Can We Use aws:SourceVpc Condition Without a VPC Endpoint?
How AWS IAM policies work with VPC? This post walk you through what is under the hood.
aws:SourceVpc condition requires a VPC endpoint to work?".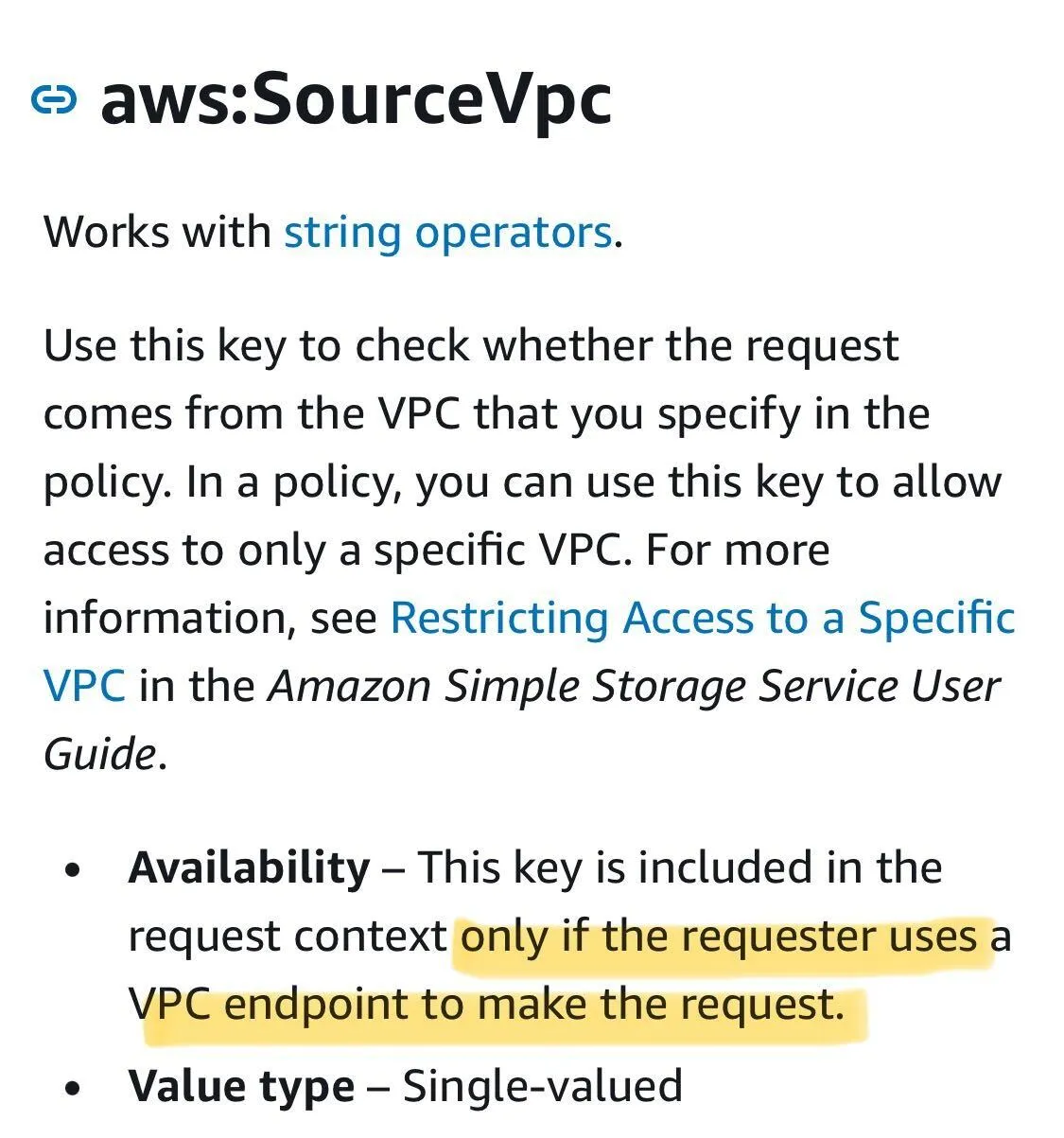
aws:SourceVpc, there are still some confusion. Luckily, I attended a chalk talk session in last year's AWS re:Inforce about this topic. So, I think it's time to share what I've learned.
