How to build retro games in AWS using Sega Genesis Development Kit (SGDK)
Have fond memories of retro gaming classics? Want to know more on how to build new retro games in the modern world? Today, I walk you through how to setup your Sega game builds using AWS cloud.
A Jenkins Environment in which you will need permissions to add agents.
A Code repository that Jenkins can pull from
Game or Demo Game built with SGDK
Intermediate level knowledge of Jenkins, EC2, and S3
Security Group Settings. We chose to create a new security group based upon the seller settings. Within this section give your new security group a name and description. It is not recommended to have your instance open to the public, within our example we’ll be setting the source IP to your local IP for the time being on SSH but leaving port 80 and 443 open to the internet since there is a web portal we need to access.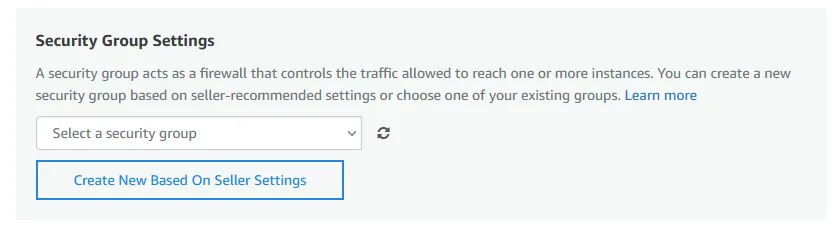
Create a key pair in EC2 you will be directed back to your AWS console. From there, click on the Create Key Pair button located in the upper right hand of the screen.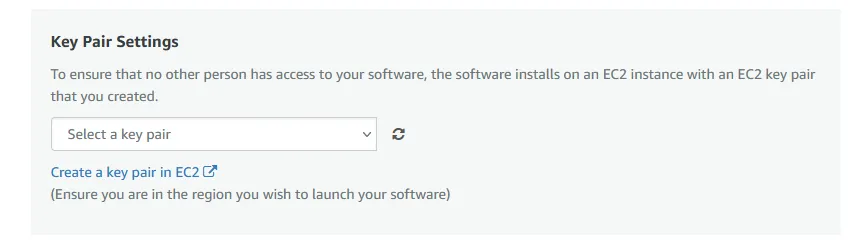
Create Key Pair you should see a similar screen as below. Chose RSA and .pem as your radio options. Give your key a descriptive name such as sgdk-jenkins-key and then click Create key pair at the bottom right of the screen. Take note of where you have saved your .pem key as it will be used for a later step.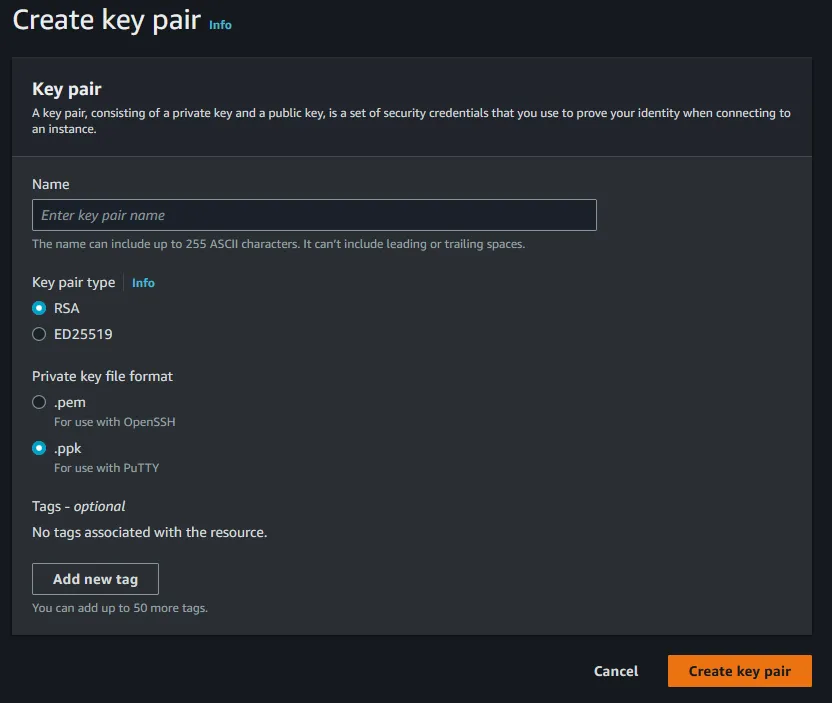
