Secure your Burnbook: Learn how to add encryption in transit to your apps using Pangea Vault and AWS Amplify
Learn how to secure sensitive data in your application with encryption in transit. Just like the "Burn Book" from Mean Girls, your user data demands protection. Dive into data encryption in this blog post and implement a simple encryption-in-transit middleware for robust security.
1
2
git clone https://github.com/pangeacyber/pangea-authn-amplify-backend-demo
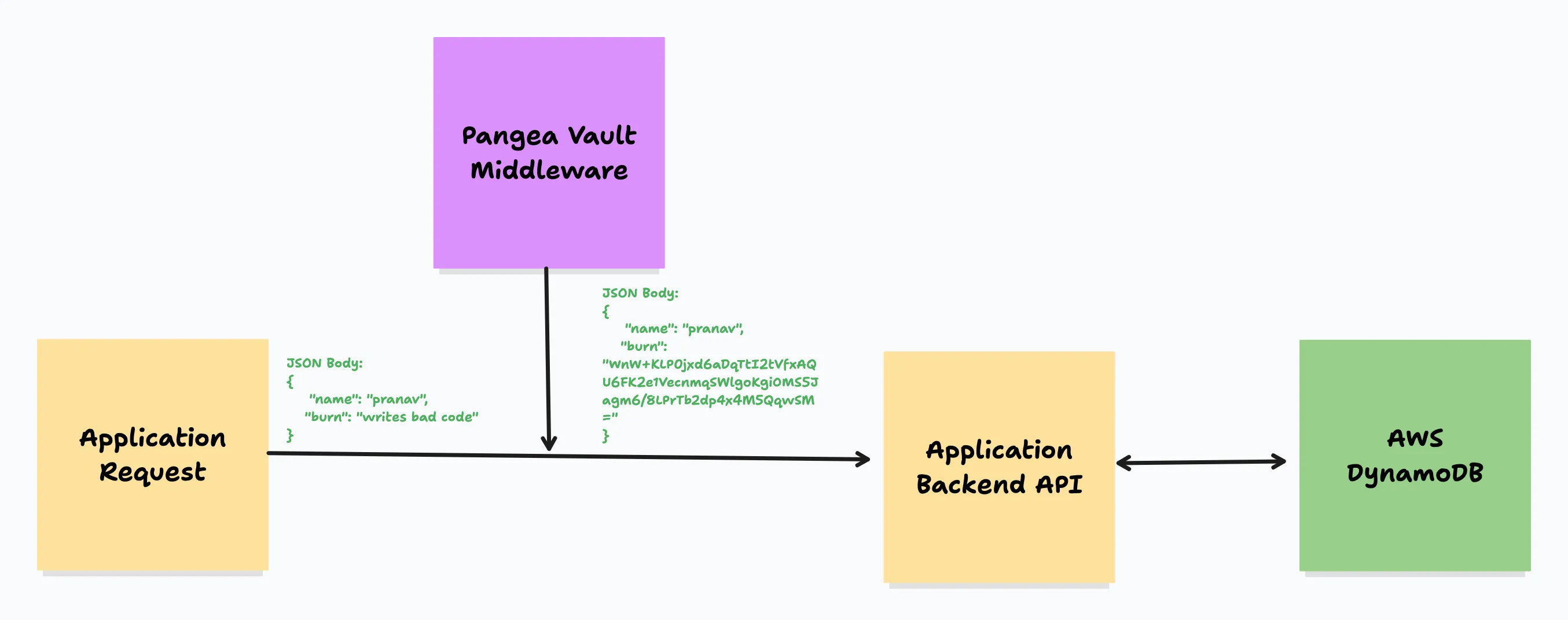
git checkout burnbooksrc/pages/api/send-burn.ts file. Notice how the exported API handler is wrapped with a middleware function encryptBodyInTransit which is defined in src/utils/encrypt-middleware.ts where the encrypt function looks something like this:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
import { PangeaConfig, VaultService, Vault } from "pangea-node-sdk";
const config = new PangeaConfig({ domain: process.env.PANGEA_DOMAIN });
const vault = new VaultService(process.env.PANGEA_TOKEN as string, config);
export const encryptBodyInTransit = (apiHandler: any) => {
return async (req: NextApiRequest, res: NextApiResponse) => {
try {
if(req.body.burn) {
const createResponse = await vault.encryptStructured({
id: "<KEY_ID_ON_PANGEA_VAULT>",
structured_data: req.body,
// define the fields to be encrypted
filter: "$.burn"
})
// only "burn" field is encrypted while all others in plaintext
// update request body
req.body = createResponse.result.structured_data;
}
// continue with API functionality
return await apiHandler(req, res);
} catch (e) {
console.error(e);
res.status(500).json({ error: e });
}
}
}encryptStructured API from Pangea Vault’s extensive API set allowing us to specify the fields we would like to encrypt. Similarly, we can do the same with decrypting data in transit.