- The route of a network request goes within AWS
- The way IAM knows the API request's context
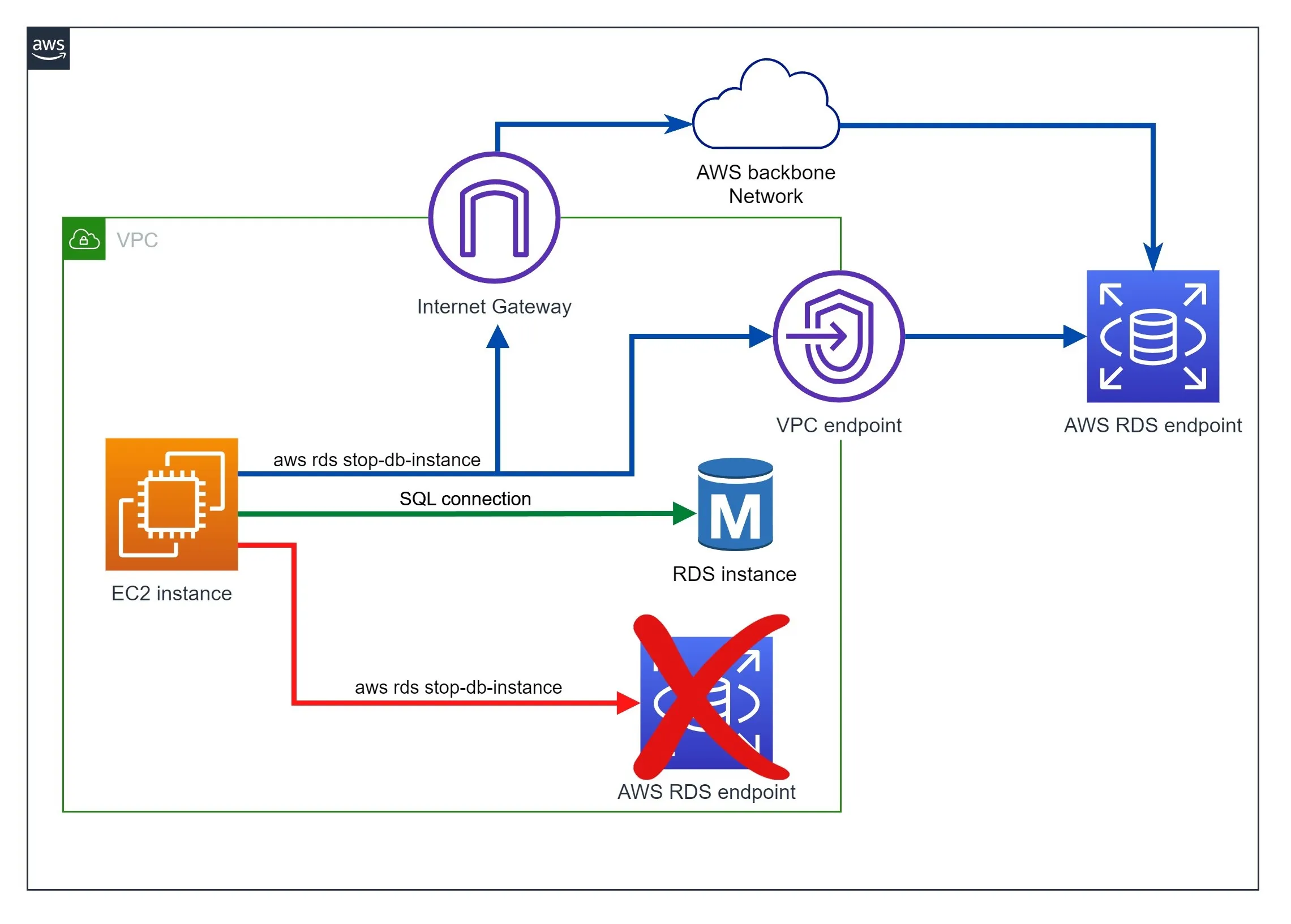
aws rds stop-db-instance from the EC2 instance), it cannot stay within the VPC.rds.us-east-1.amazonaws.com), which is owned by AWS and sits outside of the VPC. (i.e., The CLI is talking to AWS, "Hey! I want to stop that instance, please do it").aws:MultiFactorAuthPresent is added inside the session token because when we sign in, the STS service knows if we have MFA authentication and injects this information into the session token.aws:SourceIp is added when the request reaches the API endpoint because the endpoint can inspect the IP header and determine which IP the request is coming from.aws:MultiFactorAuthPresent because it doesn't know how the user login in the first place. We also cannot expect the STS service to add aws:SourceIp into the session token because it won't know where it will be copied and used to sign subsequent API requests.aws:SourceVpc context. Who should add this to the request?aws:SourceVpc context is added when the API call goes through the VPC endpoint.