Key Pair Settings and you should see the new key pair show up. Make sure the new key is selected and click on the Launch button.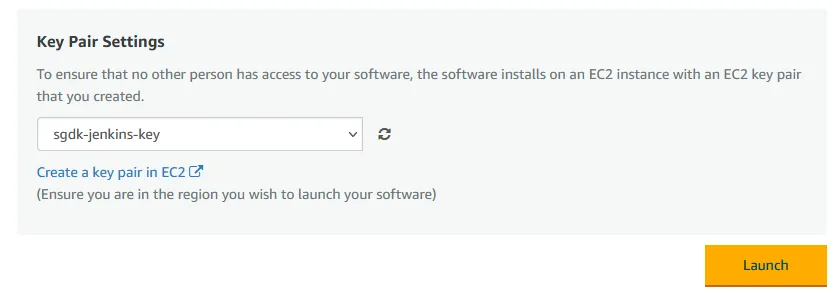
Usage Instructions button.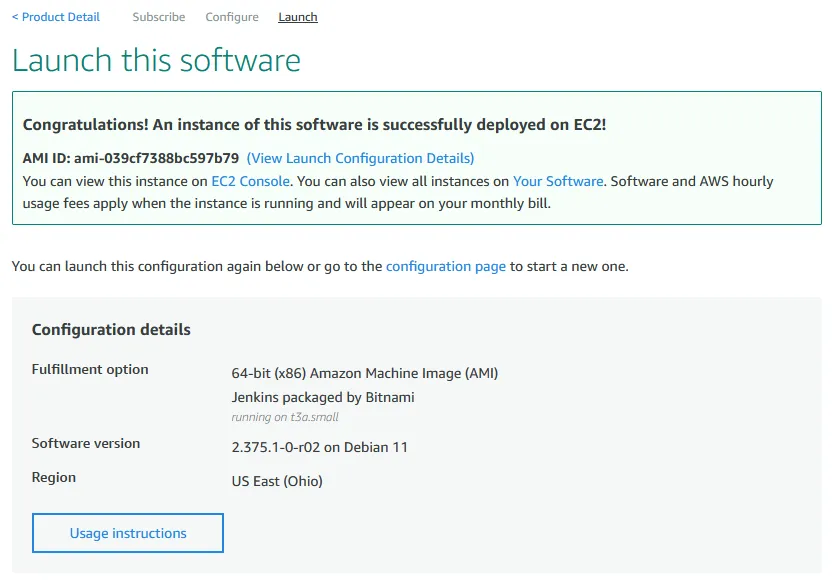
Usage instructions button you should see a popup that looks like below. Click on the link mentioned within the popup about “...learn how to get your password” and open within a new tab. You may also click the link here.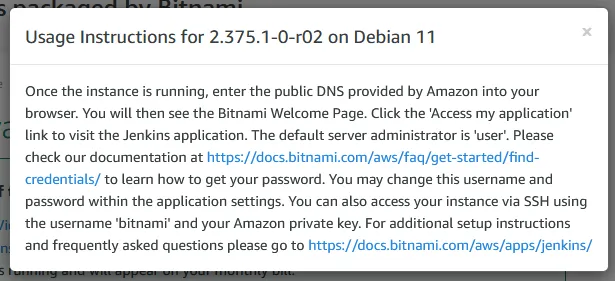
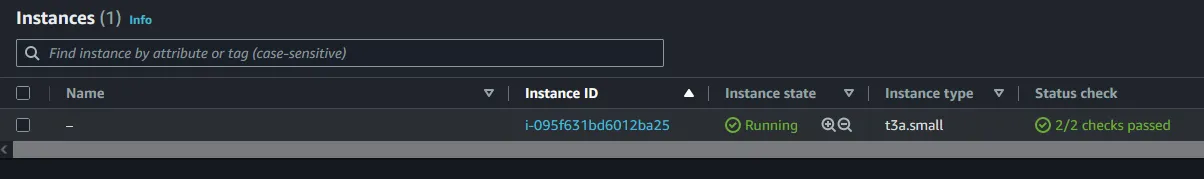
Public IPv4 DNS. Click on the open address link within a new tab (NOTE: you maybe warned that it’s an unsafe site, you may proceed to the site anyhow as this is your newly created instance).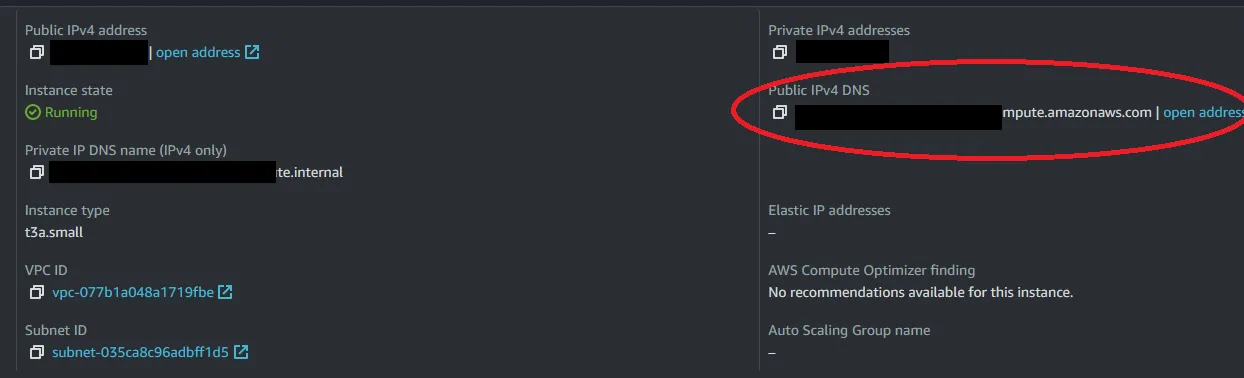
Actions in the top right of your screen. Select Monitor and troubleshoot. Then select Get System Logs.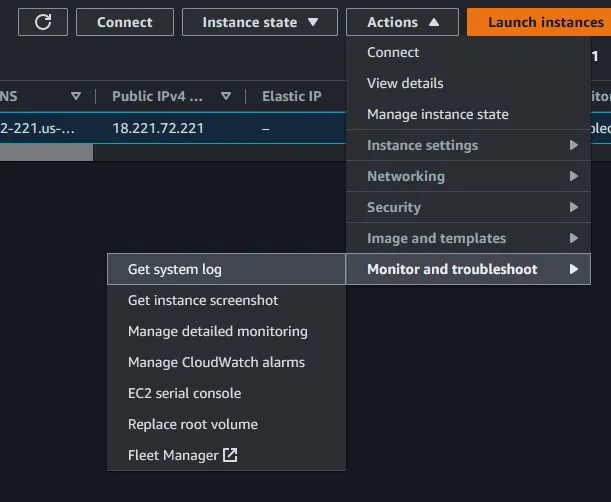
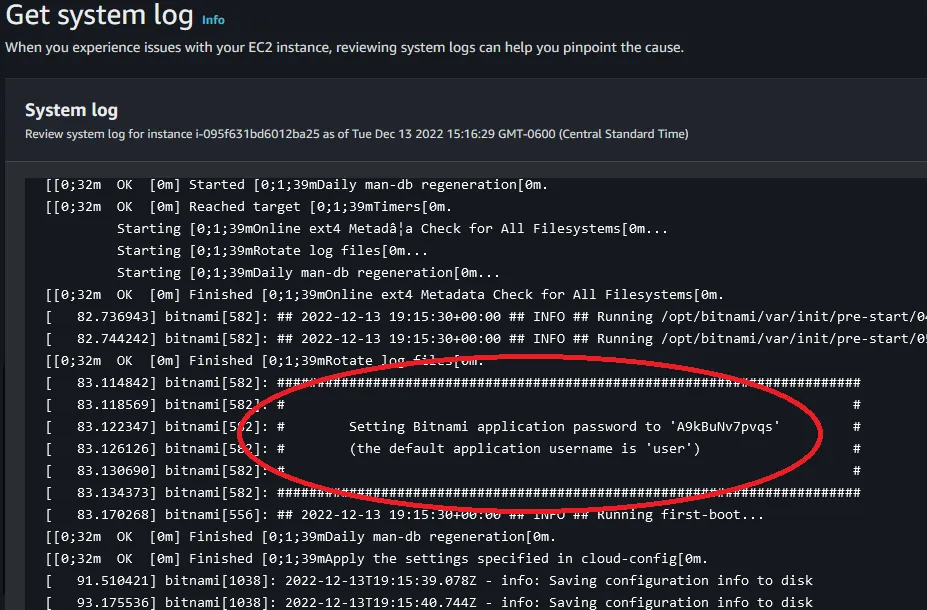
user drop down at the top right of the page. Select Configuration. Then scroll down to enter in your new password.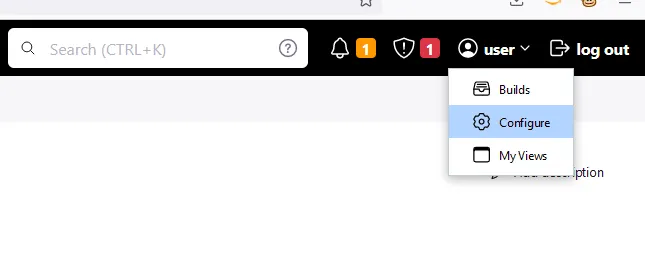
us-east-2. We kept all the defaults the same (including blocking all public access).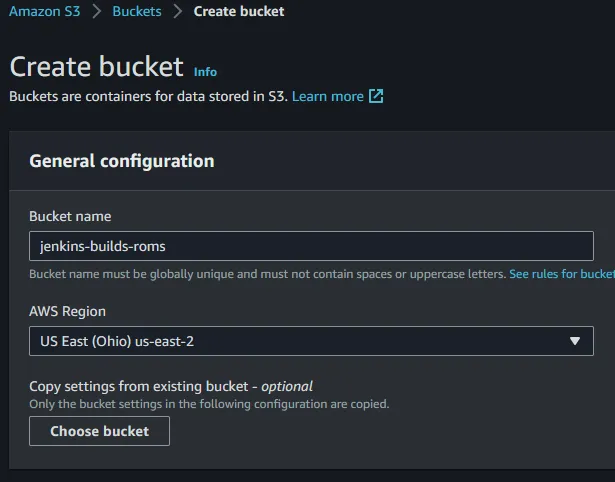
