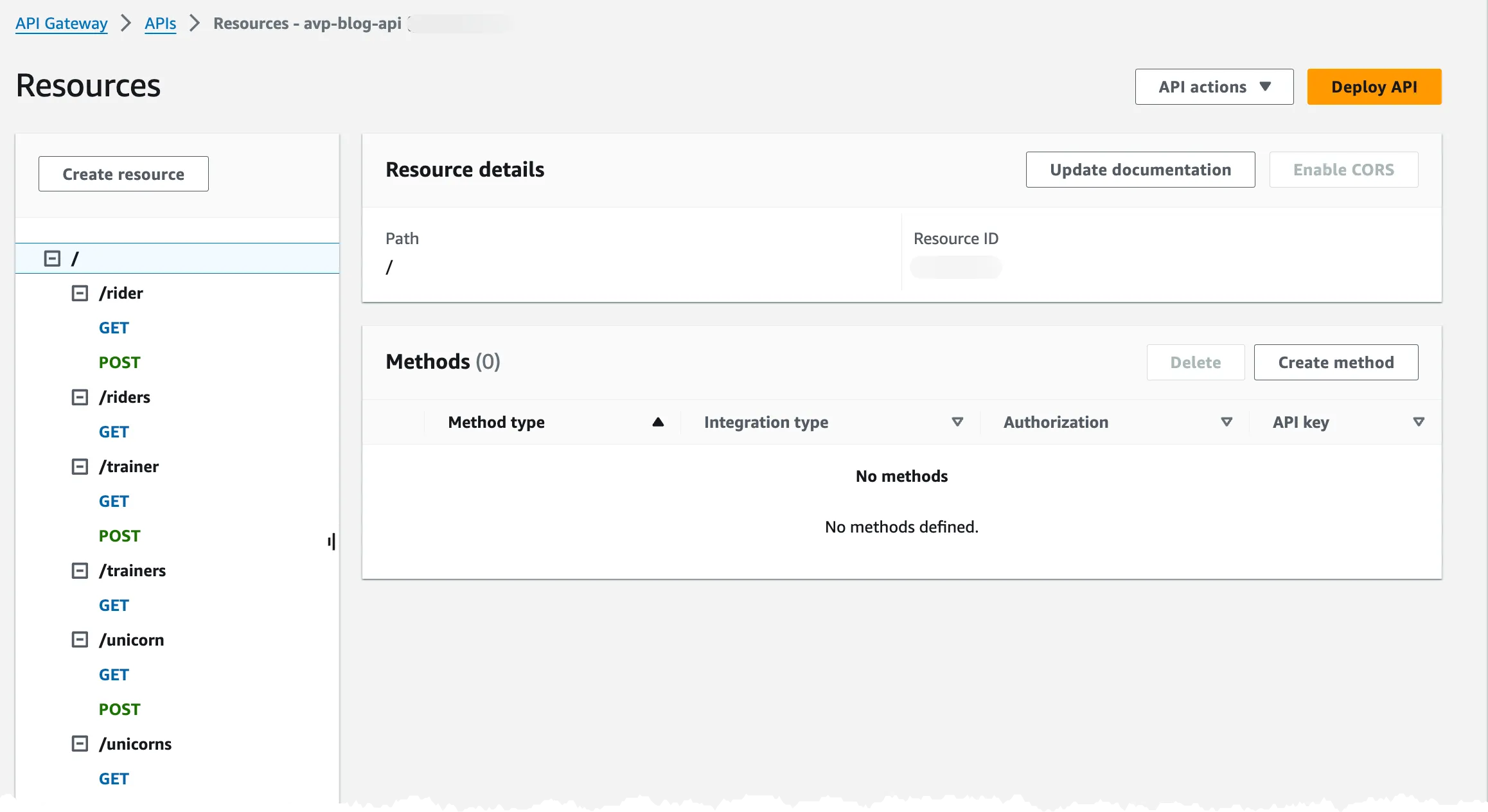
Selecting one of the resources will show that no auth is configured.