aws:SourceVpc context is added by the VPC endpoint. So does it really mean "Source VPC"?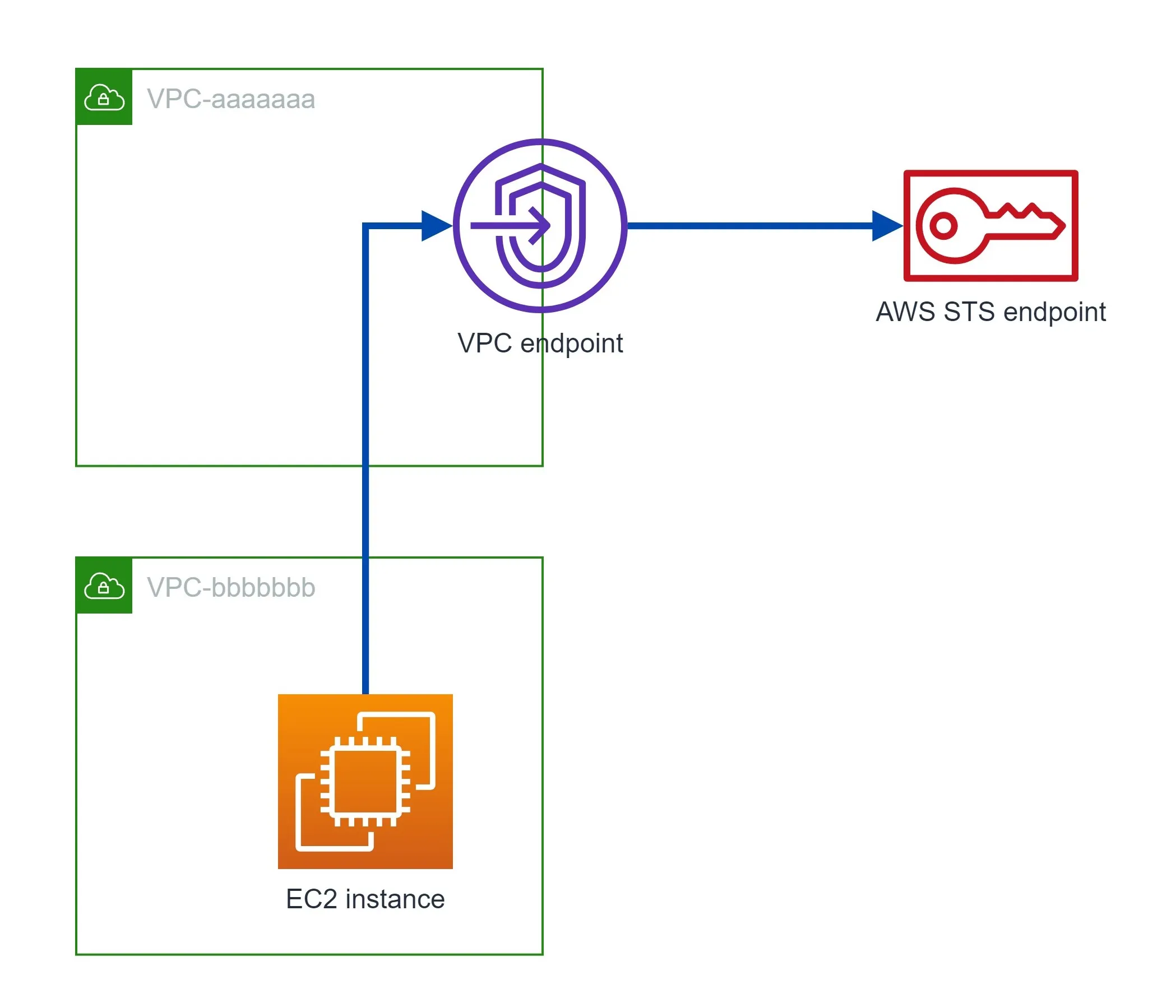
vpc-aaaaaaa and vpc-bbbbbbb) with VPC peering. An STS VPC endpoint in vpc-aaaaaaa, and an EC2 instance in vpc-bbbbbbb.1
2
3
4
5
"Condition": {