Security Credentials tab of that newly created user and create access key (please download and save the .csv file as you will need both the access key and secret key for the next steps within Jenkins).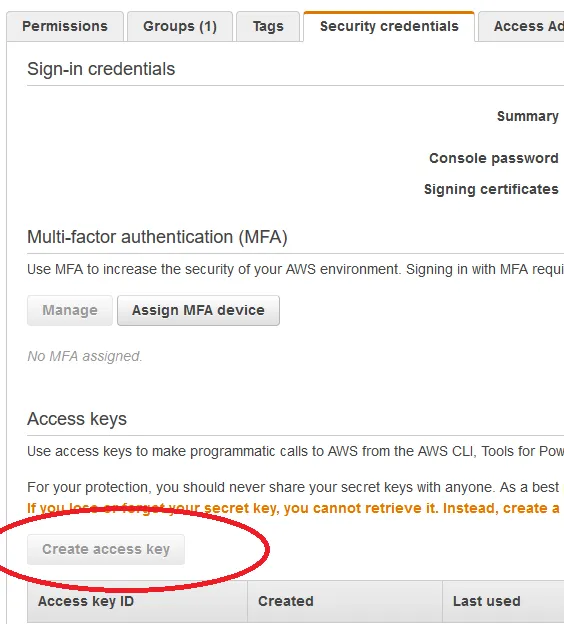
launch instance button to get started. (NOTE: Make sure you create the new agent within the same region as your Jenkins Controller).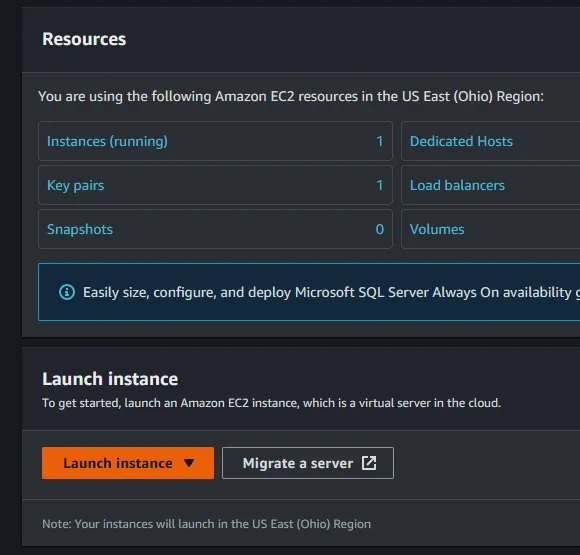
sgdk-windows-agent. Then underneath the Application and OS Images drop down, select windows within the Quick Start tab and you may leave the default option of (Microsoft Windows Server 2022 Base - Free Tier eligible). (NOTE: The SGDK only runs on Windows).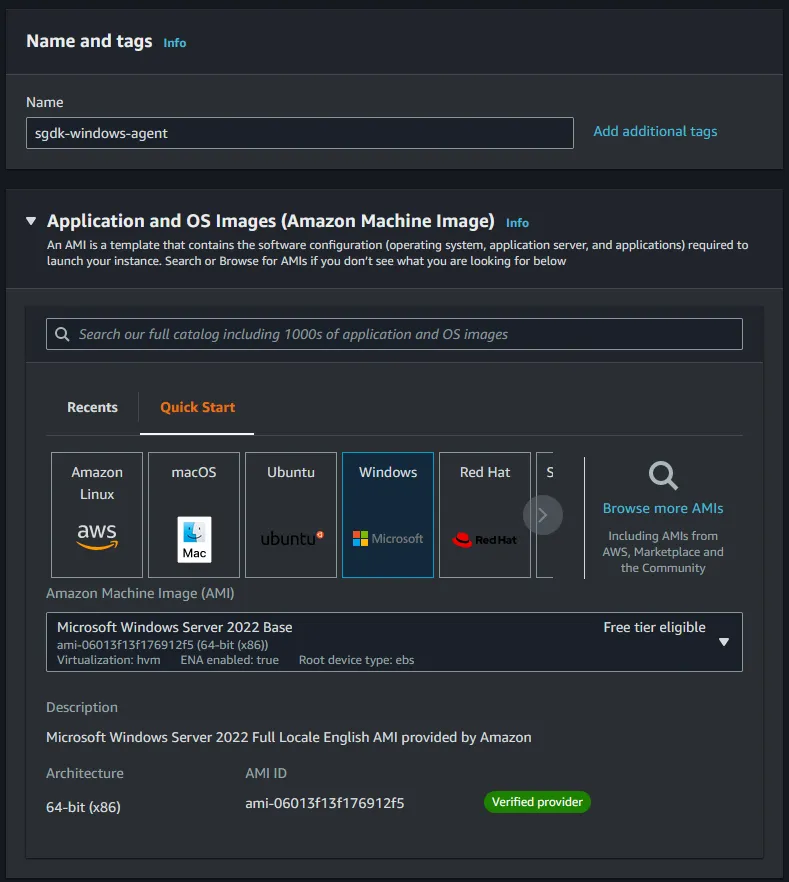
Configure Storage and Advanced Details alone for now, but for future reference within Advanced Details is where you can specify spot instance in order to save cost.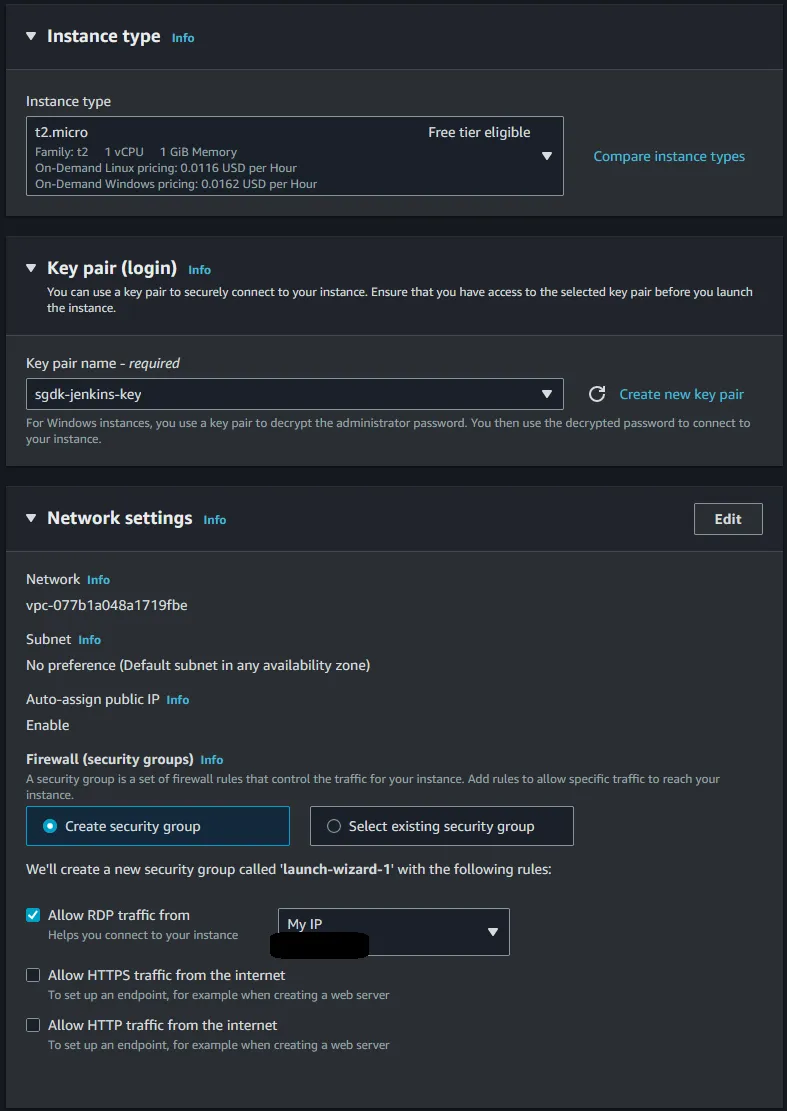
Launch instance located on the right side of the page underneath the summary section. This should only take a few seconds to create but may take a few minutes to initialize. You should see the screen below if everything was successful. When you see the success screen feel free to click on the instance id link or you may navigate back to instances and see your newly created agent instance within the list of instances.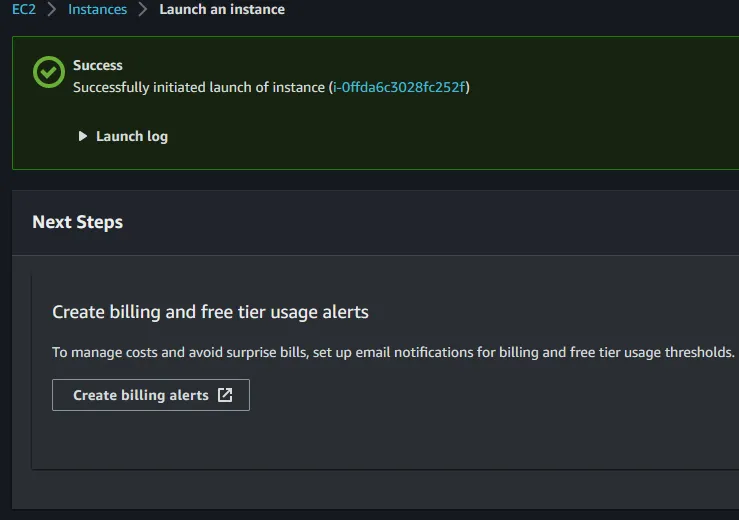