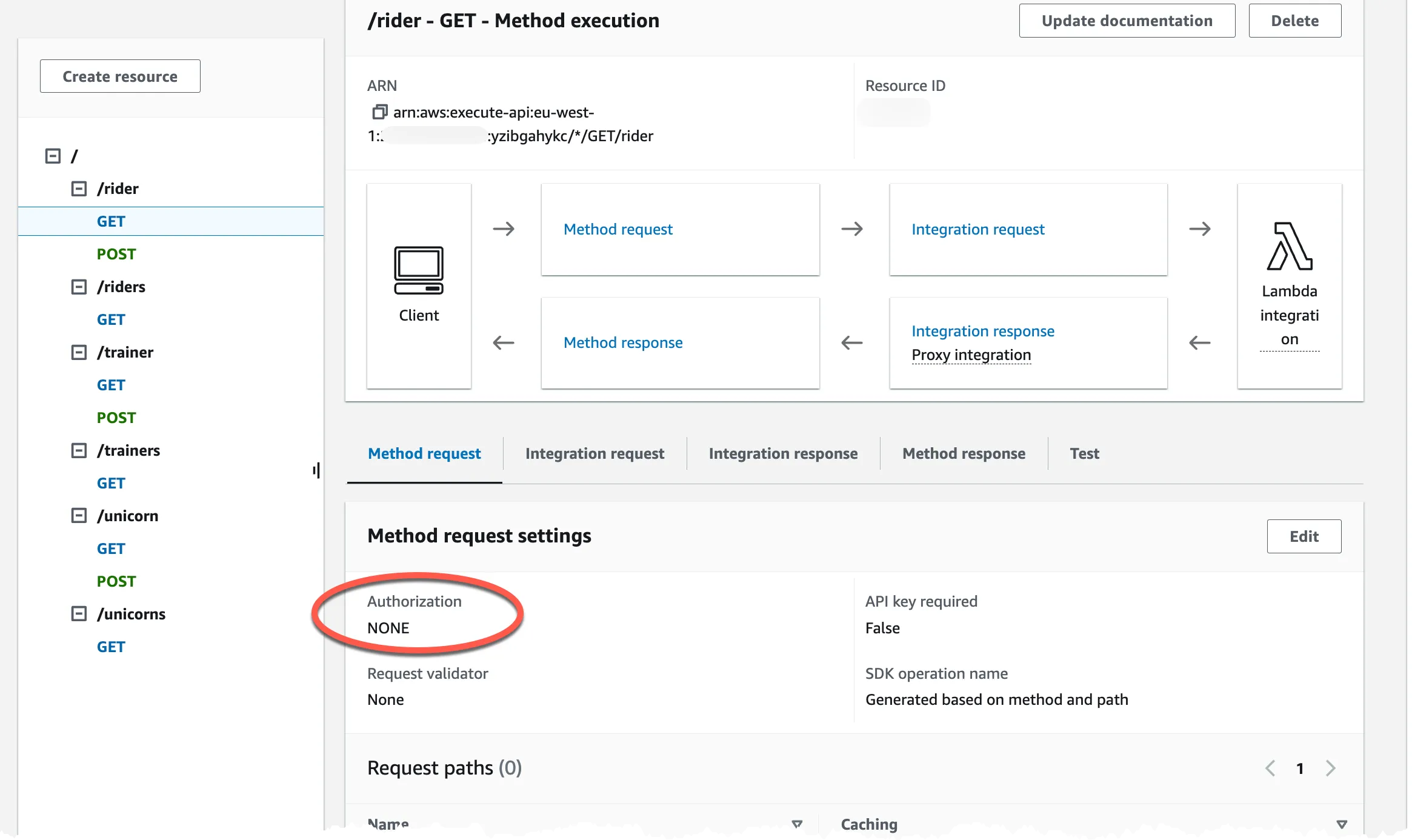
Now both the prerequisites are created and we can move over to the actual securing using Amazon Verified Permissions.
This part of the setup will purely manual as AVP has released the quick start, to help us configure Authorization for APIs using verified permissions.
The first thing we need to do is open Amazon Verified Permissions section of the console, from here we'll start creating a policy store.
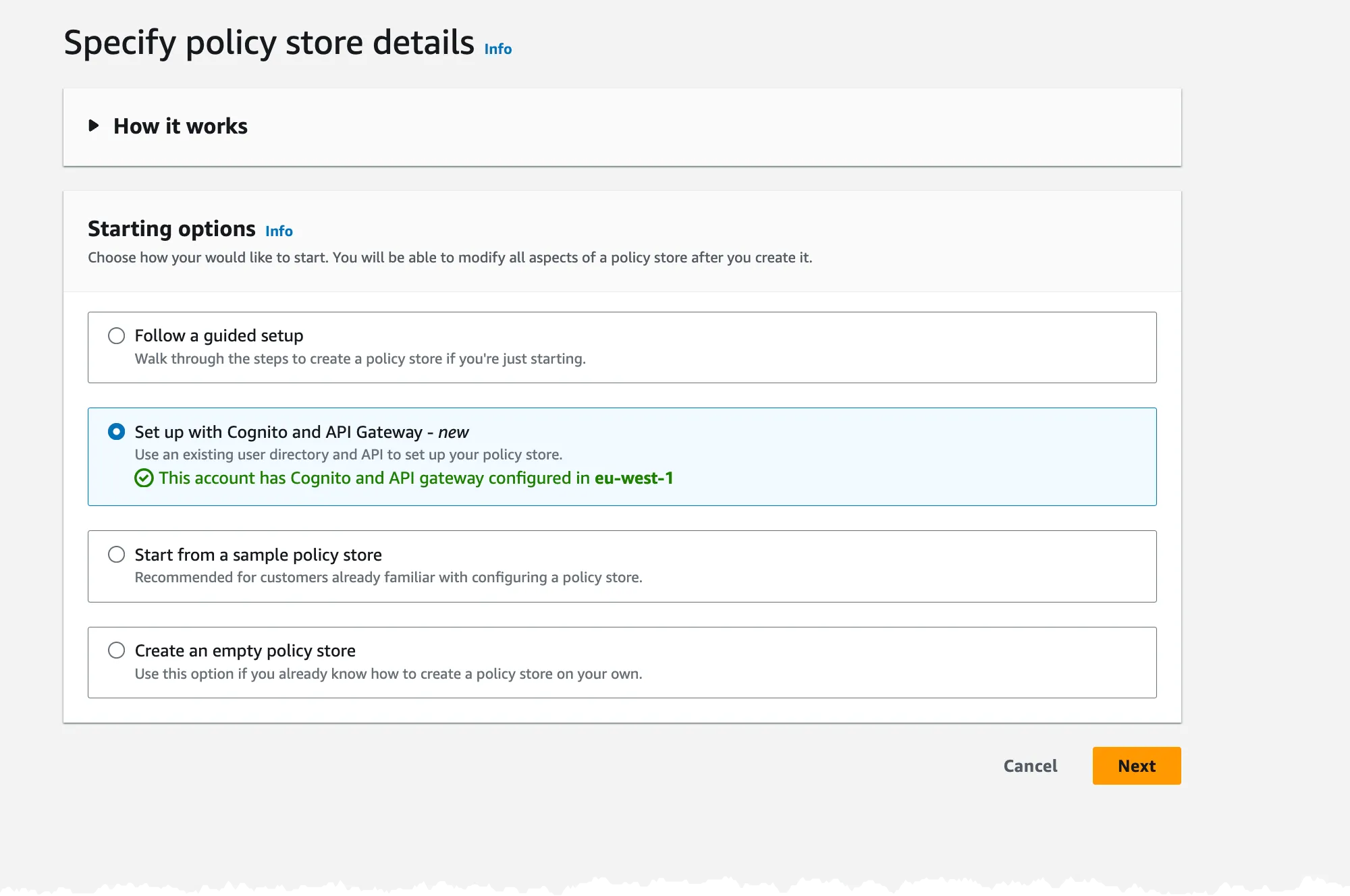
In this first step in the guide we select that we like to use Cognito and API Gateway, both need to be in place already. If they are missing there will be a message informing that.