"StringEquals": {
"aws:SourceVpc": "vpc-bbbbbbb"
}
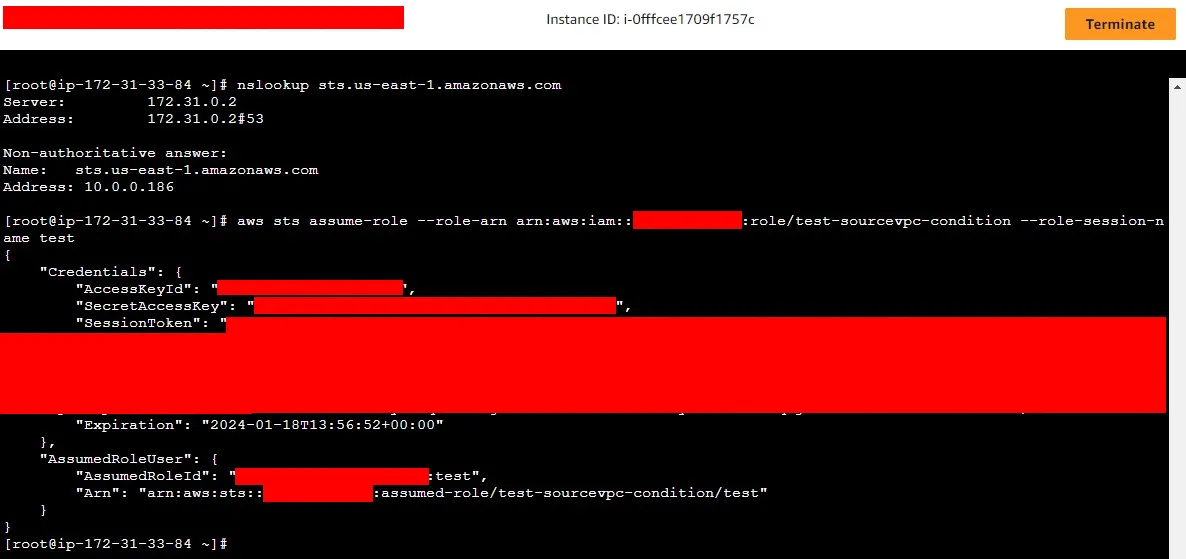
}- I created an EC2 instance in
vpc-05c07e7f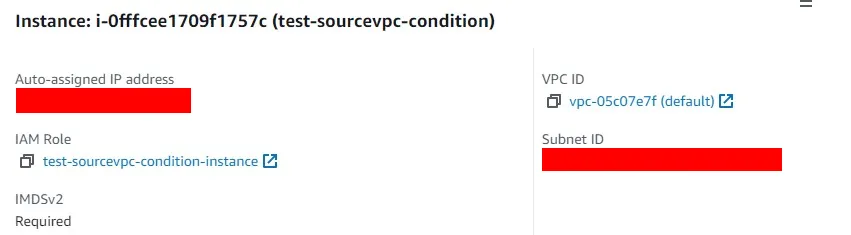
- I created an STS VPC endpoint in another VPC,
vpc-0c3610a65f744e73f, which is peered with the first VPC.