connect. Click connect to bring up options for that instance.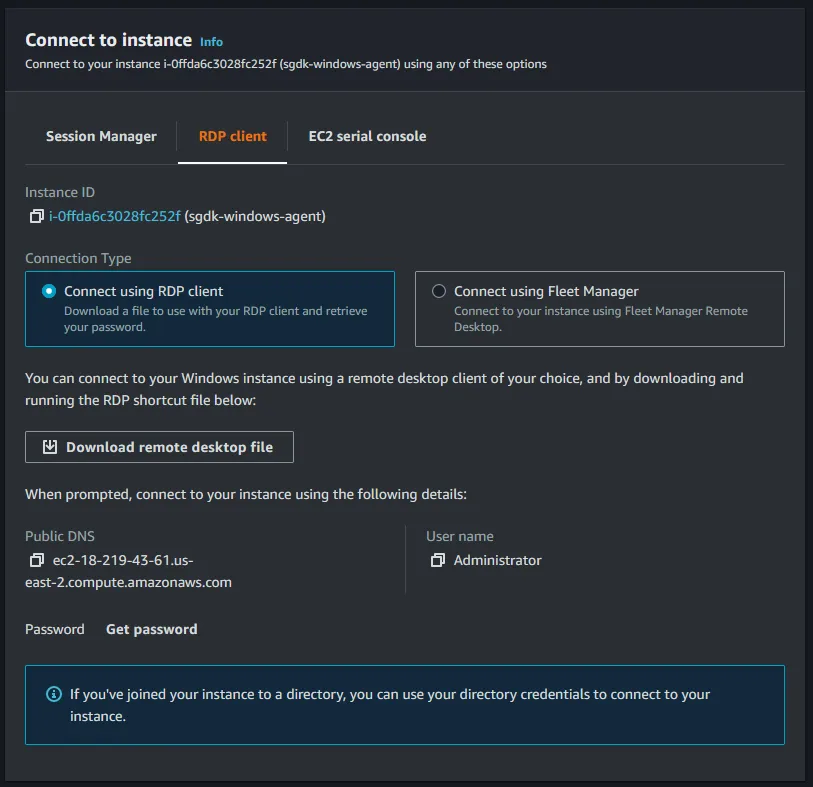
Download remote desktop file to your local machine. Before you can connect you will need to get the Administrator password. To get the password click on the Get password section.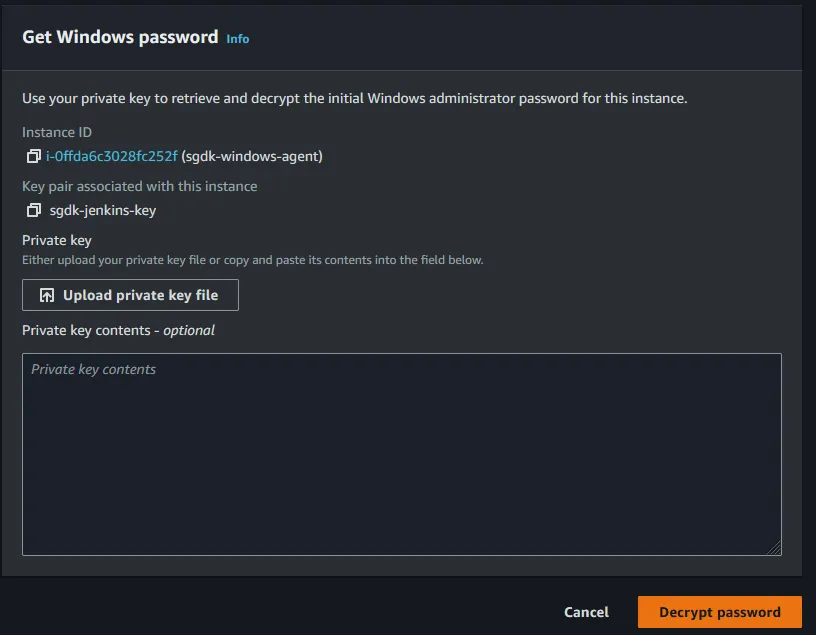
upload private key file. After doing that you should see your RSA private key contents populate the textfield and now you can click Decrypt password button.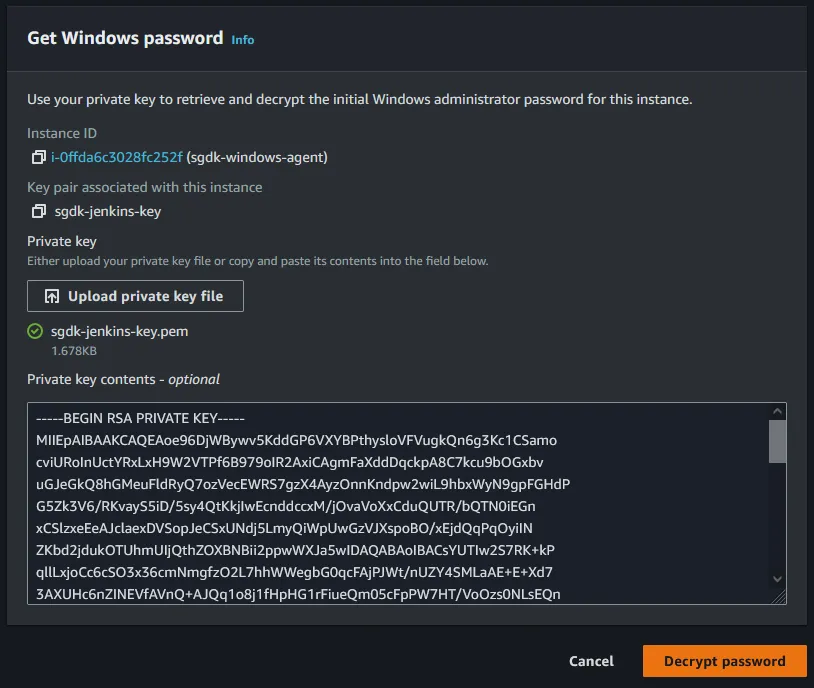
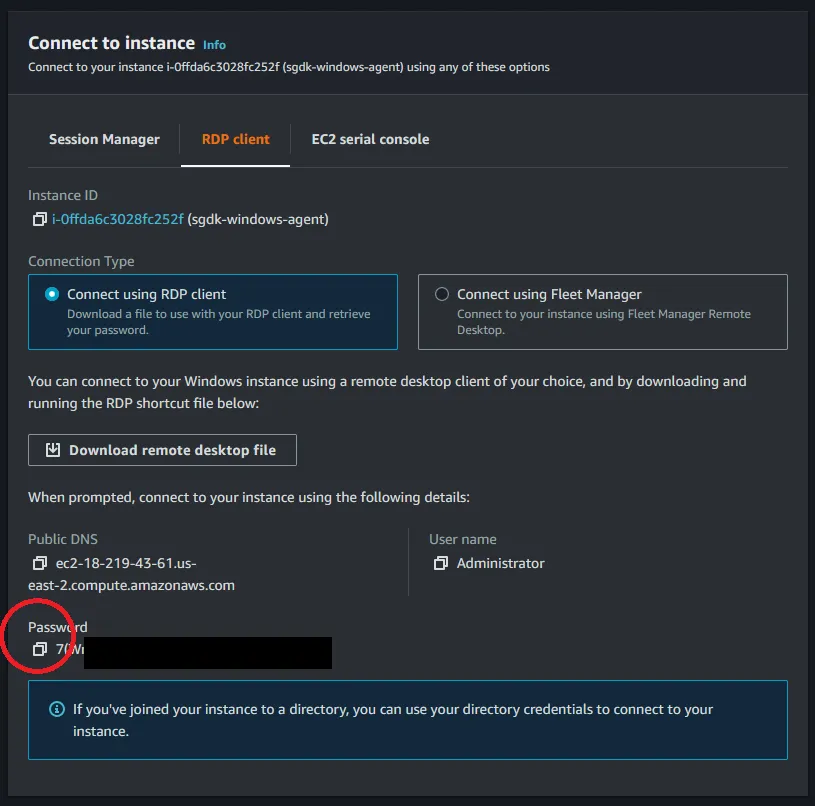
jdk-17_windows-x64_bin.msi. Then after installing Java we need to install Git and at the time of writing this blog we had installed Git-2.35.1.2-64-bit.exe. Now, you can confirm that both are installed by pulling up command prompt and typing in Git —version and java -version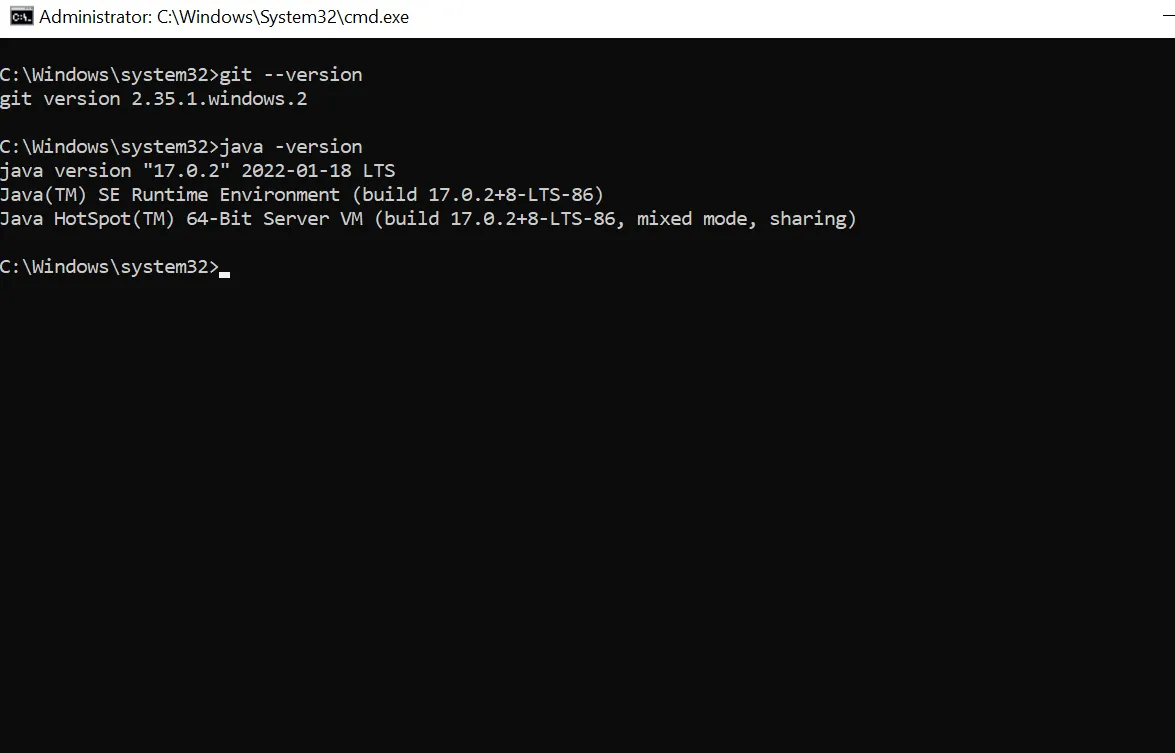
Jenkins_Agent_Node as we will need this later for our SGDK libraries as well as the agent.jar file that Jenkins uses to communicate with the agent.sgdk on the C drive of your windows instance(You can technically place this anywhere; but just remember the file path as you will need that later).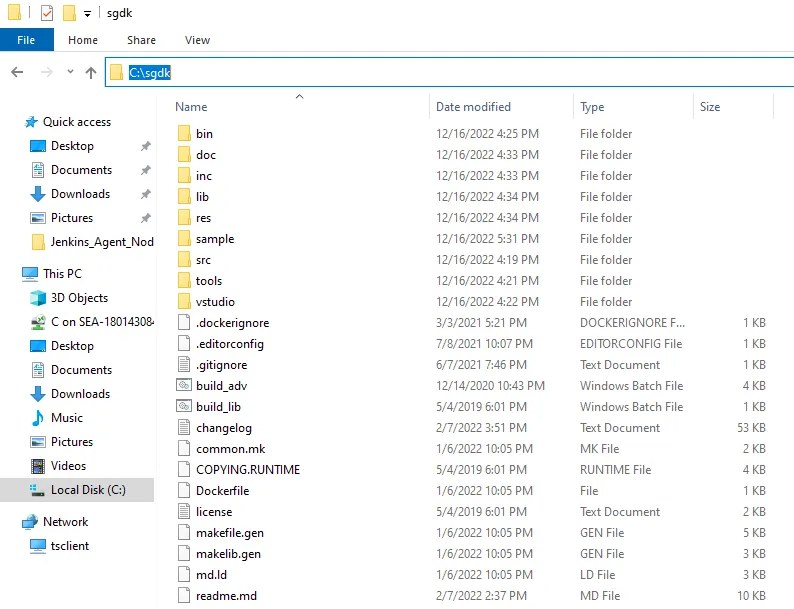
.\bin\make -f makelib.gen
number of executors section and change the value from 2 to 0 and click save.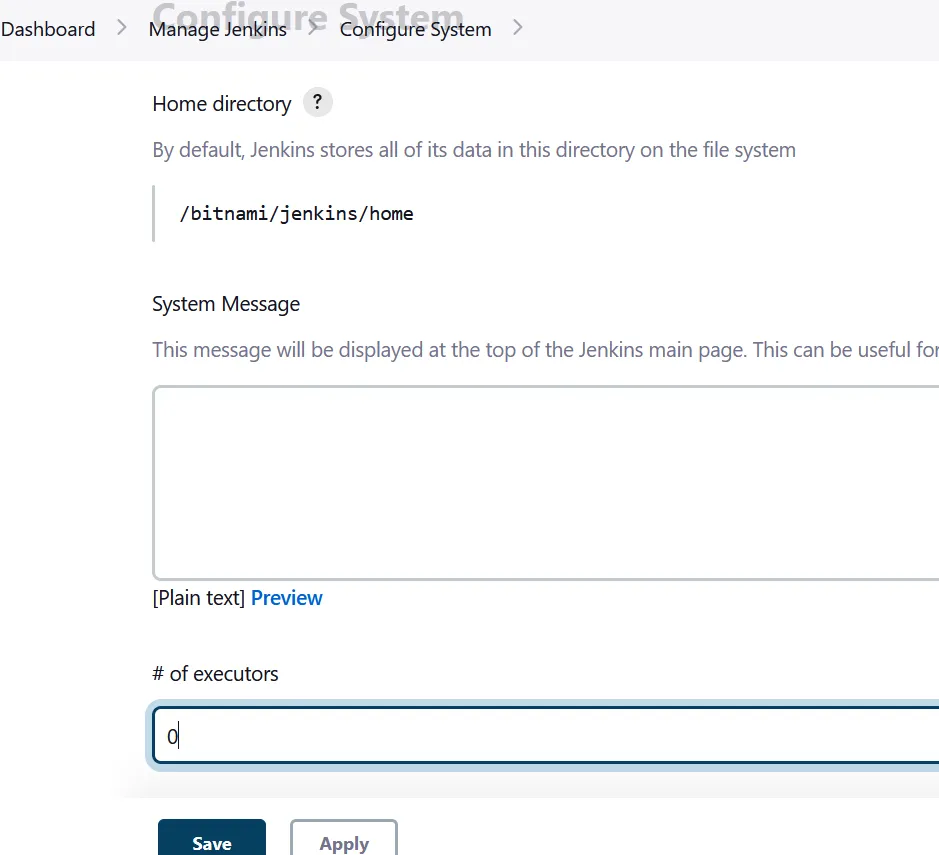