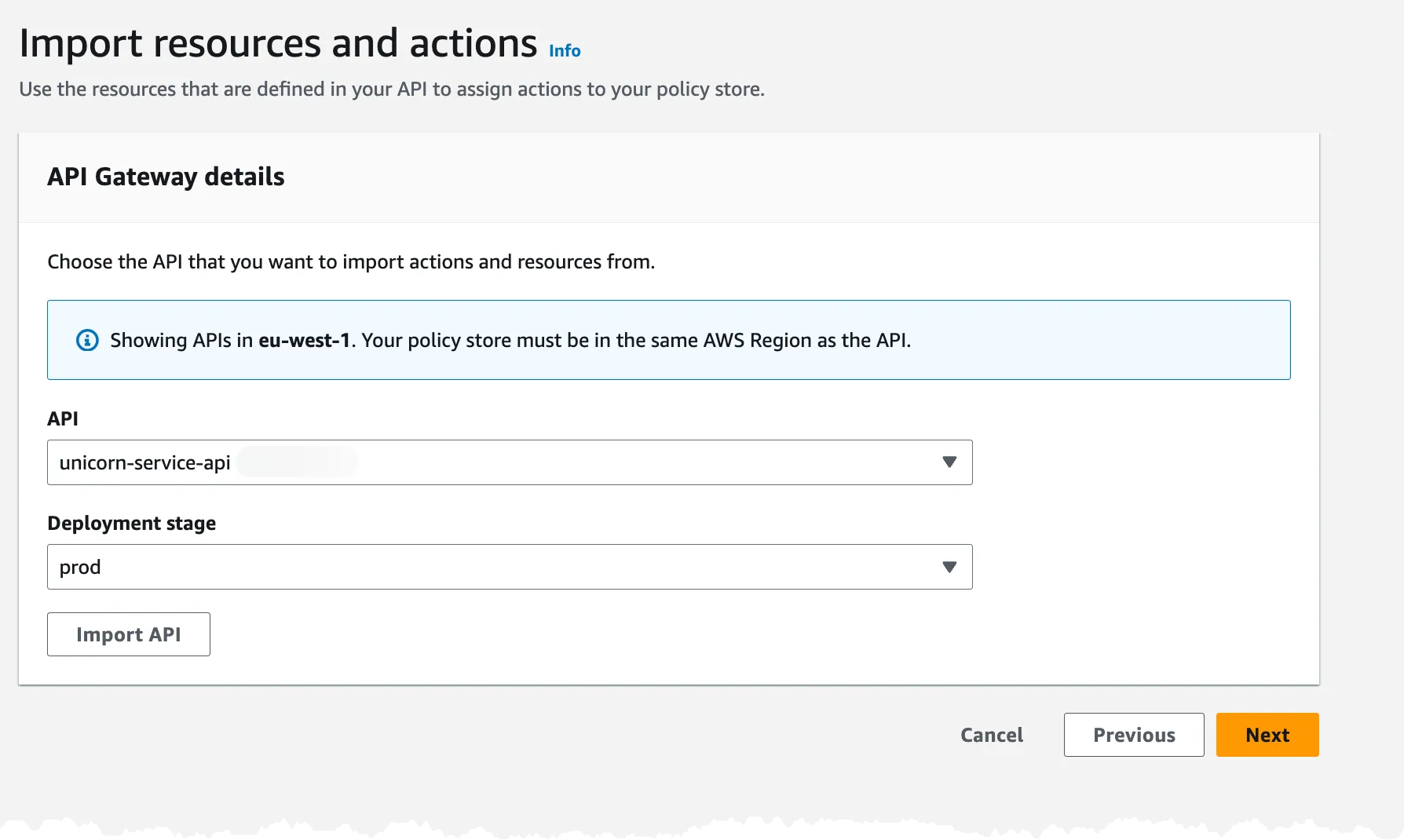
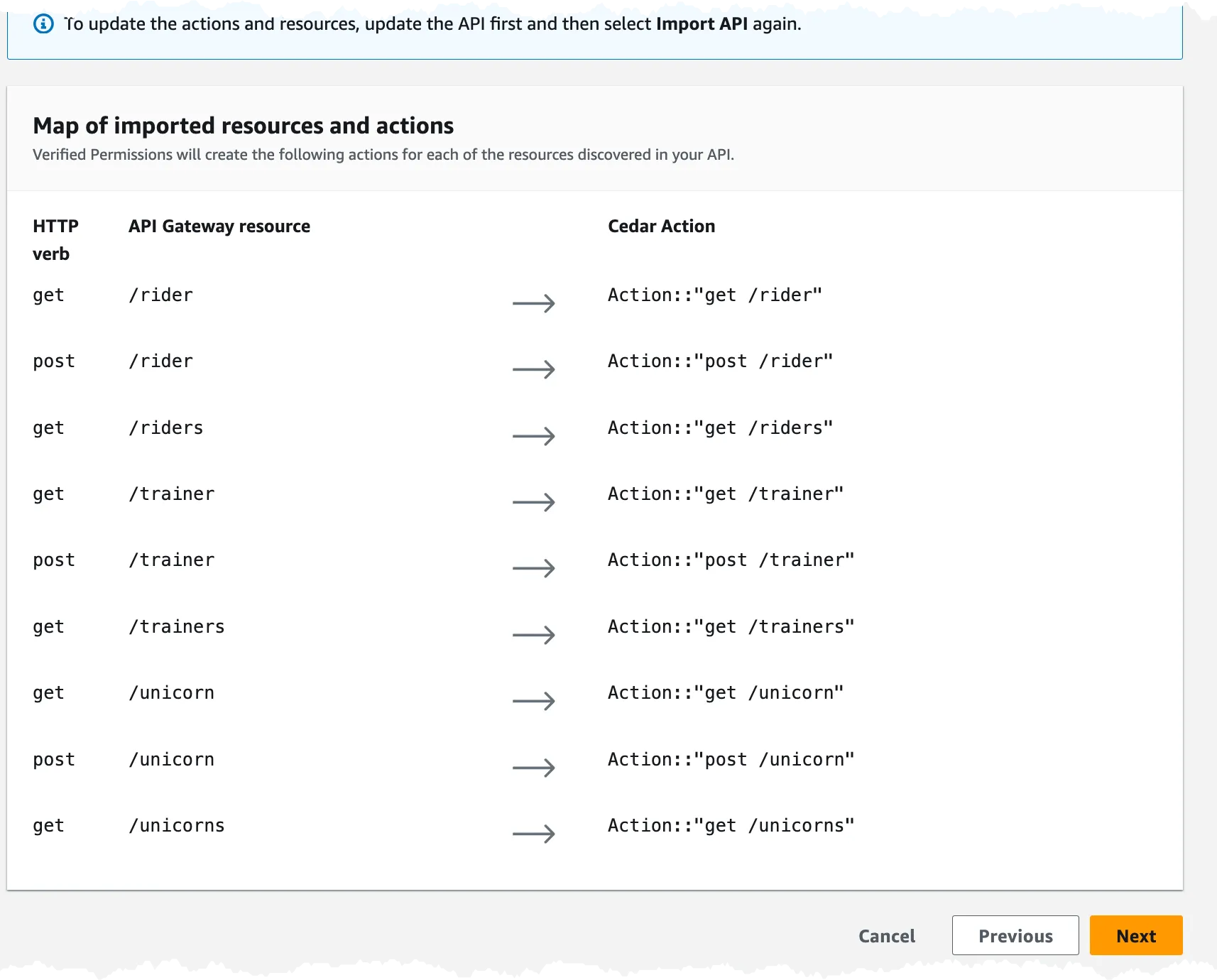
Now we need to select the API and Stage and import the API.