Its private IP address is10.0.0.186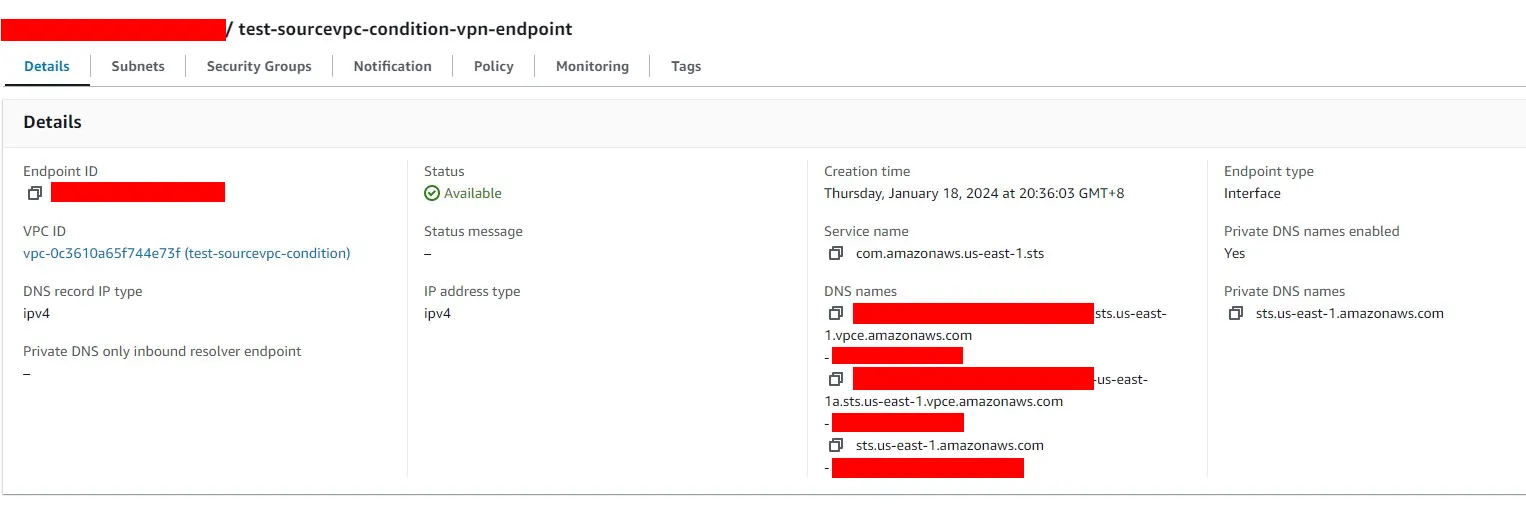
- Then I attached an IAM policy into the EC2 IAM role, using
vpc-05c07e7f, which is the VPC containing the EC2 instance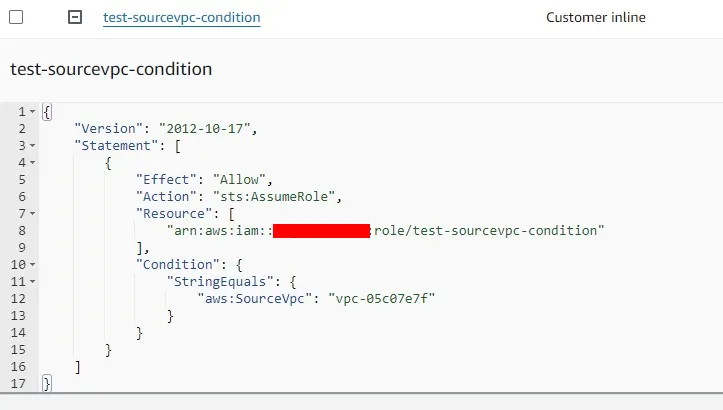
- I logged into the EC2 instance and verified the STS request will go to the VPC endpoint IP address.
