Managing multiple AWS accounts with AWS Organisations
Using AWS organisations to create multiple accounts for dev and prod workloads
- Create accounts in the organization
- Invite other existing accounts to the organization
- Remove accounts from the organization
- Designate delegated administrator accounts
- Manage invitations
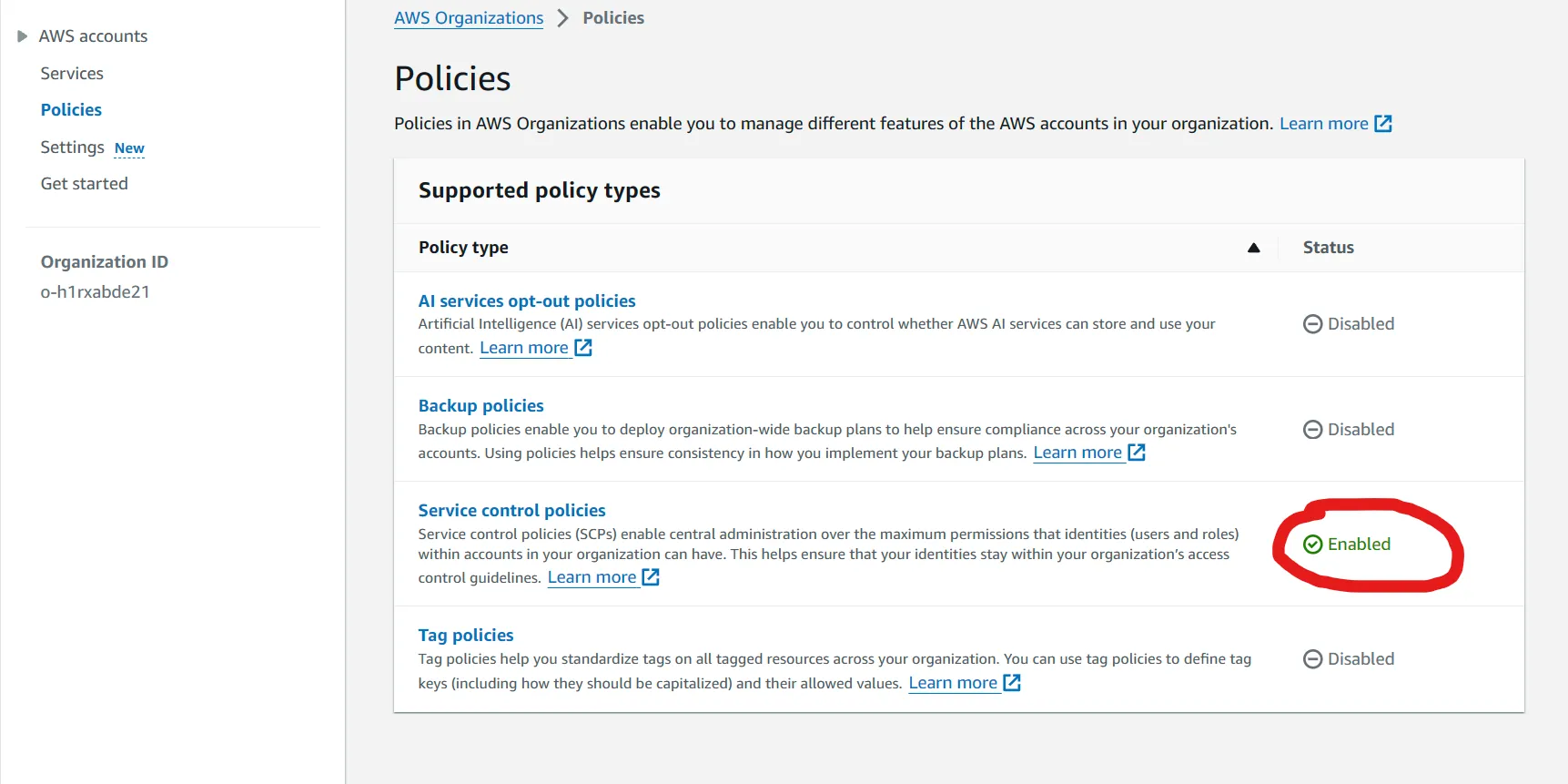
- Apply policies to entities (roots, OUs, or accounts) within the organization
- Enable integration with supported AWS services to provide service functionality across all of the accounts in the organization.
