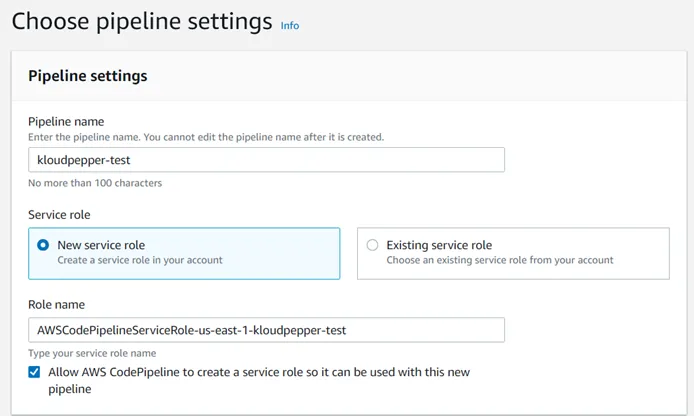
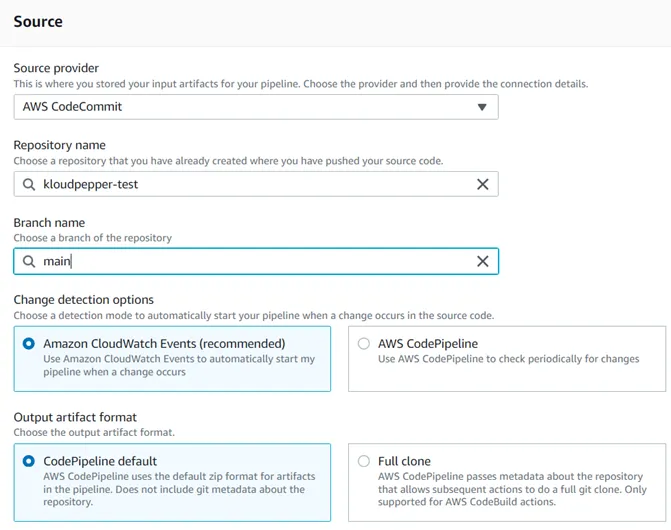
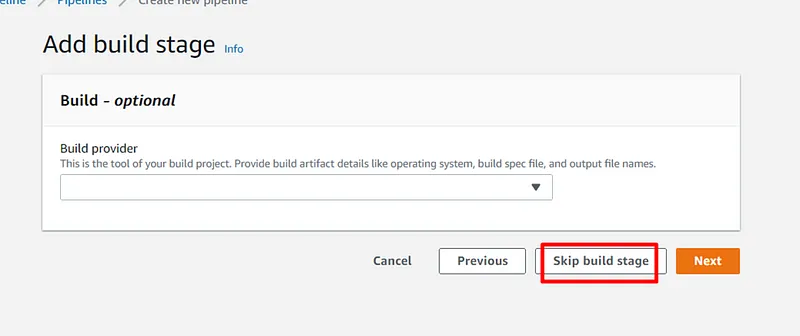
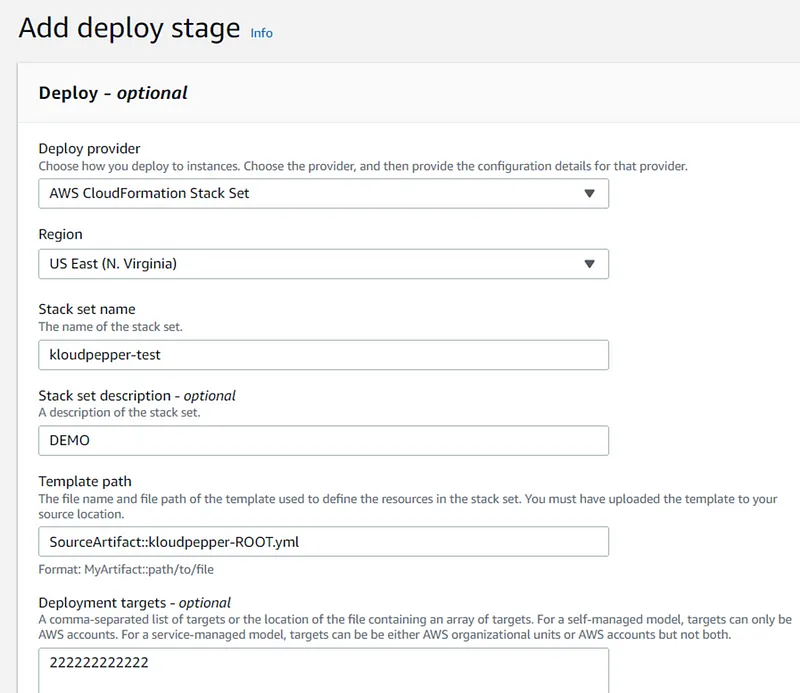
