Essential Steps for Securing Your AWS Environment
Master Your AWS Security with These Top 10 Cloud-Protecting Practices.
Tip 1: Implement a Multi-Account Architecture
Tip 2: Design a Custom VPC Configuration
Tip 3: Prioritize Patch Management
Tip 4: Optimize Authentication with Single Sign-On
Tip 5: Secure the Root Account
Tip 6: Manage Permissions Effectively
Tip 7: Enhance Remote Access Security
Tip 9: Protect Web Applications with WAF
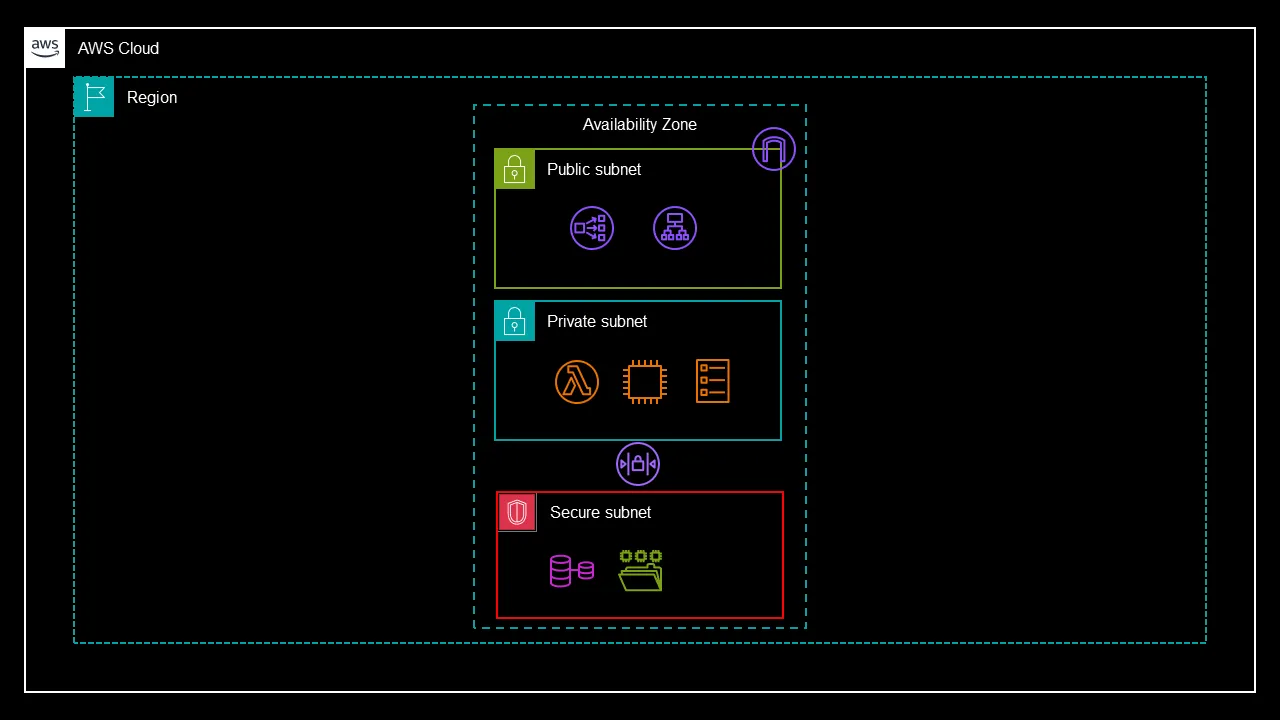
- In the first layer, have a public subnet. Just put your load balances there for anything that needs to be exposed to the Internet. Or maybe you’ve got a reverse proxy or a VPN server.
- The second layer to your VPC is going to be a private subnet. I’d put all my compute workloads here like Lambda Functions, EC2 instances and Fargate tasks as well. That way, you’ve separated your compute workload from the Internet, make sure you’ve got a NAT Gateway, so those resources can get out to the Internet for their updates. But ultimately, the only way into these workloads should be via the load balancer.
- And then, lastly, the third tier. This is the secure tier. Or, as I like to call it, the data’s tier. I put all my Managed AWS services here that look after my data. RDS, EFS, FSX, etc. And it keeps that data secure. Why is it secure? Well, first of all, there’s no Internet gateway or NAT Gateway. There’s also a network access control list (NACL) across the bottom of this as well, which then means you’re blocking that from the public subnet.