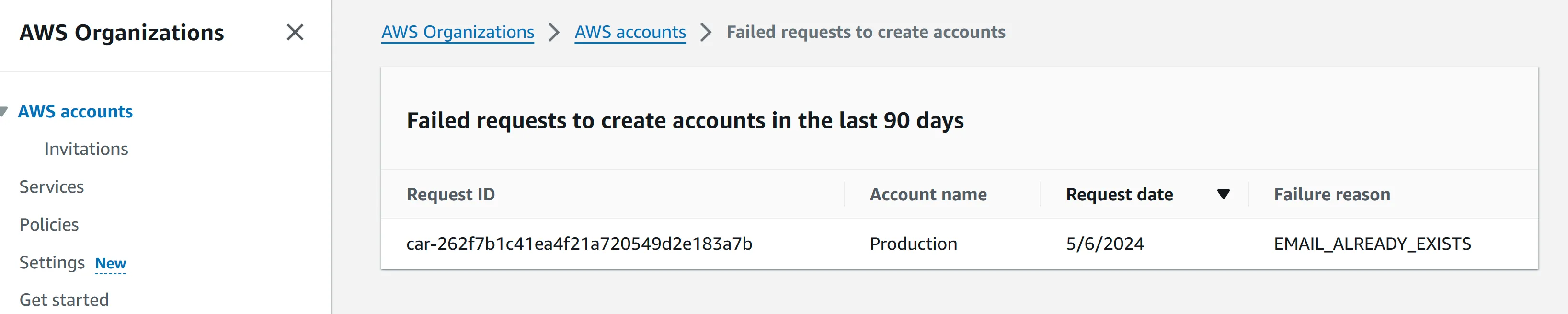
- Select the Root OU and in the on the Actions menu, under Organizational Unit, choose Create new
- In the Create organizational unit dialog box, enter the name of the OU that you want to create.
OrganizationAccountAccessRole role to the member account.By default this enables users and roles in the management account to exercise full administrative control over the member account. This can be restricted using service control policies (described in the latter section). - Account ID: <account-id of production account>
- IAM role name:
OrganizationAccountAccessRole - Display Name: Prod
- Display color: Green (or choose whatever color you like)
- Account ID: <account-id of development account>
- IAM role name:
OrganizationAccountAccessRole - Display Name: Dev
- Display color: Yellow (or another color different to the Prod Role)
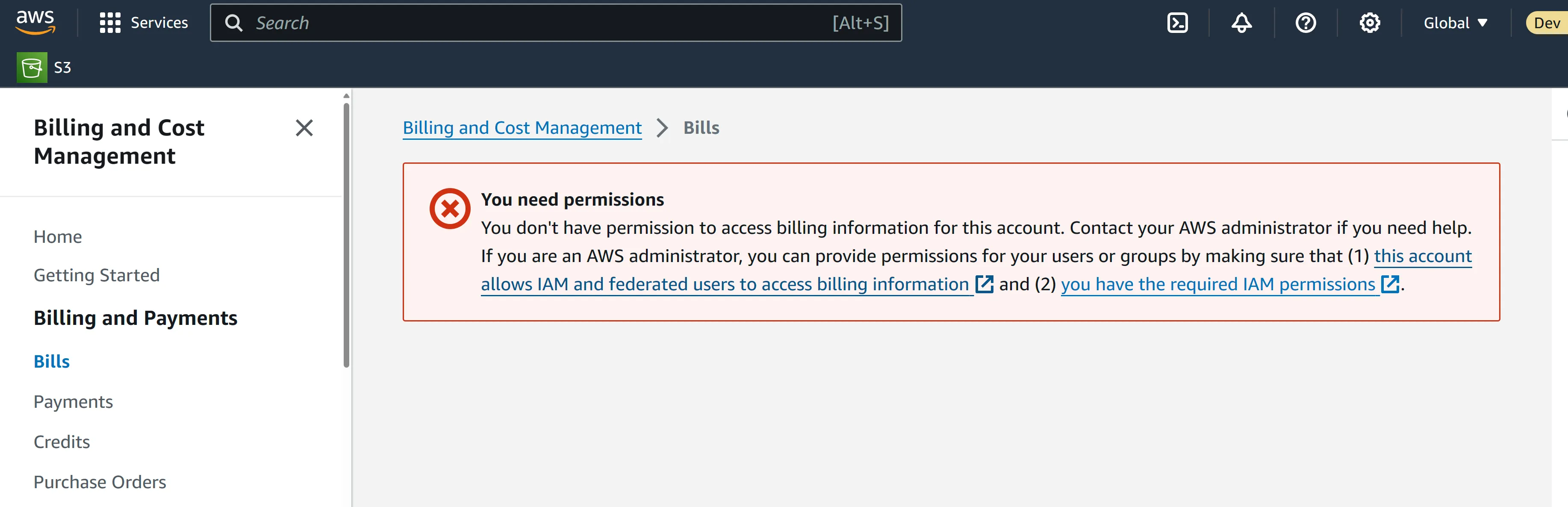