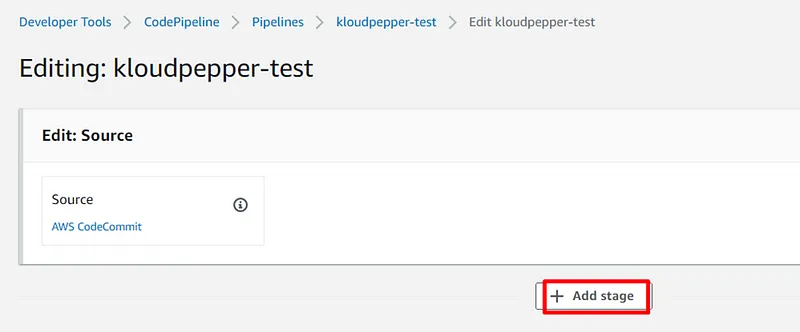
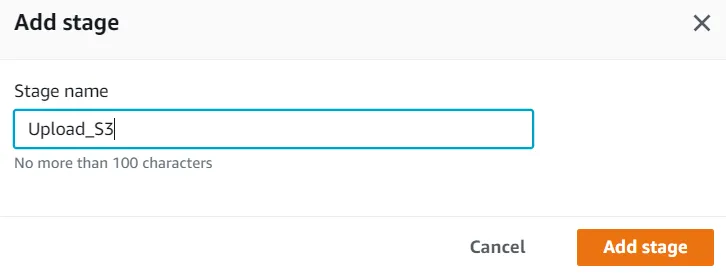
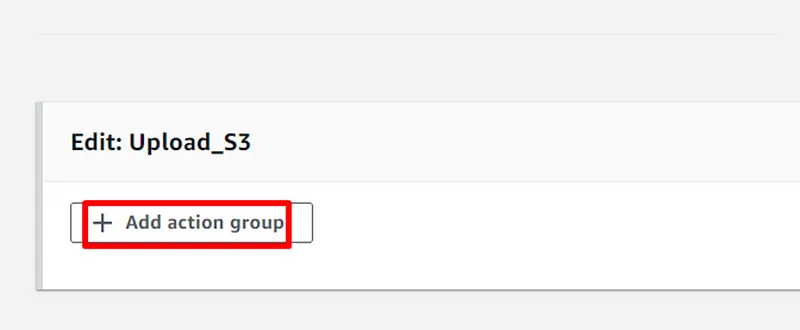