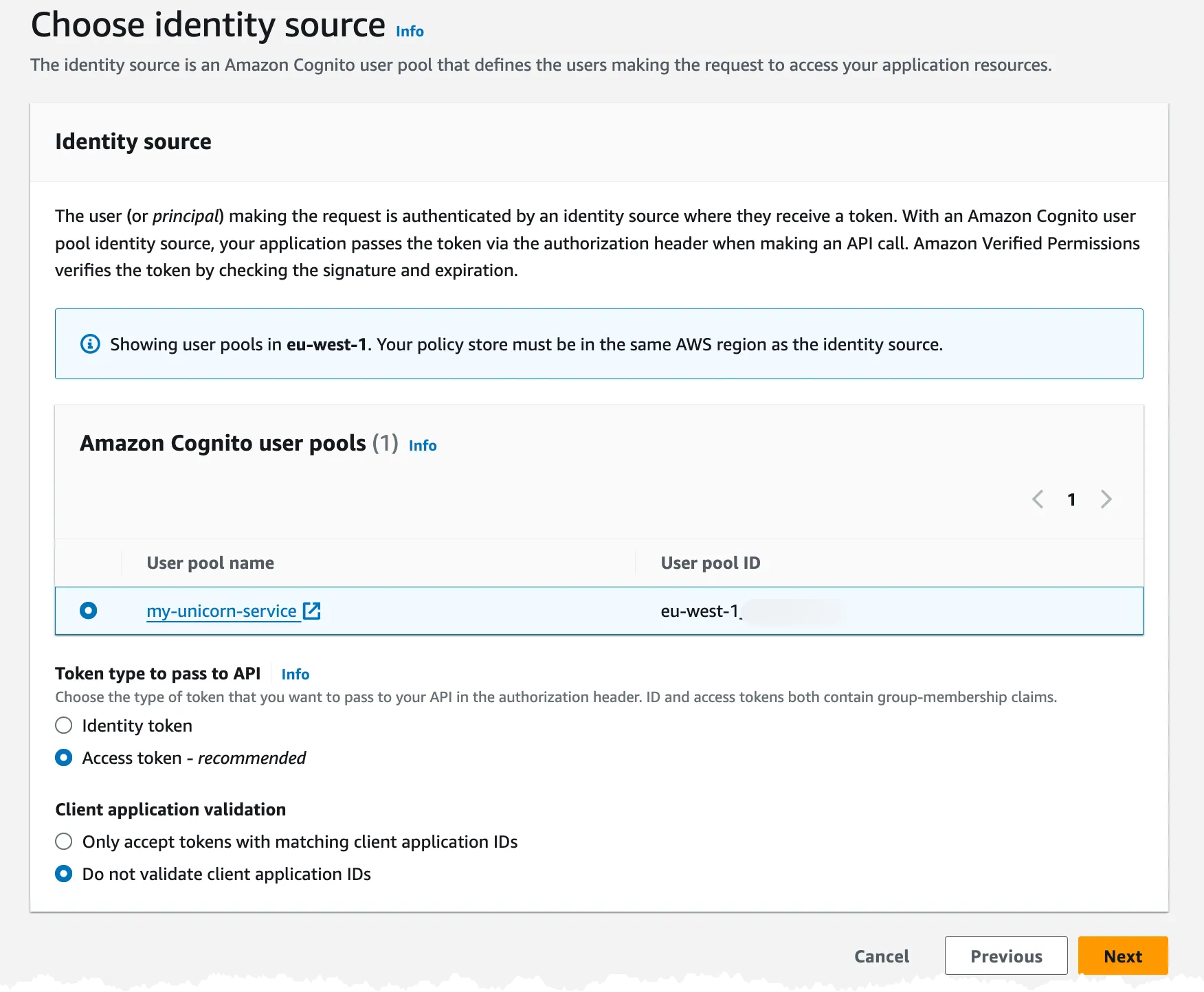
Next step is now to select the Identity Source and in this case it will be the Cognito User Pool.