billing:* actions to the deny list. 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Deny",
"Action": [
"billing:*",
"aws-portal:*"
],
"Resource": [
"*"
]
}
]
}BillingDenySCP) and paste the policy snippet above (as shown in screenshot below) and create policy.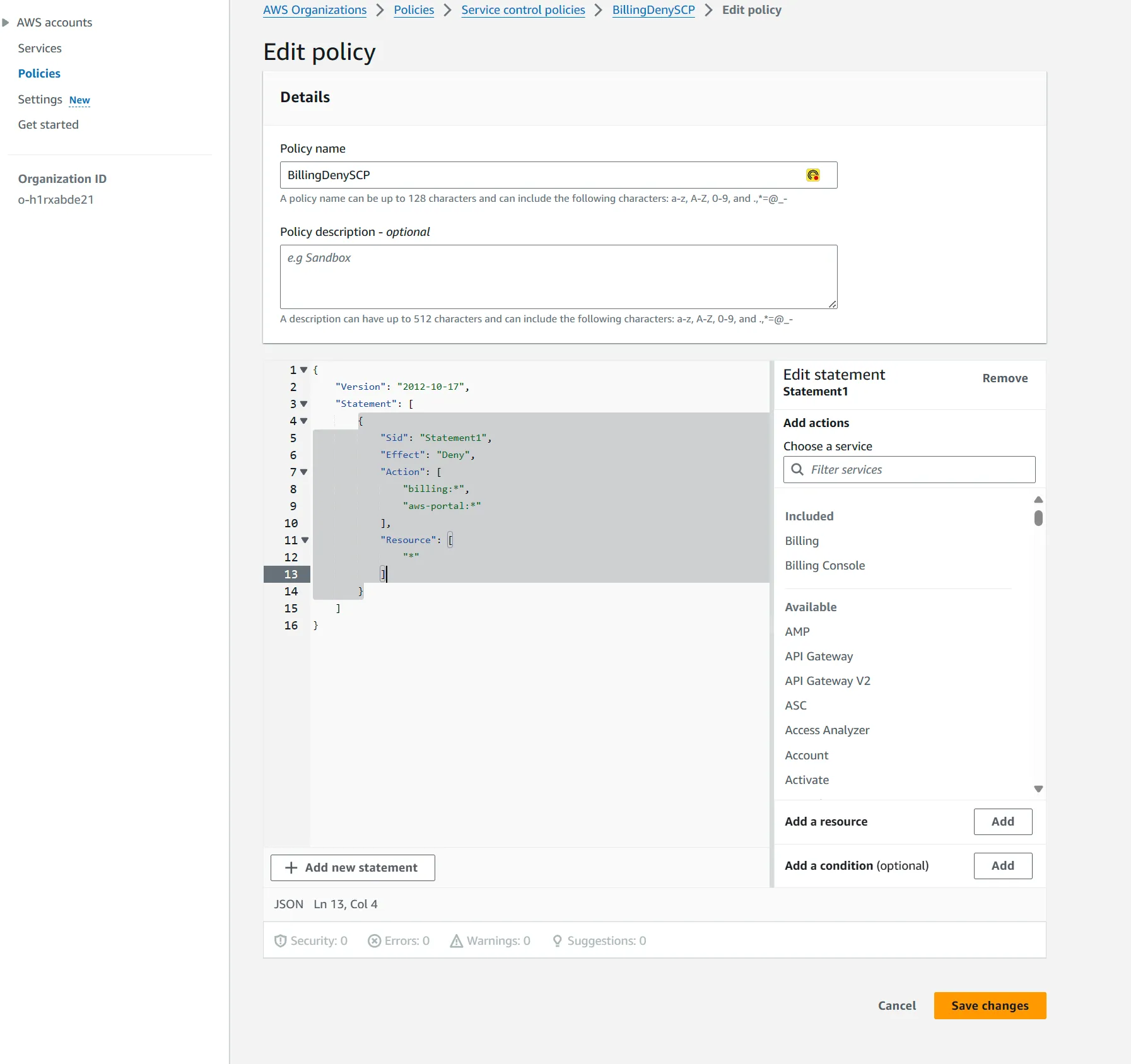
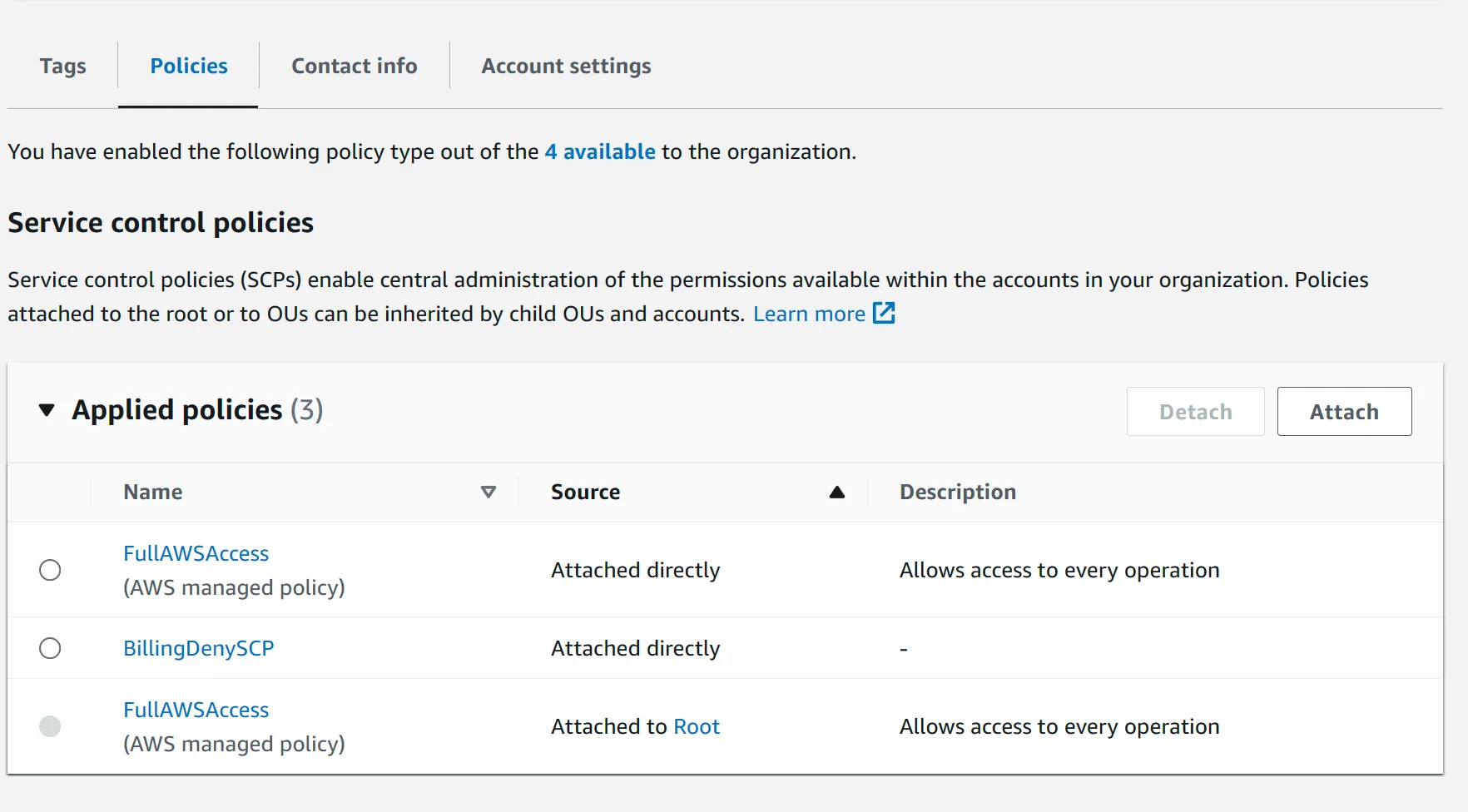
FullAWSAccess policy already attached. This is propagated down from the root account (management account). By default, all users accessing either member accounts