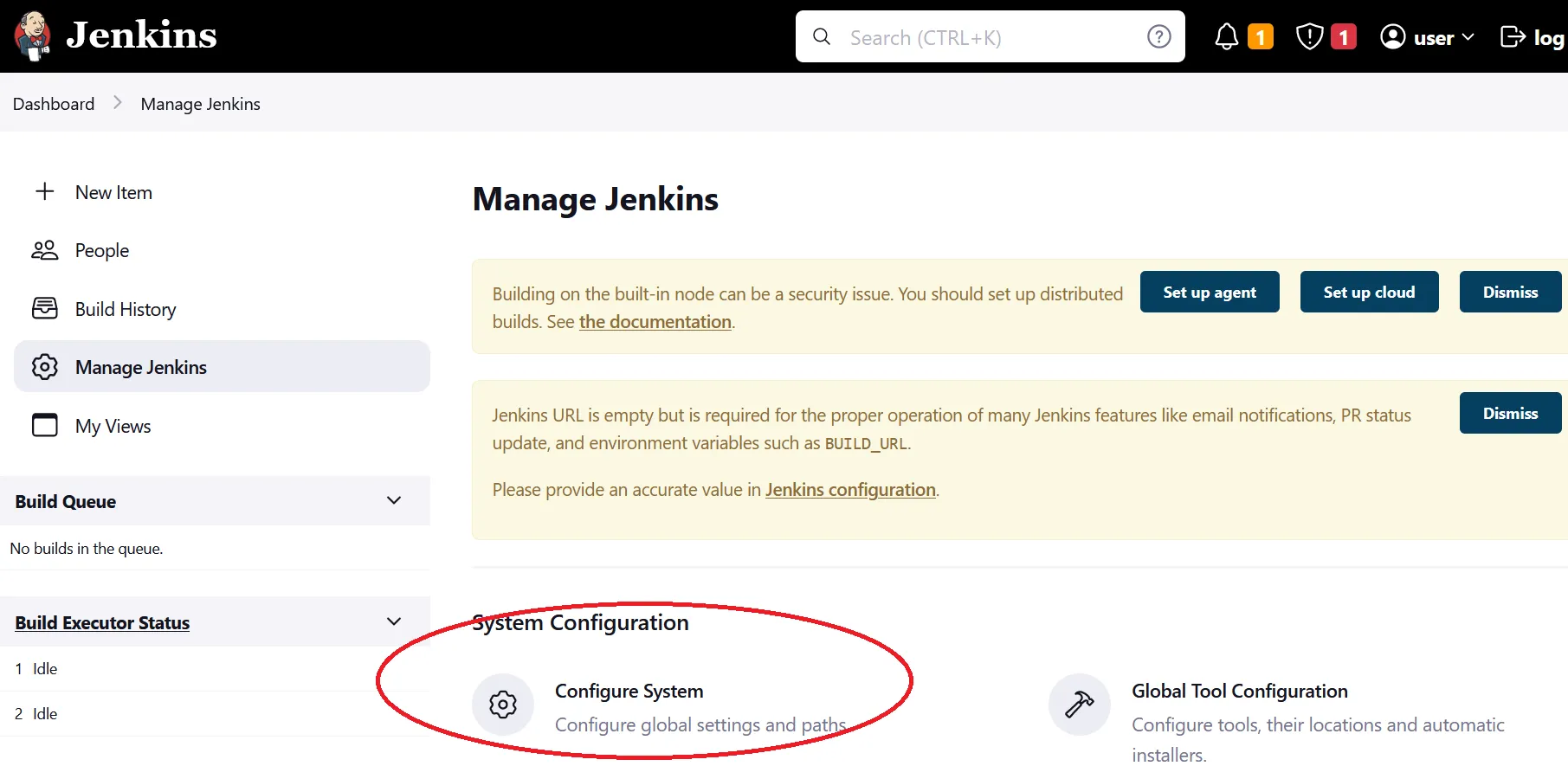
Manage Jenkins to setup remote access for our agent. Once you are back to Manage Jenkins scroll down until you see Configure Global Security. Click on that and then scroll down to the section that says Agents. Here we are going to select a specific port number, so select the fixed radio toggle and put in the port number 36587 (NOTE: you can use other ports if you wish, but for this tutorial we have chosen port 36587). Then click save down below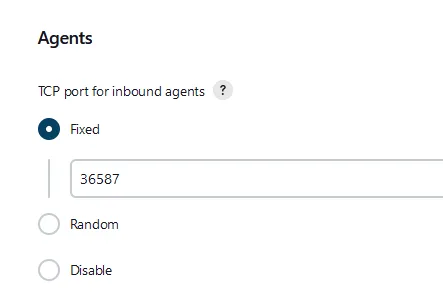
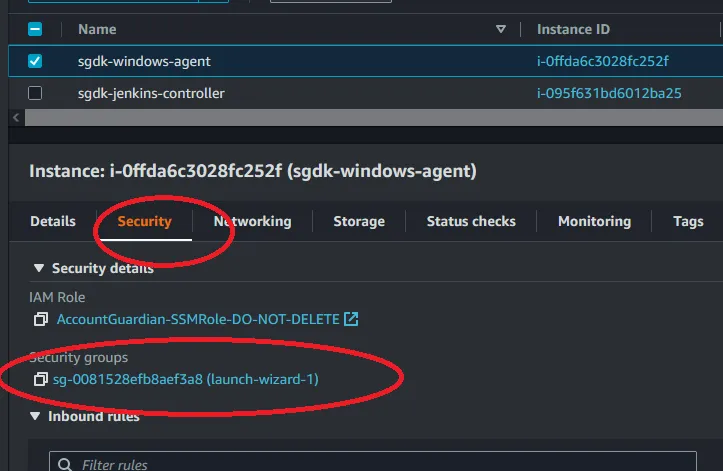
inbound rules and then on the far right click on Edit inbound rules.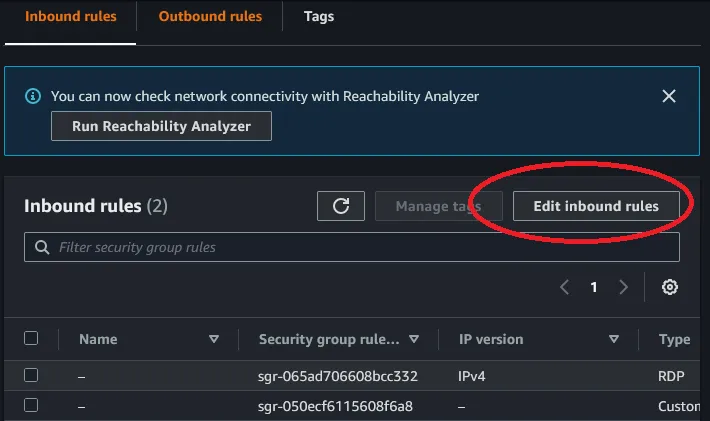
Custom TCP, Port range is set to 36587, and the source will be set to the Jenkins Controller’s security group (NOTE: you can type sg- to filter the options down to just security groups). When that is all in place, click Save rules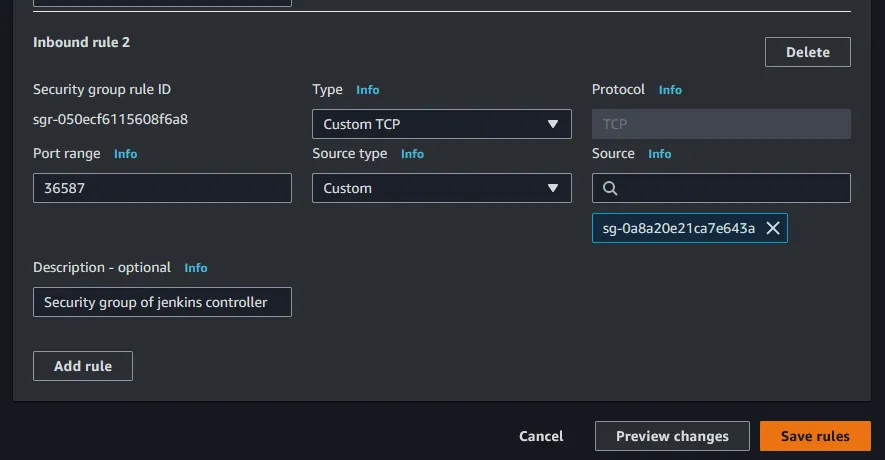
security tab and then click on the security group that is attached. When you are in the security group go ahead and click Edit inbound rules like before. Add a new rule with the Type set to Custom TCP, Port set to 36587, and the Source set to the windows agent’s security group. Then click Save rules. The new rule should look something like below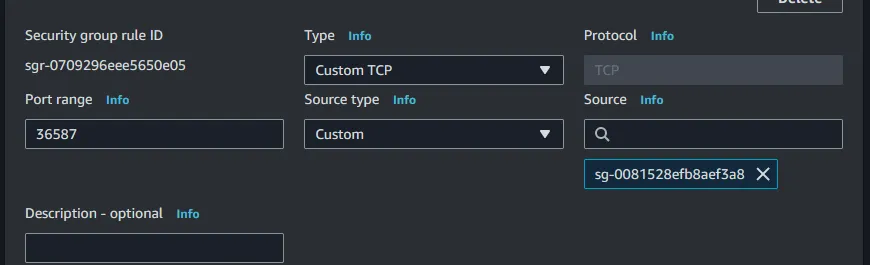
Set up an agent.
