Comprehensive Guide to AWS Control Tower
Streamlining multi-account AWS environments
Published May 8, 2024
Hello Cloud learners,
Here is an another interesting article about important key points when setting up multi-aws accounts.
AWS Control Tower is a service that helps organizations set up and govern multi-account AWS environments based on best practices from AWS experts and industry requirements. It provides a unified way to set up and manage a secure, multi-account AWS environment using service control policies (SCPs) and guardrails.
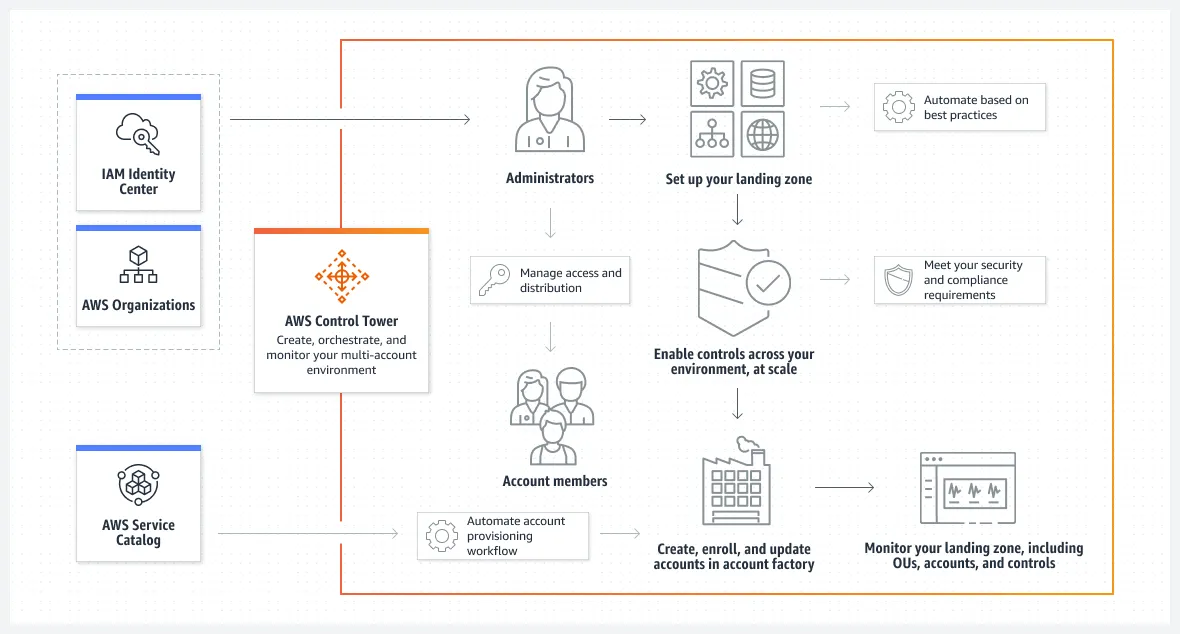
When organizations create a new AWS Control Tower landing zone, multiple AWS accounts are automatically provisioned, including a management account, a log archive account, and shared/workload accounts based on specified specifications. The management account is the main account used to manage the overall environment, while the log archive account is dedicated to storing logs from accounts in the landing zone. Shared/workload accounts are used for deploying and managing applications or workloads.
Let's deep dive into key components and functionality of AWS Control Tower:
Account Factory
The Account Factory is responsible for automatically provisioning and managing AWS accounts within the landing zone based on customized account provisioning settings. It creates new accounts in an automated and consistent manner, preconfiguring them with appropriate security controls, logging configurations, and default Amazon Virtual Private Cloud (Amazon VPC) settings.
Customizable Baselining
AWS Control Tower baselining capabilities allow organizations to define and enforce a set of rules, known as guardrails, across their AWS accounts and resources. Guardrails are essentially AWS Control Tower rules that govern aspects such as AWS Identity and Access Management (IAM) settings, logging configurations, encryption settings, and resource quotas.
There are two types of guardrails: mandatory and strongly recommended. Mandatory guardrails are enforced automatically across all accounts and cannot be modified or disabled. Strongly recommended guardrails are optional, but highly recommended for security and compliance purposes.
Service Control Policies (SCPs)
SCPs are a key part of AWS Control Tower's governance model. They are JSON policies used to define permissions across accounts in an organization, allowing organizations to establish boundaries for what actions can be taken with AWS services and resources. SCPs are defined at the organization root (OU) level and apply to all accounts within that OU.
For example, an SCP can restrict the ability to create specific resource types, enforce specific resource configurations, or limit the regions where resources can be created. This ensures consistent compliance and security across the entire AWS environment.