will have full admin access. By attaching the SCP created above, with explicit deny list, we can restrict anyone in the accounts from using any restricted services or if only use certain services if they satisfy some condition.BillingDenySCP option, and then attach.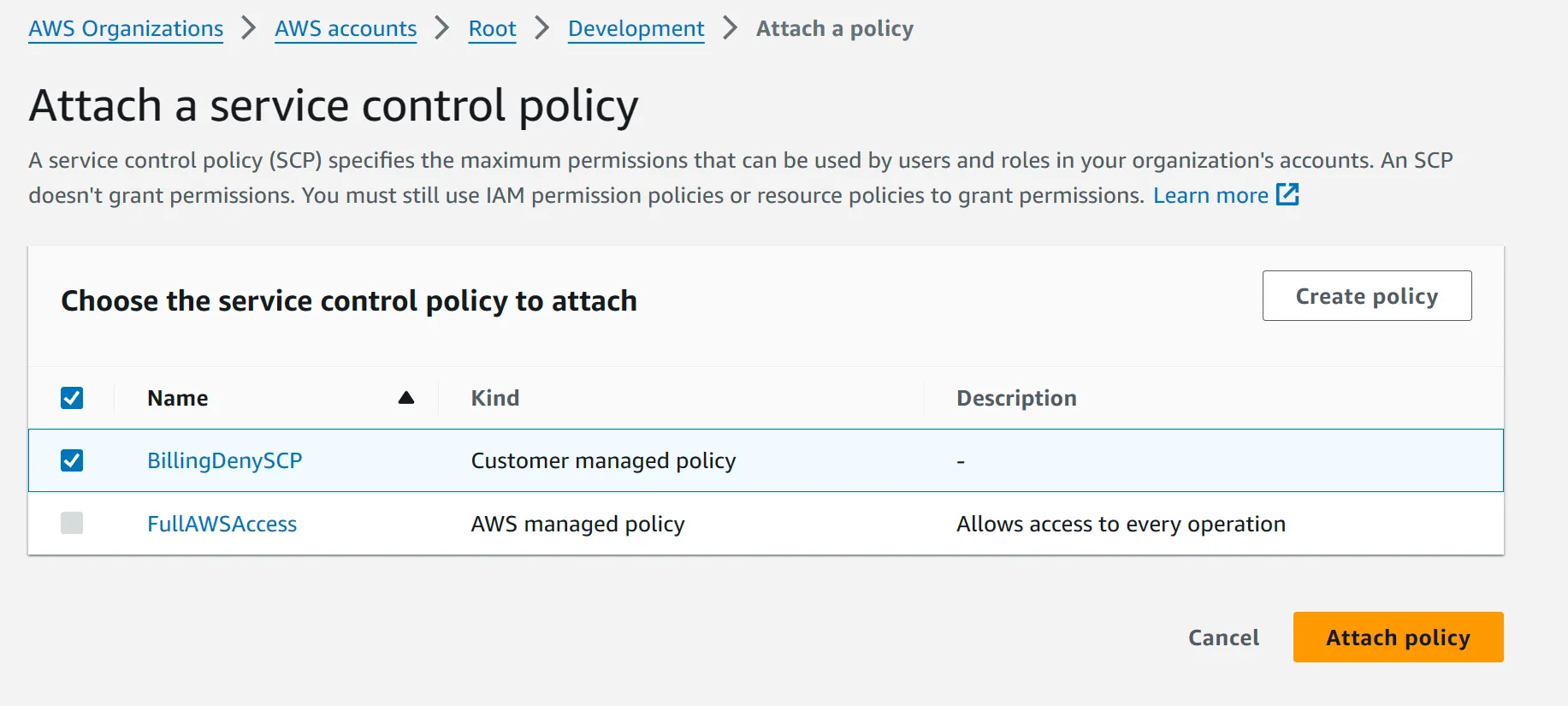
- AWS Organisations What is AWS Organizations? - AWS Organizations (amazon.com)
- Service Control Policies Service control policies (SCPs) - AWS Organizations (amazon.com)