sgdk-windows and make sure to select the Permanent Agent radio button; then click create.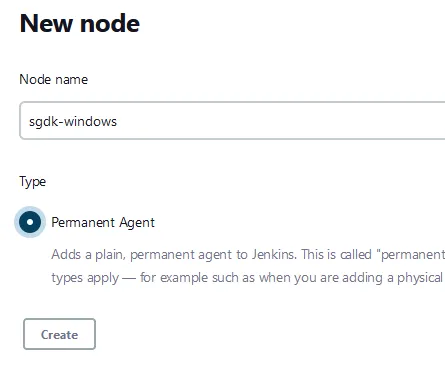
New Sega Genesis Build Agent. Remember that directory we created back on the windows agent (C:\Jenkins_Agent_Node)? We are going to use that folder path within the Remote Root Directory text field. For Labels put in sgdk and change the launch method to Launch agent by connecting it to the controller. Then click save. We will configure more later on when we connect our Jenkins environment to our code repository, but for now we want to make sure Jenkins can see the new agent. After saving you should see a similar screen like below.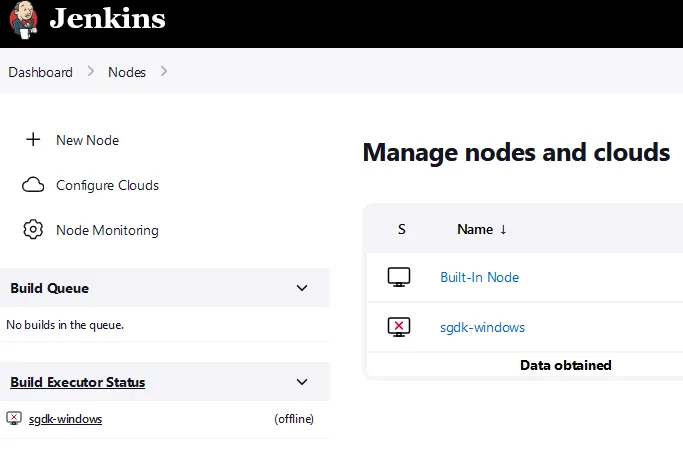
sgdk-windows. You should see a screen similar to below, but it will contain the specific URL to your instance. We will be using the top option Run from agent command line within this tutorial.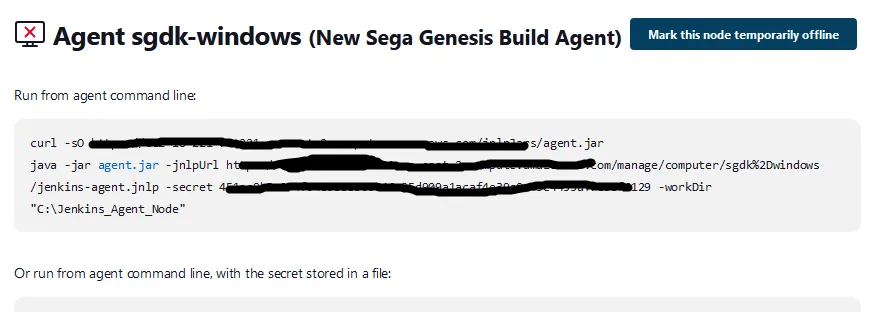
agent.jar file is a hyperlink? Go ahead and click on that link to download the agent.jar file. Then move that agent.jar file to your windows agent into the C:\Jenkins_Agent_Node folder. that we had created previously. The script will need that in order to establish connection to the Jenkins Controller.RunInCMD.txt and placed it on the desktop) within your windows agent as we will use this later. At the end of the script (for this tutorial purposes) we will be adding in the -noCertificateCheck flag. So, your script should look like this below.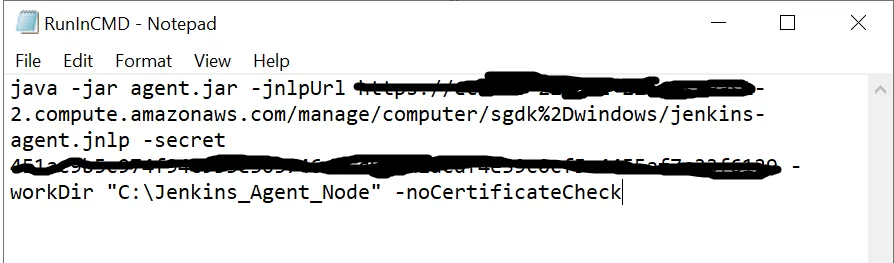
agent.jar file on our windows agent, let’s start the agent and see if our Jenkin’s controller see’s it come online. Within your windows agent open up a command prompt (NOTE: make sure you are in the same folder as the agent.jar file) and copy and paste the script that we had previously created and run it. If all was successful you should see a similar screen as below.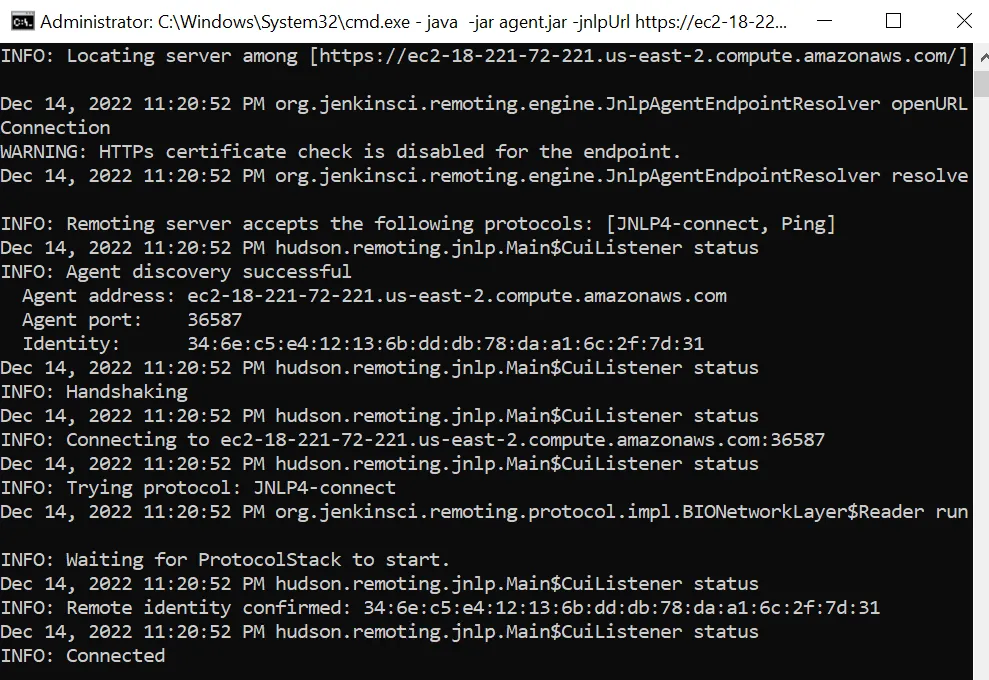
Dashboard. If everything went well, you should see your new windows agent sitting idle and connected. See the screen shot below.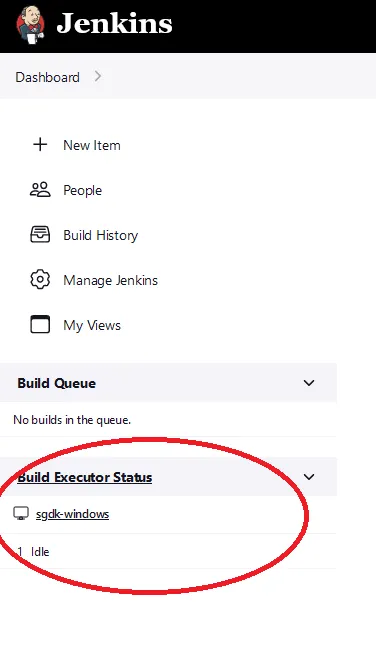
edit profile. Then select Access Tokens. We are going to generate a new token that will be used within Jenkins to access our project.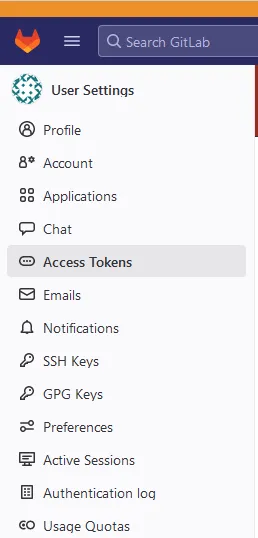
api checkbox and then click Create personal access token. Please remember your Token Name and Token that is generated. In our example we are using sgdk-blog-test as our token name.Manager Jenkins → Manage Plugins. From here we are going to install the GitLab Plugin, so go to the available plugins section and search for GitLab Plugin and select the checkbox. Choose the download now and install after restart option. Restart your Jenkins instance (You can do this by going into the AWS Console again, going to your list of EC2 instances and selecting the Jenkins instance, and then in the top right corner click on instance state to select reboot instance.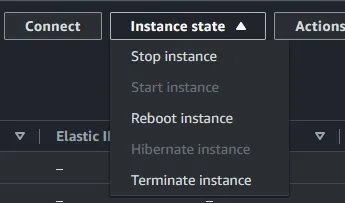