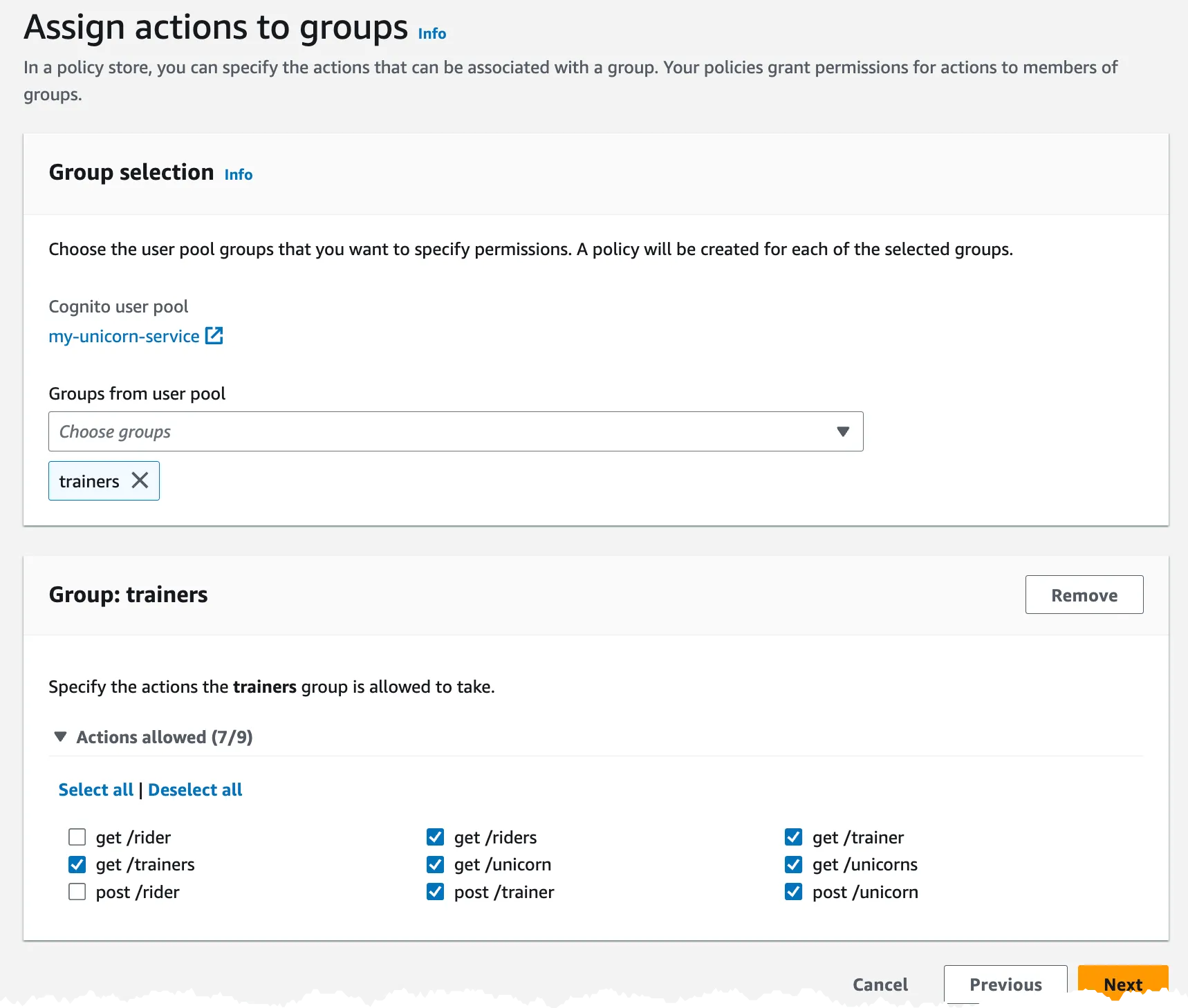
Final step is to assign what actions a specific group should have access to in the API.