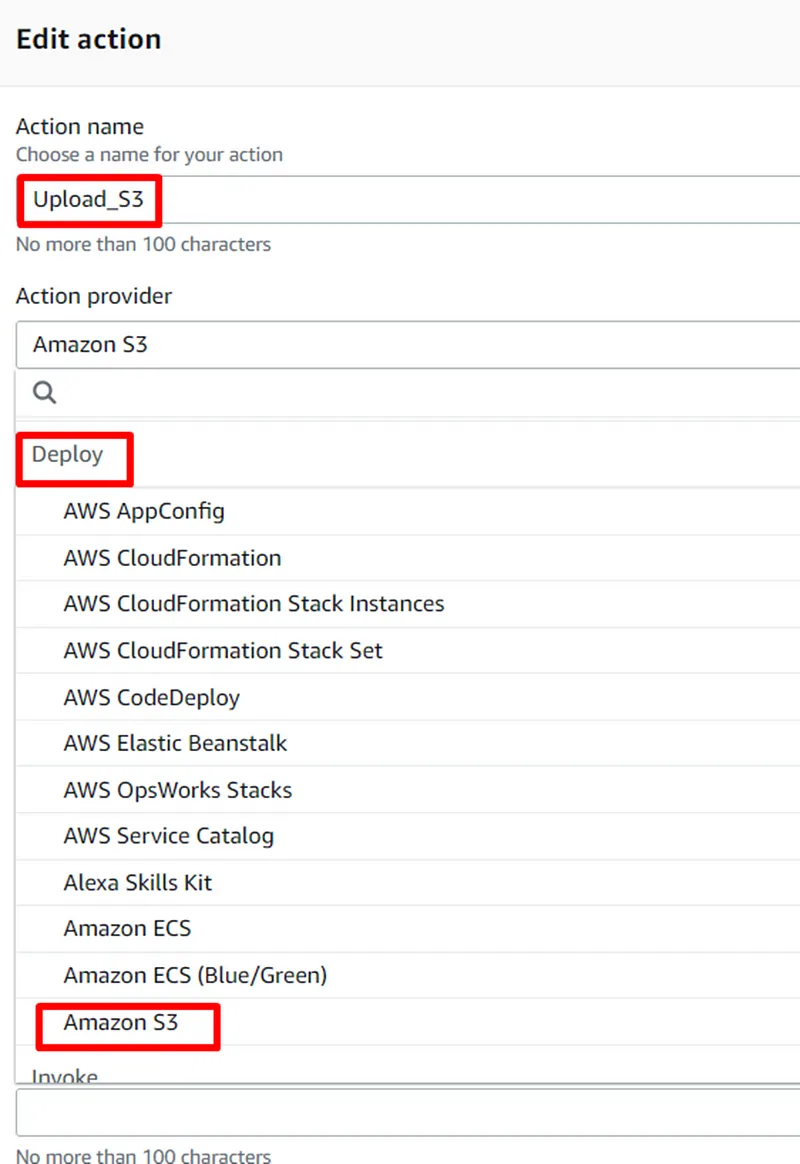
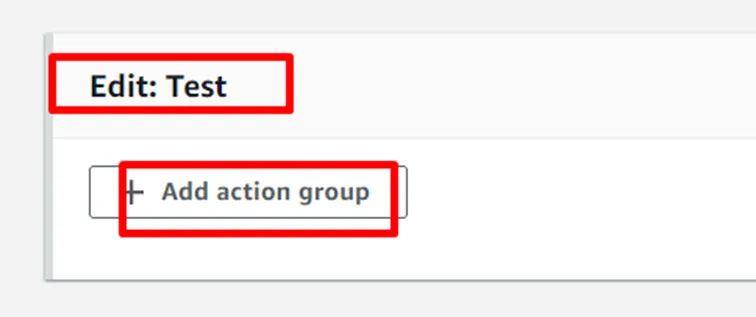
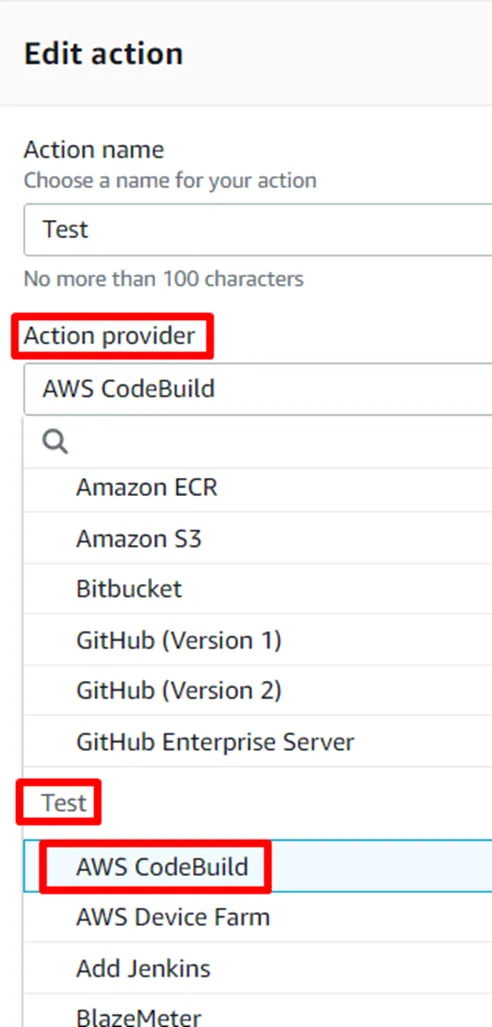
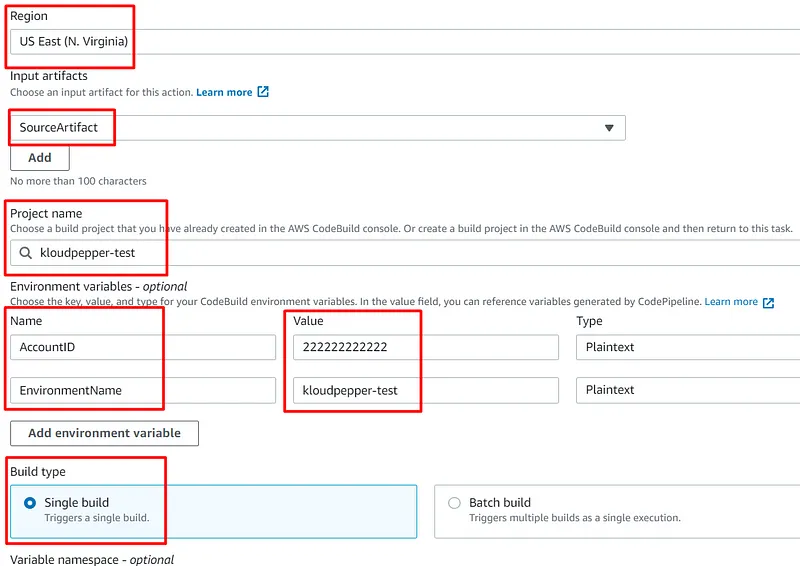