Manage Jenkins again. Now, depending upon what version of Jenkins you are running you maybe prompted with other libraries that need to be installed for the GitLab plugin to work (be sure to download and install them as well).Install without restart.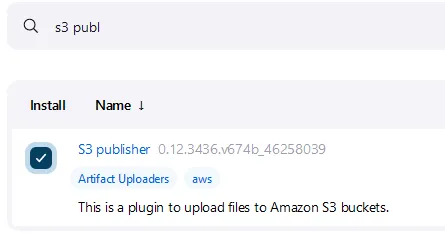
Manage Jenkins from the dashboard page. Then click on Configure System Scroll all the way down to the bottom until you see Amazon S3 Profiles Now give your profile a name and paste in your access and secret keys and then test the connection. If all was successful you should see the “check passed!” message. Now we will be ready for our publishing step later on in the tutorial.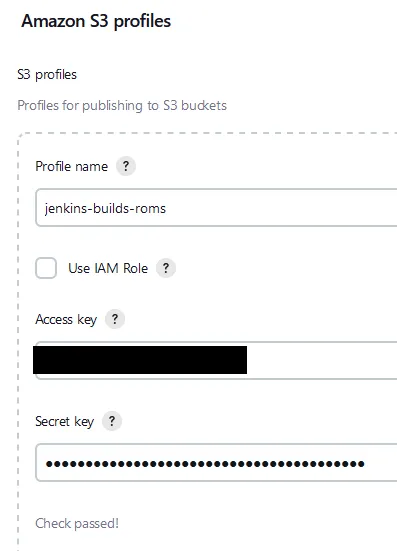
Manage Jenkins click on Configure System. In the GitLab section, select Enable authentication for ‘/project’ end-point. Fill out the connection name and the Gitlab host URL. Then, click on the add button to add in your credentials that we created previous within GitLab. This will be used by Jenkins to communicate to GitLab.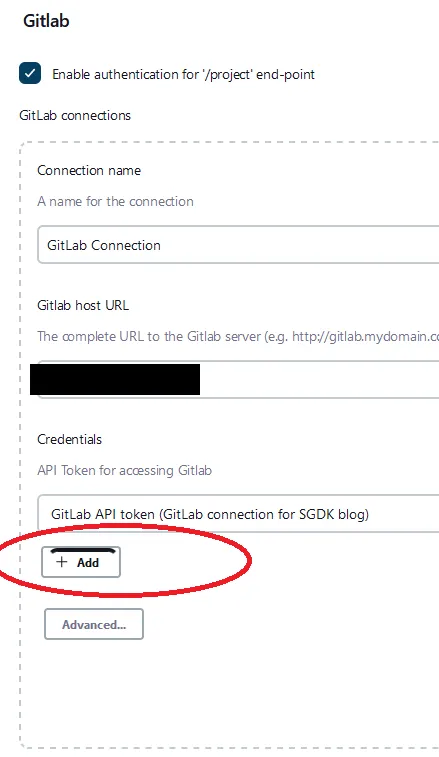
Kind option to GitLab API Token and keep the scope at Global (Jenkins, nodes, items, all child items, etc). Paste in the GitLab Token you have previous saved within the API Token field. You can leave the ID field blank as that will be auto generated. Feel free to fill in the description as well.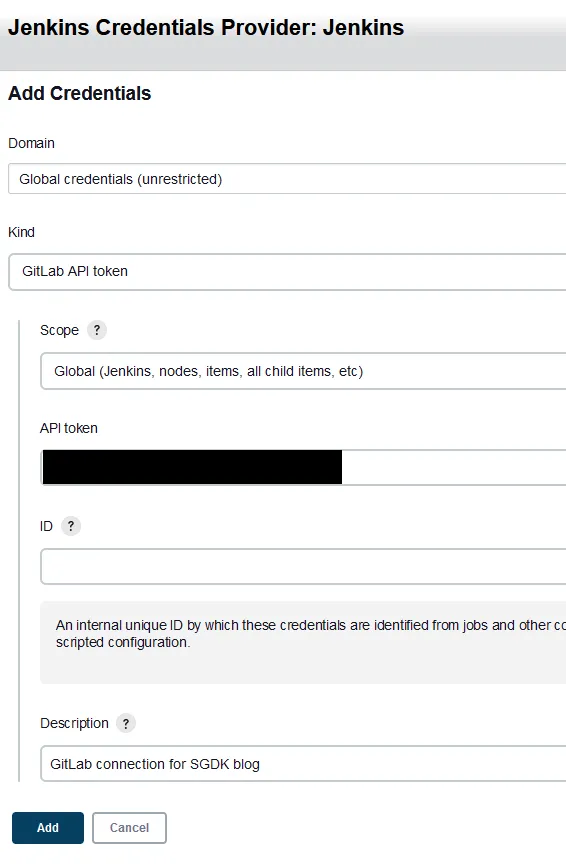
Test Connection button. You should see success if all went well. Now let’s navigate back to the Jenkin’s dashboard to create our first pipeline.+ New item at the top left of the dashboard screen and from here enter an name for the Jenkins project. In this tutorial we will be using the Freestyle project option. Once selected and a name is given go ahead and click on OK. (NOTE: Remember the Jenkin’s project name, you will need this later on within GitLab)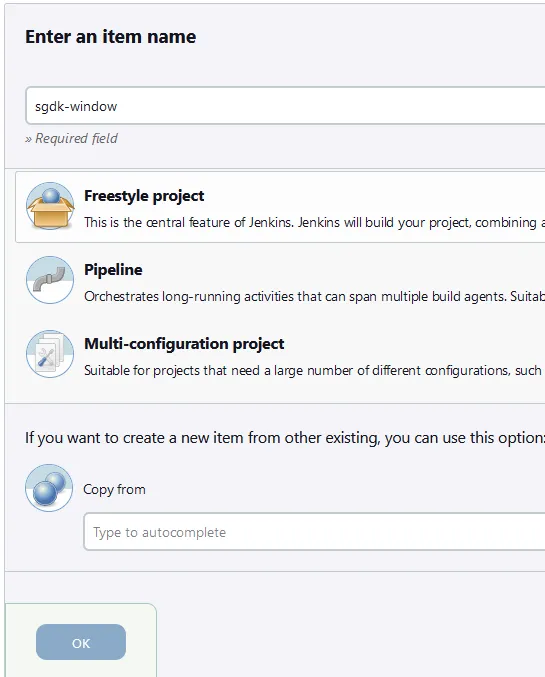
GitLab Connection. Make sure the drop down selection is set to GitLab Connection. Then select the Restrict where this project can be run checkbox and specify the label with sgdk.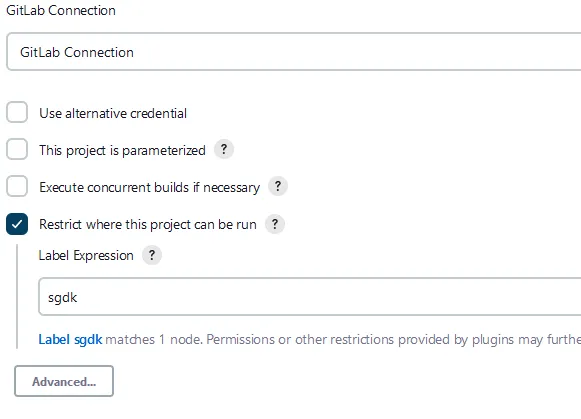
source code management section, select the Git radio option. Within the Repositories section fill in the URL to your git repository hosted in GitLab within our example. Underneath the Credential section we will be adding another set of credentials so go ahead and click the +add button. From here we will leave the Kind option set to Username with password. In the username field put in the GitLab Token Name that you generated previous (in our example we used sgdk-blog-test) and within the Password supply the GitLab Token. Then click Add.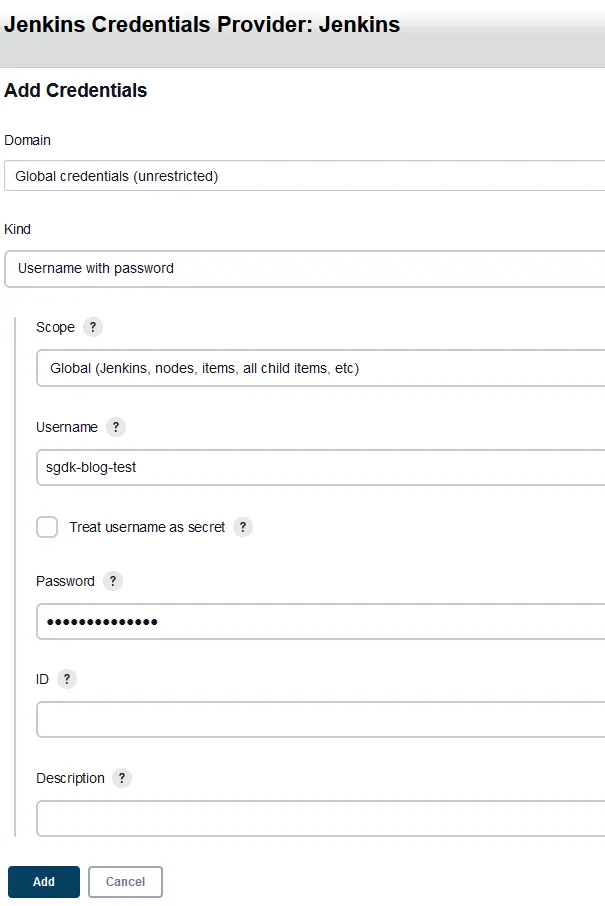
main). Your Source Code Management screen should look similar to the image below.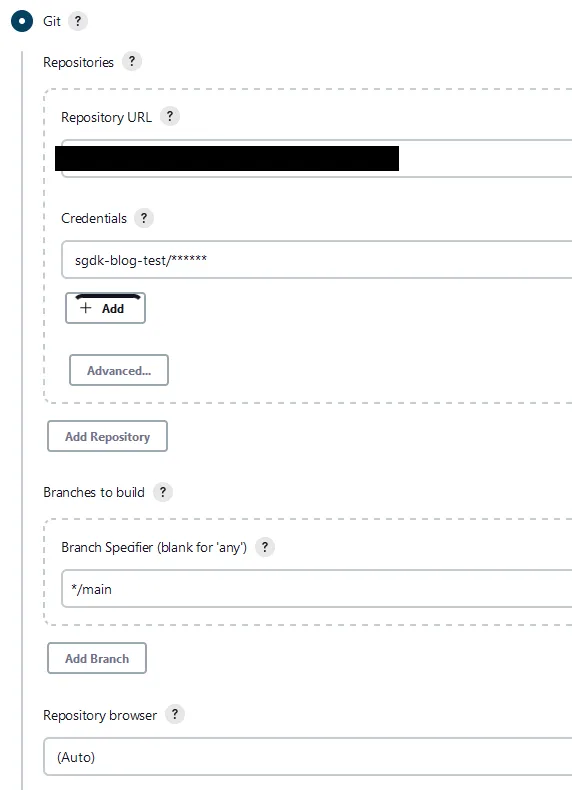
Build Triggers, select the option Build when change is pushed to GitLab. Enable the GitLab triggers you wish to trigger your build events. In our example we selected the Accepted Merge Requests and Closed Merge Requests options. Whenever these events occur within GitLab it will trigger our build within Jenkins. Your screen should be similar to ours below.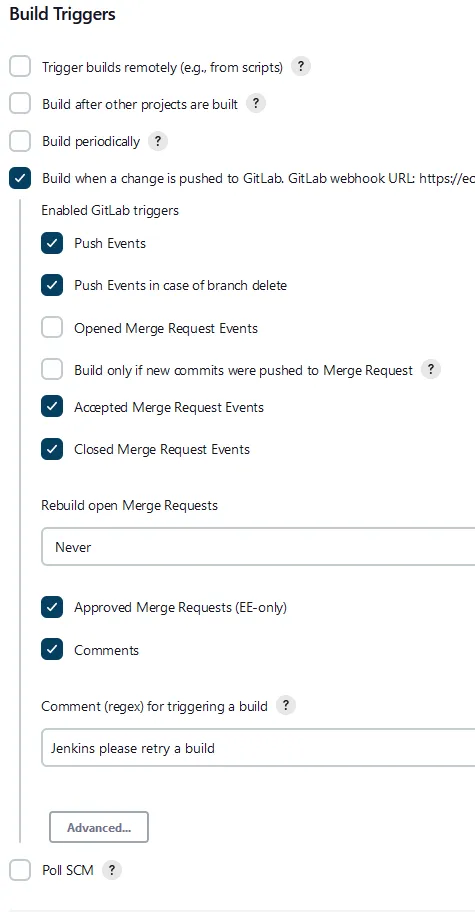