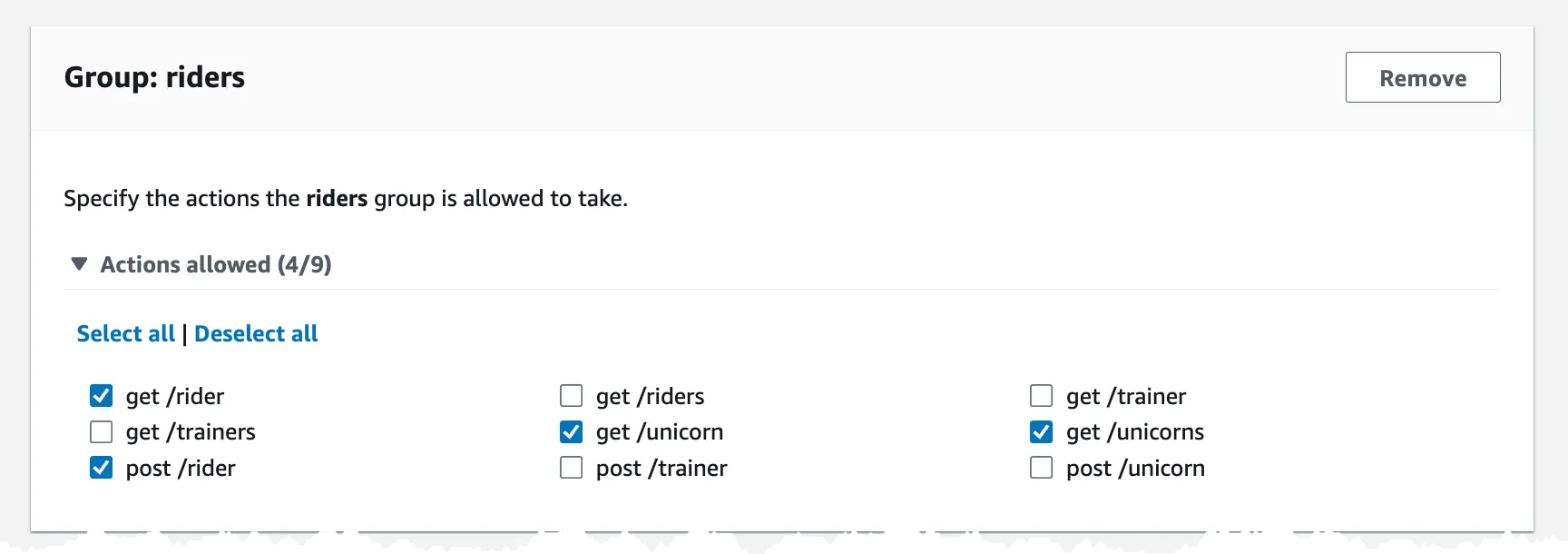
Now, we are all set and ready to create the policy store.
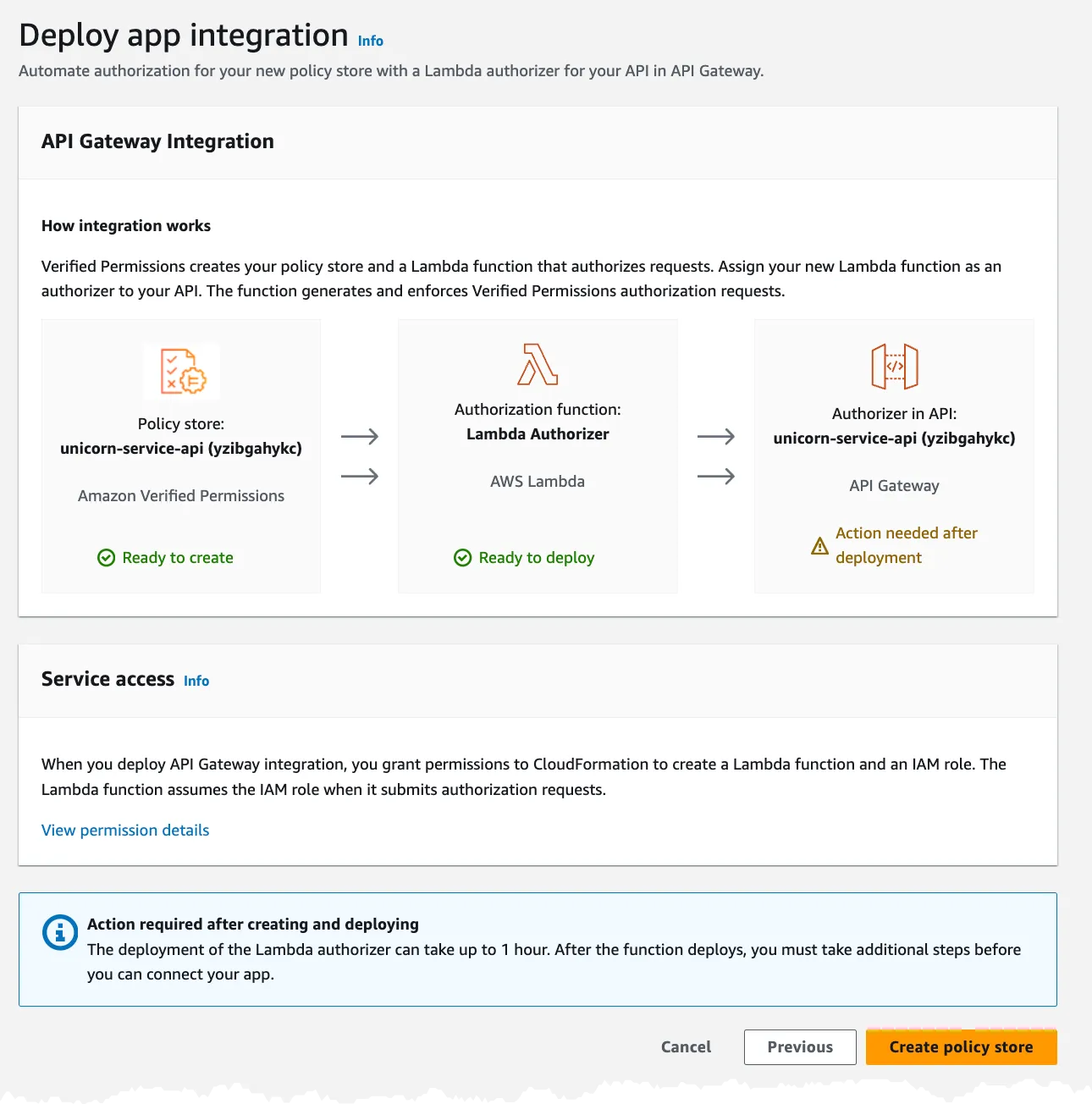
So far this has been a very nice flow and very easy to use. But! Now the problem started for me. The first thing was that I got an error with an invalid character in the namespace.
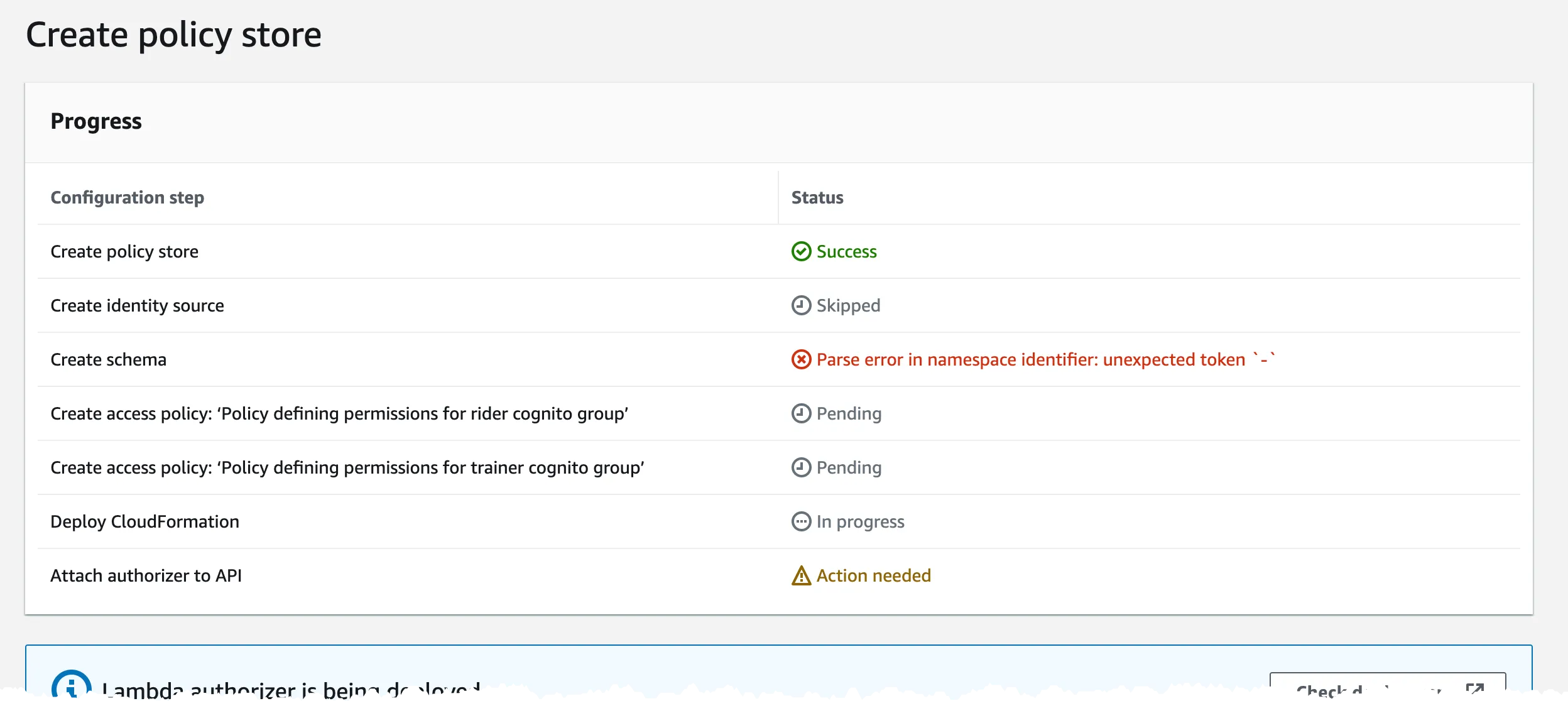
This happens since I used '-' in the name if the API Gateway API, I named it 'unicorn-service-api' and this is used as the name space and was not allowed. I think the guide should have warned me about this earlier. The first step in the guide checks that there is an User Pool and an API Gateway API, it could also check the name requirements.