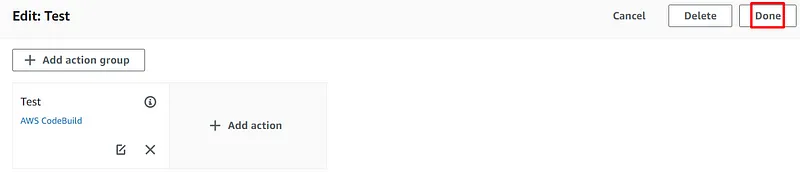
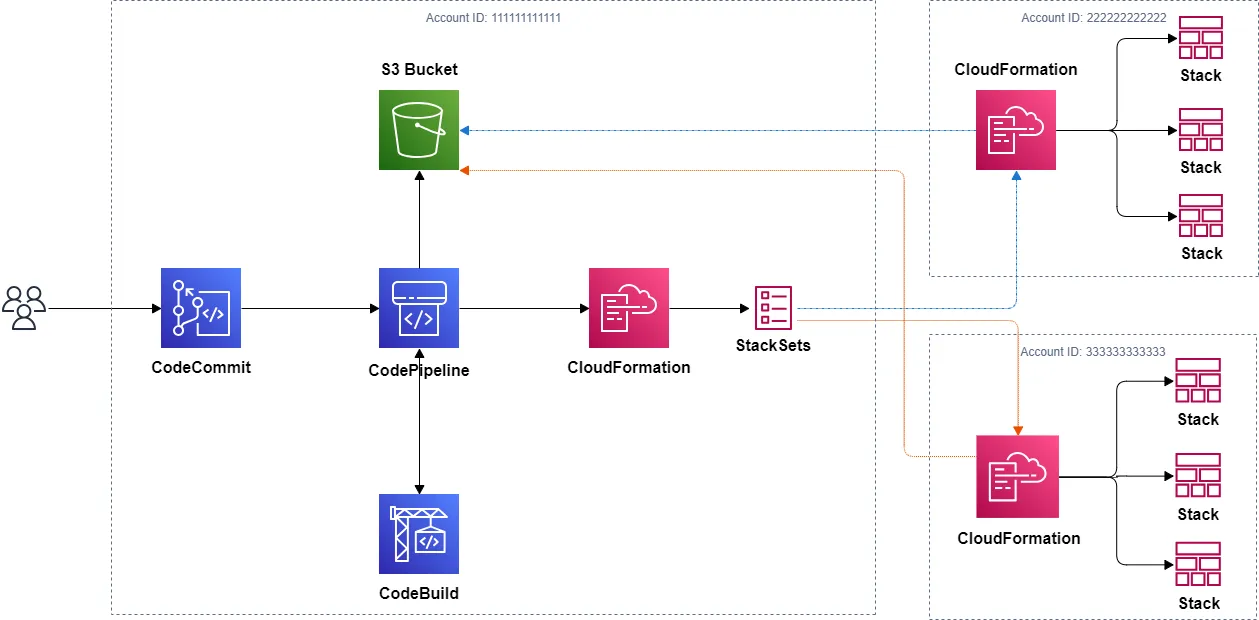
Build a CI/CD pipeline for CloudFormation and Cross-Account.