cd C:\Jenkins_Agent_Node\workspace\sgdk-windows & del rom.bincd C:\Jenkins_Agent_Node\workspace\sgdk-windows & C:\sgdk\bin\make -f C:\sgdk\makefile.gen & cd out & copy rom.bin C:\Jenkins_Agent_Node\workspace\sgdk-windows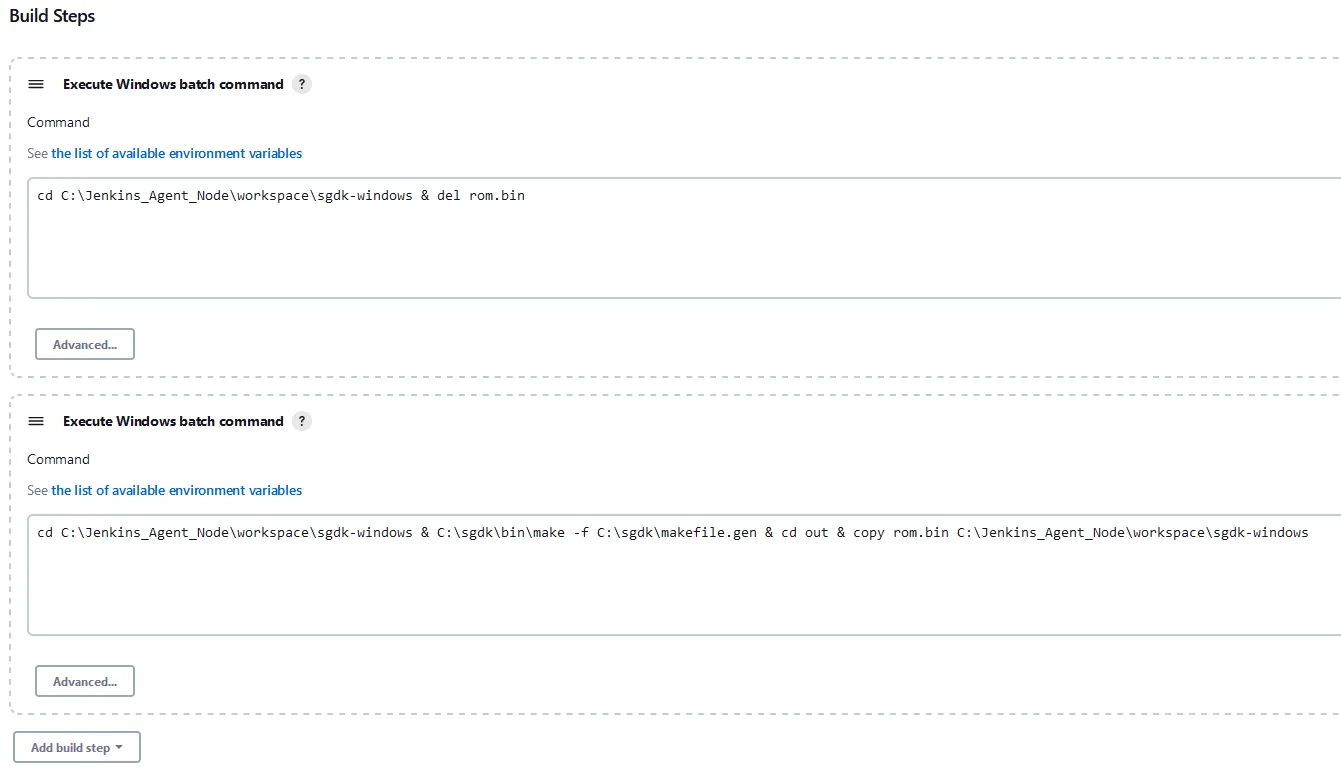
Publish status to GitLab since we are using GitLab (If you are not using GitLab you may skip that step). The second will be Publish artifacts to S3 Bucket. Add both of those new by clicking on the Add post-build-action button at the bottom of the page.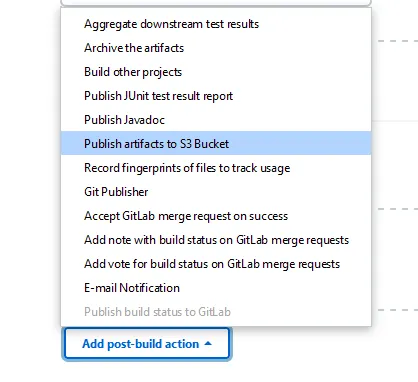
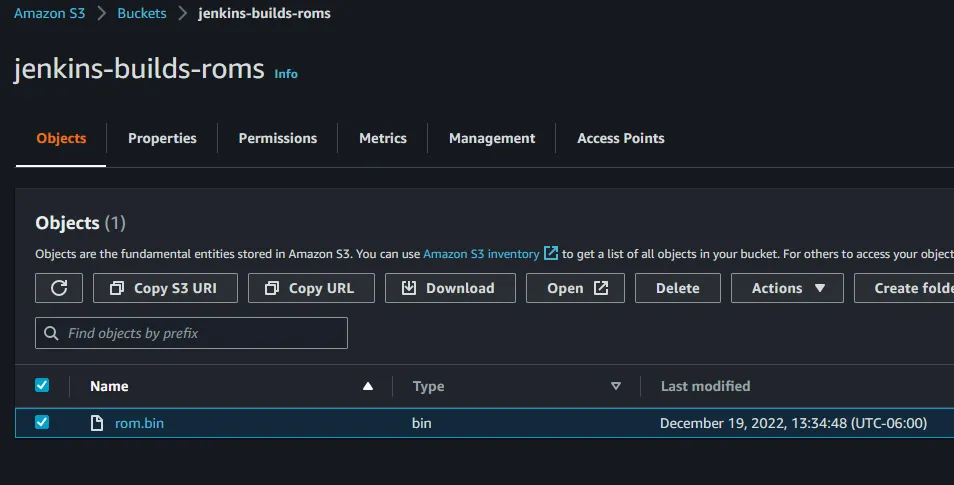
Add underneath Files to upload section.Source let’s put in the file path that we copied the rom.bin file to during our build step. So in our case that path is out/rom.bin. Be sure you put in the name of our newly created bucket from earlier within the Destination bucket field (we used jenkins-builds-roms). Leave the storage class set to standard and make sure you select the correct region that the bucket was created in (in our case we are using us-east-2). Lastly, check the box No upload on build failure. Your setup should look similar to the image below. Make sure to click save or your changes will be lost!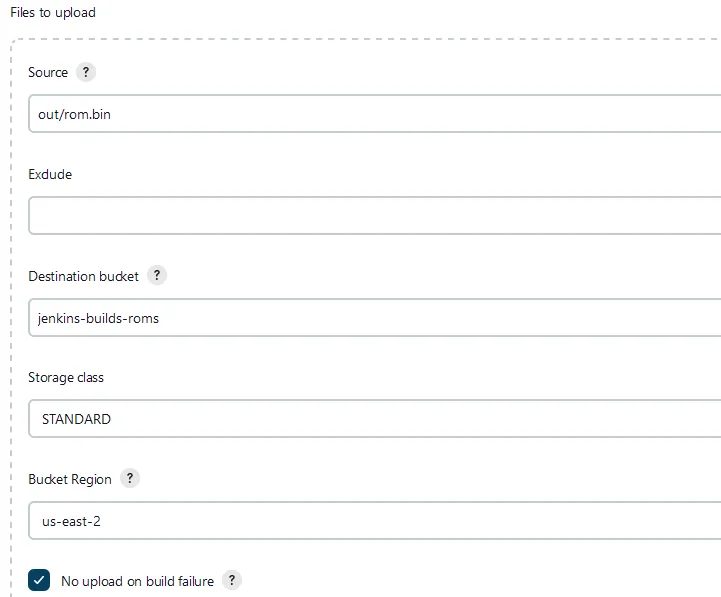
build now action).agent.jar file before executing the command script via command window.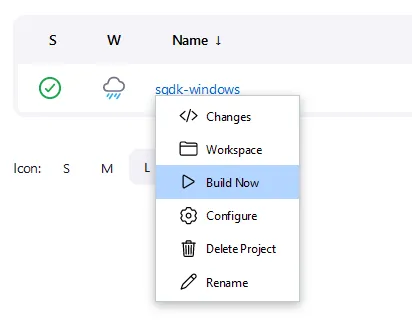
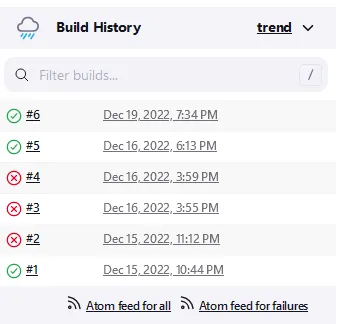
Console Output to see what happened. You should see a similar output like below with a Finished: SUCCESS message at the bottom.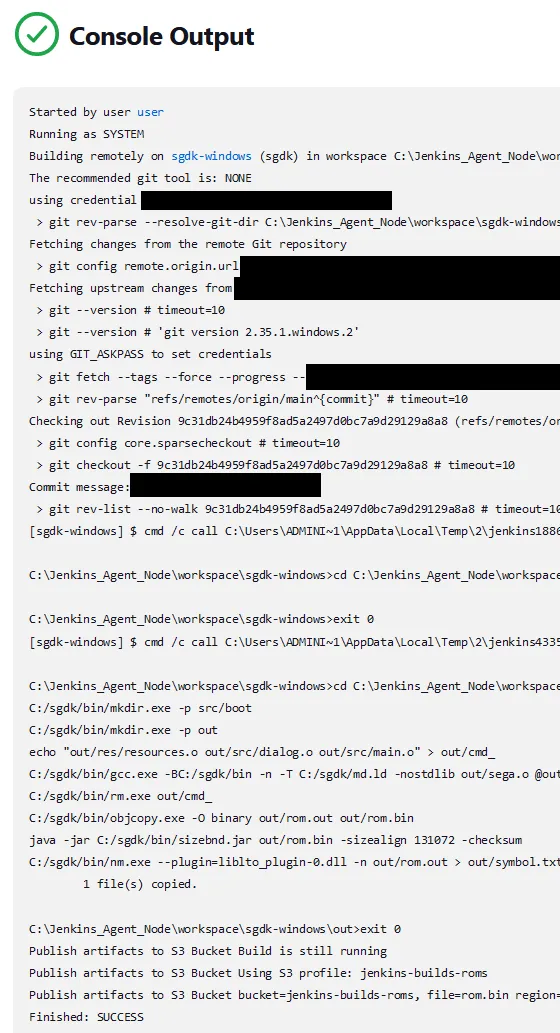
- sgdk build agent offline - If your agent reboots or if the command window running the agent.jar file on the agent closes out you will need to open a new command prompt to run the agent.jar file again. Make sure that when you run the agent.jar script that you have navigated to the file path that the agent.jar file lives.
- sgdk fails to build on the agent - Make sure that all the files have been copied to the sgdk folder on the agent. Also, might want to confirm that you had built the library files before trying to build any roms. You can build the library files by revisiting Step 13 underneath the Setting up your SGDK Build Agent section.
- Job fails to publish to S3 - Make sure that your IAM User has the proper write permissions to that S3 bucket. Also, make sure that you have the correct access and secret key. Be sure to test your profile’s connection during step 5 of Connecting and configuring section. Also, make sure that the rom.bin file was successfully buit as we previously configured S3 publishing to not publish on failures.
- OHSAT Games - produces a lot of great tutorials on getting started with SGDK.
- SGDK Info - GitHub repository with more information on the open source library along with other resources on how to get started.
Any opinions in this post are those of the individual author and may not reflect the opinions of AWS.