After solving this problem, renaming the API Gateway API, the error was gone.
After the policy store has been created the Lambda Authorizer must be connected to the API Gateway actions. Navigate to the API Gateway API and select Resources in the menu.
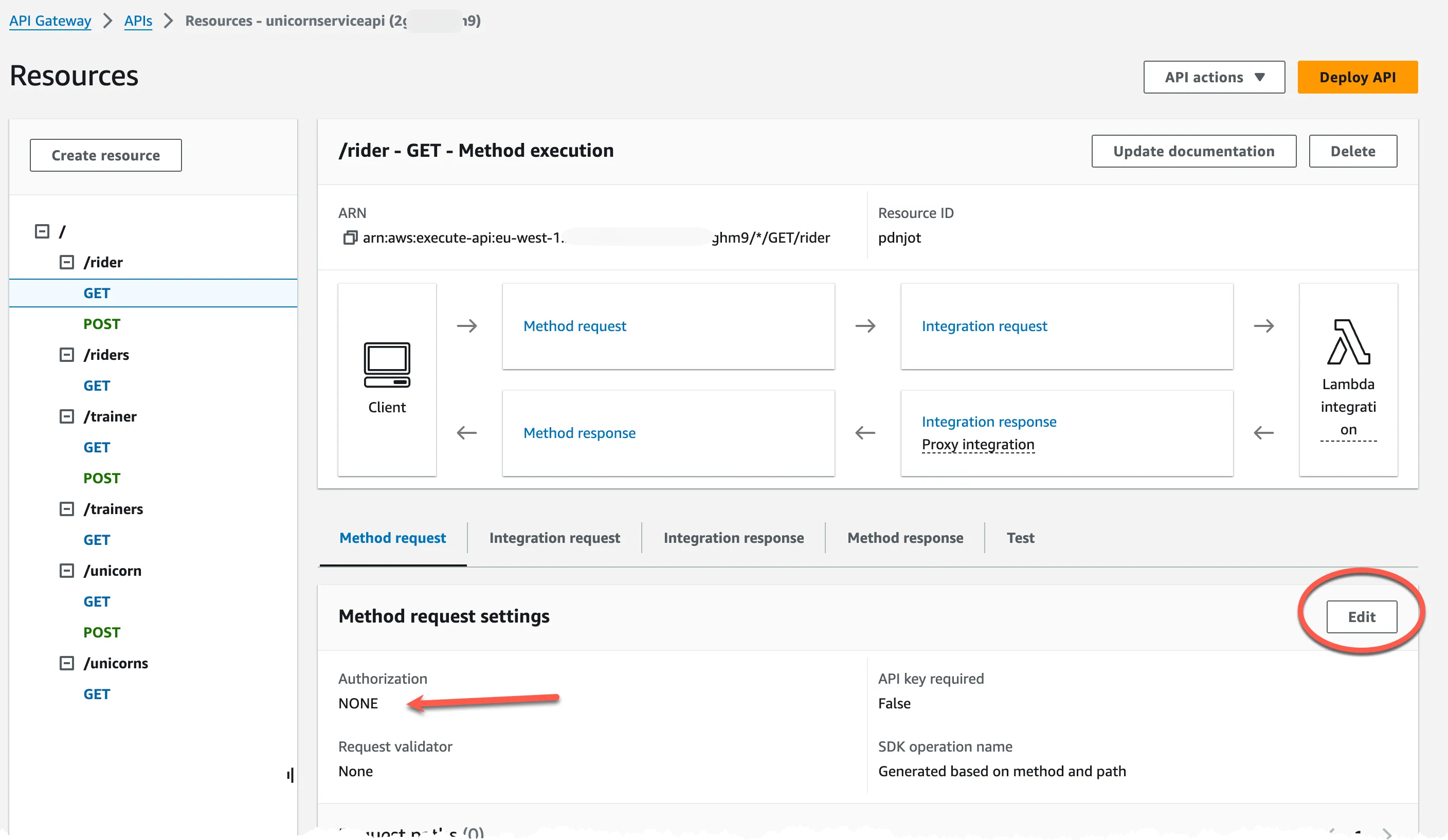
Select the action and then click on Edit for 'Method request settings'. In the drop down menu select the Lambda Authorizer. Repeat this for all of the actions in the API.
Final step is then to Deploy the API to your stage again, changes do not take affect until this is done.
With this connection, you are done and your API is protected with Cognito User Pool and Amazon Verified Permissions.
I think this is a nice addition and it makes creation of the Lambda Authorizer easier, however I do see a couple of areas for improvements.
First. Today the guide will deploy a CloudFormation template with the Lambda Authorizer. To connect this authorizer to API Gateway API this must be done manually in the console. Since I'm a user of AWS SAM a Authorizer must be in the same template / stack as the API Gateway resource, so it's not possible to import from a different stack. Instead of this automatic deployment I would prefer to get an option to download the code and template in either yaml or json. That way I could include this in the same template as the API Gateway resource and then handle the connection automatically.
Second. After creation of the Policy Store and the policies there are no easy way to add additional API actions to the policy, or to add a new group in the User Pool. APIs change and I would prefer an as easy way to update as it was to create.
Last. Better checks on conditions like the problem above that gave me an error.
This was a quick walkthrough of the new feature to easy connect Amazon Verified Permissions to an API Gateway API. The process is easy to use and straight forward, but I do see improvement potential, and hopefully the guide will evolve over time.
As Werner says! Now Go Build!