Step-by-step guide on creating a CI/CD for AWS CloudFormation StackSets with CodeCommit, CodeBuild, CodePipeline and S3 to Multi-Account deployments.
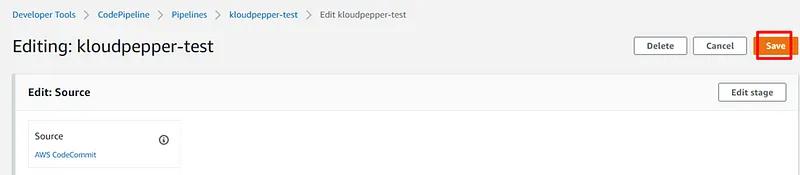
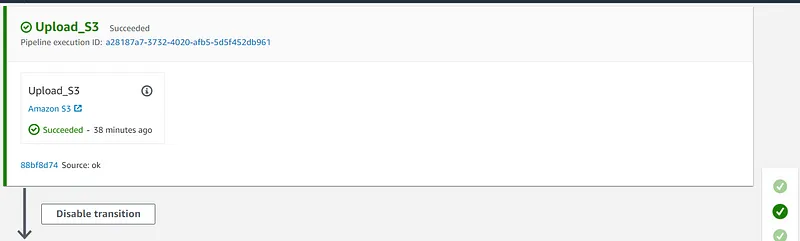
- AWS CloudFormation templates should be stored in a Git repository on CodeCommit to perform workflows that include code revisions and modifications, pull requests, and merge branches.
