Amazon Route 53 Profiles - A Deeper look into Centralized DNS Configuration and Governance Solution
Amazon Route 53 Profiles are designed to assist customers in applying and managing a central DNS configuration across numerous VPCs in different accounts within the same AWS Region. It expedite the deployment of DNS changes for multiple VPCs using a single configuration alteration on Amazon Route 53 Profiles. The services that can be centralized using Amazon Route 53 Profiles include Private Hosted Zones, Resolver Rules, DNS Firewall failure mode configuration, rule Groups, and DNSSEC.
But you cannot manage existing HostedZones created by those accounts using the Amazon Route 53 Profile. It is a solution to have a centrally managed DNS account where all of the Amazon Route 53 changes can be made and shared. So one networking account creates all of the hosted zones and DNS firewall rules etc, and shares these rules with the org and Org accounts can then, associate VPCs that will use this policy only.
- Permissions for owners
Profile owners can create, manage, and delete resources and manage VPC associations. The owner can view the VPC associations and resource associations made by the consumer.
- Permissions for consumers
The default permission for consumers of a shared Profile is read-only. With read-only permission, they can see the associated resources and associate it to VPCs, but can't manage the resource associations.
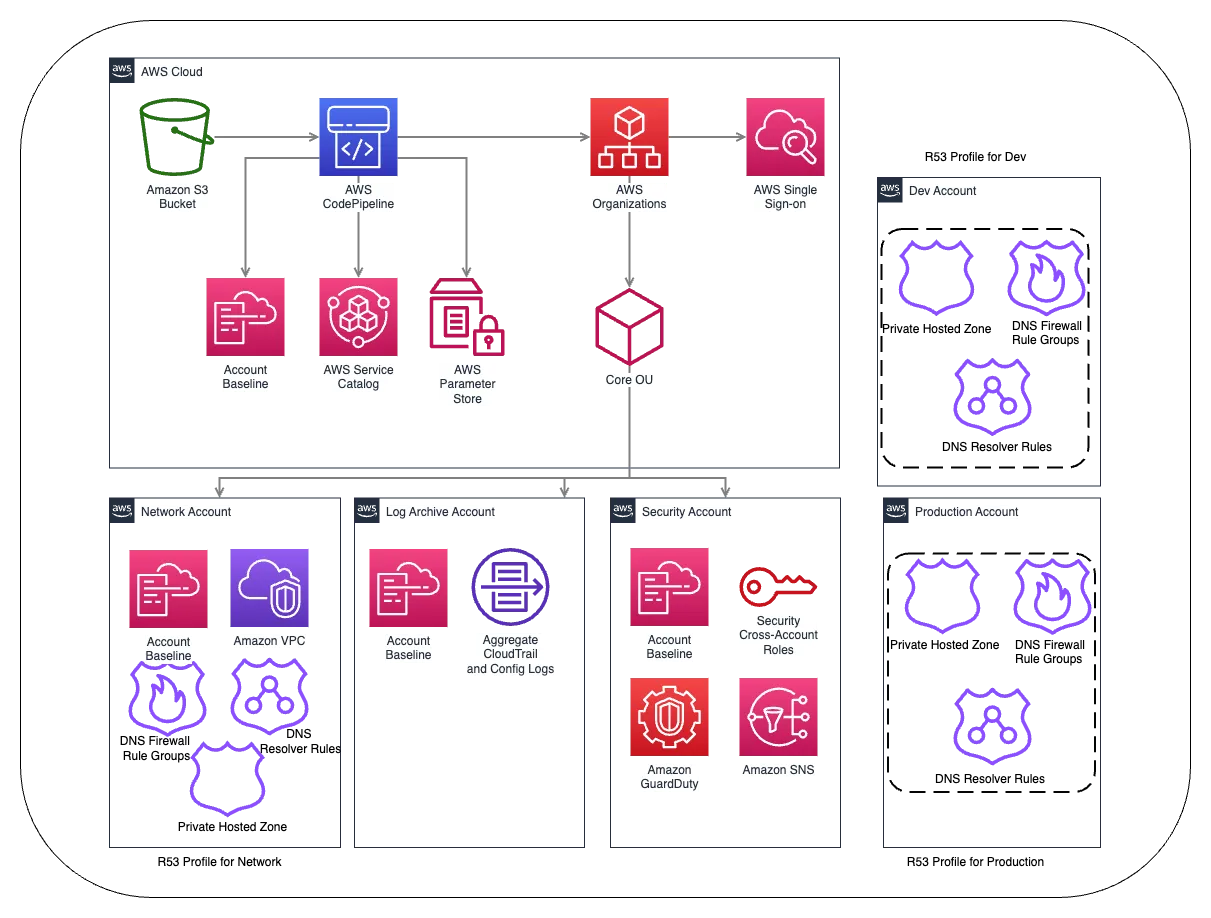
structure would impact production, along with the added cost of using the new feature. These are all cases that would and should involve your team and Dev testing for suitability.
- Open Amazon Route53 console.
- In the navigation pane, choose Profiles.
- On the navigation bar, choose the Region where you want to create the Profile.
- Enter a name for the Profile, optionally add tags, and choose Create Profile.
- This creates an empty Profile with default configurations to which you can associate resources. After you associate resources to the Profile, you can associate it to some VPCs and edit how some of the Resolver configurations apply to the VPCs.
Total Profile-VPC associations = 200
[$0.75 (per hour) (for first 100 VPCs) + Total of VPC associations beyond 100 * $0.0014] x [24 hours x 30 days] = [$0.75 + 100 x $0.0014] x 720 = $640.8