Then mysts:assumeRoleCLI command was denied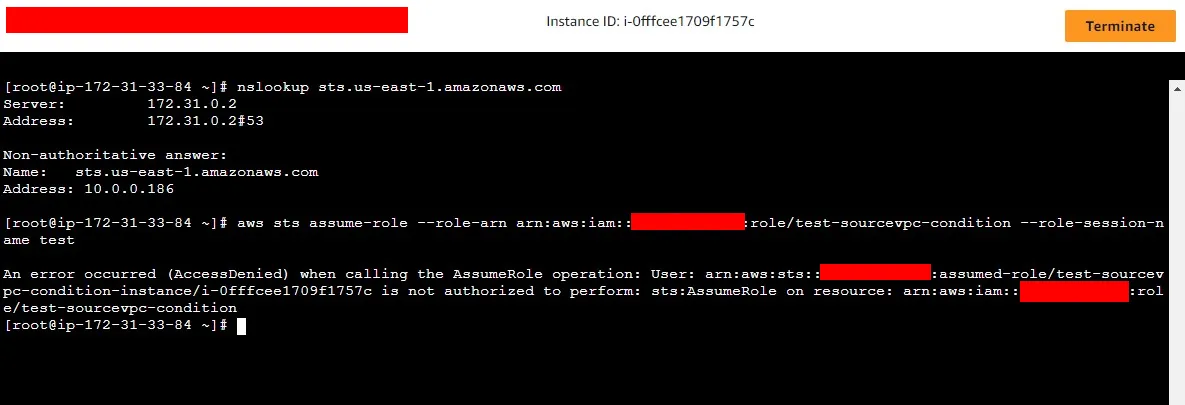
- Then I changed the IAM policy to use
vpc-0c3610a65f744e73f, which contains the VPC endpoint
The CLI command was successful this time.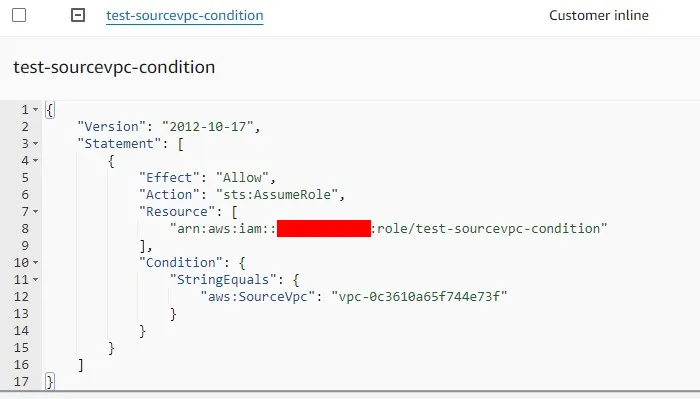
aws:SourceVpc is not where the request is really coming from.- Make the documentation more accurate
Clearly, theaws:SourceVpcdoesn't actually represent whether the request comes from the VPC..... So, the IAM team must change the wording. - Publish the process under the hood
AWS environment is complex, and it's difficult to explain something within a few lines.
If someone really wants to customize the AWS environment, the best way to let them understand is to publish the system details.
I believe if I can learn the request context and IAM condition matching process from a chalk talk session, it's not a secret. So why doesn't AWS publish the whole process in their documentation and let the architect read and decide what their IAM policy and VPC configuration should look like? - Let the appropriate team write the documentation
One of the arguing points I had in the discussion is: "Does thisaws:SourceVpccondition only works on S3?"
The reason for this argument is that when we read the documentation and want to see more details, it directs us to the S3 documentation: Restricting Access to a Specific VPC
Then I asked myself, VPC endpoint is the VPC team's product, and IAM policy is managed by the IAM team, especially when this is a global condition key. So why would the responsibility of explaining it go to the S3 team?
I understand that maybe the S3 team has written an excellent documentation and the IAM team wants to borrow it.
But can the IAM team at least give it a stamp and move it into the IAM documentation? So we, as AWS users, can be less confused about whether some features are specific to one service? Or is it common to all services?