Integration with AWS Services
AWS Control Tower integrates with various AWS services to provide a comprehensive governance and compliance solution. For example:
- AWS Organizations: AWS Control Tower leverages AWS Organizations to manage accounts, organizational units (OUs), and service control policies (SCPs).
- AWS Config: AWS Config is used to record and evaluate the configuration of AWS resources against defined rules and best practices.
- AWS CloudTrail: AWS CloudTrail is used to log and monitor AWS API activity across all accounts and services in the landing zone.
- AWS Security Hub: AWS Security Hub provides a comprehensive view of security alerts and compliance status across the AWS environment.
- AWS Config Rules: AWS Control Tower uses AWS Config Rules to evaluate resource configurations and automatically remediate non-compliant resources.
Real-Time Example
Let's consider a scenario where a company, "AmazeOnCloud," wants to set up a new AWS environment that adheres to best practices for security, compliance, and governance.
- Initiating AWS Control Tower: AmazeOnCloud's cloud administrators initiate the setup of a new AWS Control Tower landing zone. They specify the required configurations, such as the number of workload accounts needed, the AWS regions to deploy resources in, and any customized guardrails or SCPs they want to enforce.
- Account Provisioning: AWS Control Tower's Account Factory provisions the management account, log archive account, and the specified number of workload accounts. Each account is preconfigured with the defined guardrails, logging configurations, and default VPC settings.
- Baselining and Guardrails: The specified guardrails are automatically applied across all accounts in the landing zone. For example, a mandatory guardrail could enforce the use of AWS Key Management Service (AWS KMS) for encryption of Amazon Elastic Block Store (Amazon EBS) volumes, ensuring data-at-rest encryption across all accounts.
- Service Control Policies: AWS Control Tower sets up SCPs at the organization root level and applies them to the relevant OUs. For instance, an SCP could restrict the ability to create AWS Lambda functions in specific regions or enforce the use of specific Amazon Machine Images (AMIs) for Amazon Elastic Compute Cloud (Amazon EC2) instances.
- Ongoing Governance: As AmazeOnCloud's development teams start deploying workloads and resources within their respective accounts, AWS Control Tower continuously monitors and enforces the defined guardrails and SCPs. Any non-compliant resources or configurations are automatically remediated or prevented from being created.
- Centralized Visibility: Through the AWS Control Tower dashboard and its integration with services like AWS Config and AWS Security Hub, AmazeOnCloud's cloud administrators have a centralized view of their entire AWS environment's compliance status, security findings, and resource configurations.
- Auditing and Logging: AWS CloudTrail logs all API activity across the landing zone, providing a comprehensive audit trail for security and compliance purposes. These logs are stored in the dedicated log archive account for long-term retention and analysis.
By using AWS Control Tower, AmazeOnCloud can establish a well-architected, multi-account AWS environment that aligns with industry best practices and meets their specific security, compliance, and governance requirements. The service automates the provisioning and baselining of accounts, enforces guardrails and SCPs consistently, and provides centralized visibility and control over the entire AWS environment.
What Happens in the AWS Management Console
When AWS Control Tower is enabled and a new landing zone is created, the following changes occur in the AWS Management Console:
- AWS Organizations: A new AWS Organizations structure is created, with the management account as the organization's root account. The log archive account and workload accounts are created under the appropriate organizational units (OUs).
- AWS Config Rules: Predefined AWS Config Rules are automatically enabled to evaluate resource configurations against the specified guardrails and best practices.
- AWS CloudTrail: A new CloudTrail trail is created in the management account to log all API activity across the landing zone. Additionally, CloudTrail trails are created in each workload account to log account-specific activity.
- AWS Security Hub: AWS Security Hub is enabled in the management account, providing a centralized view of security findings and compliance status across the landing zone.
- AWS Control Tower Dashboard: A new AWS Control Tower dashboard is available in the management account's console, displaying an overview of the landing zone, including the accounts, OUs, guardrails, and compliance status.
- Guardrail Policies: The specified guardrails are displayed and can be managed through the AWS Control Tower dashboard or the AWS Organizations console.
- Service Control Policies (SCPs): The defined SCPs are visible and can be managed through the AWS Organizations console, under the appropriate OUs.
- Account Management: New accounts can be provisioned, and existing accounts can be managed through the AWS Control Tower dashboard or the AWS Organizations console.
- Logging and Monitoring: AWS CloudTrail logs, AWS Config evaluations, and AWS Security Hub findings are accessible through their respective consoles, providing visibility into API activity, resource configurations, and security findings across the landing zone.
Hope this article given good insights about this service and follow me to explore more about AWS cloud computing.
Happy upskilling !!