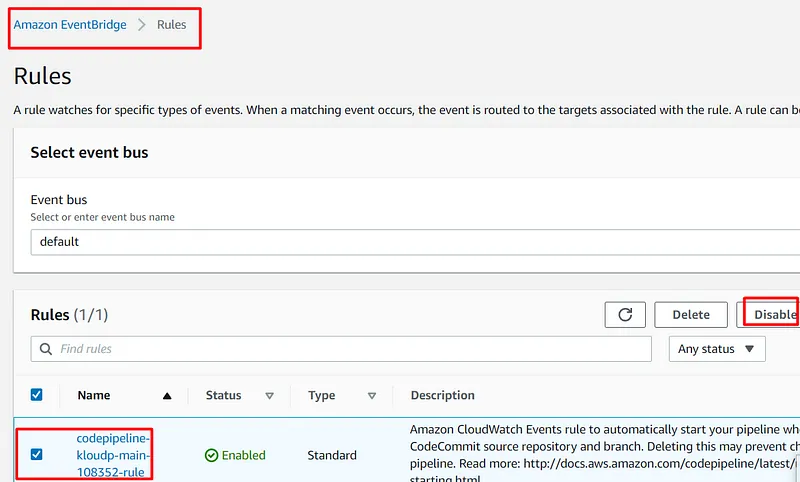
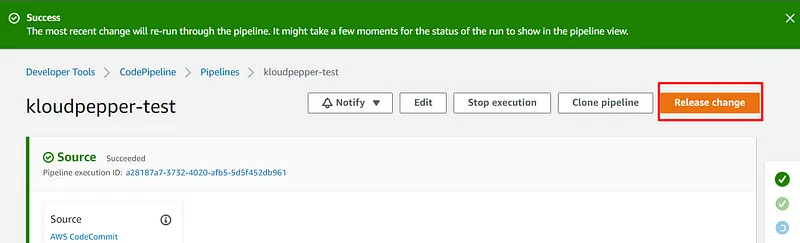
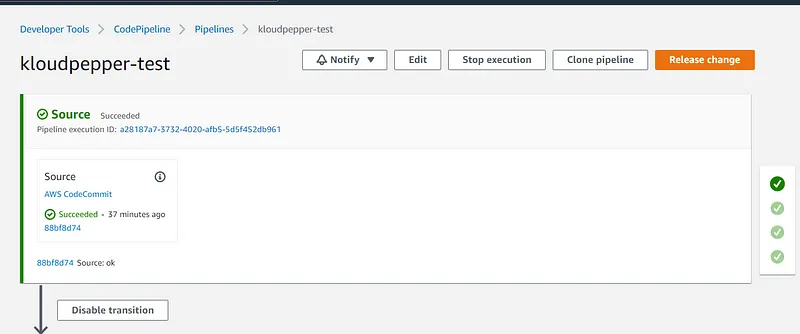
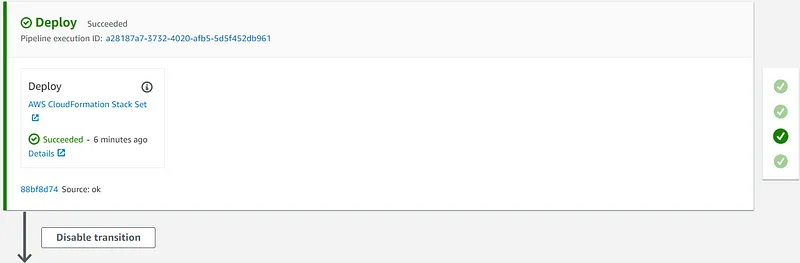
- The CodePipeline service should be used for the CI/CD pipeline and to automate the environment deployment process.
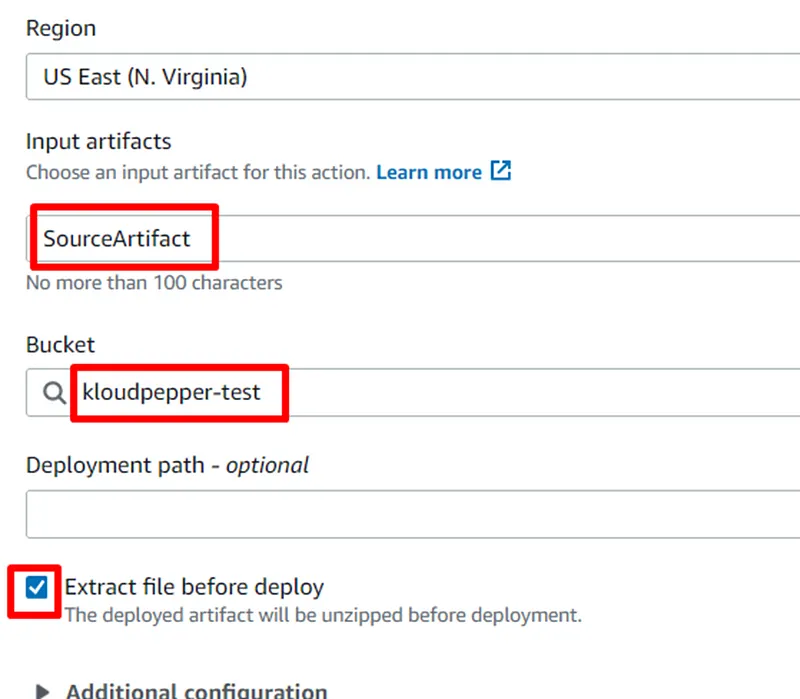
- The templates will be uploaded to a bucket in S3 so the CloudFormation stacks in the destination accounts can access them.
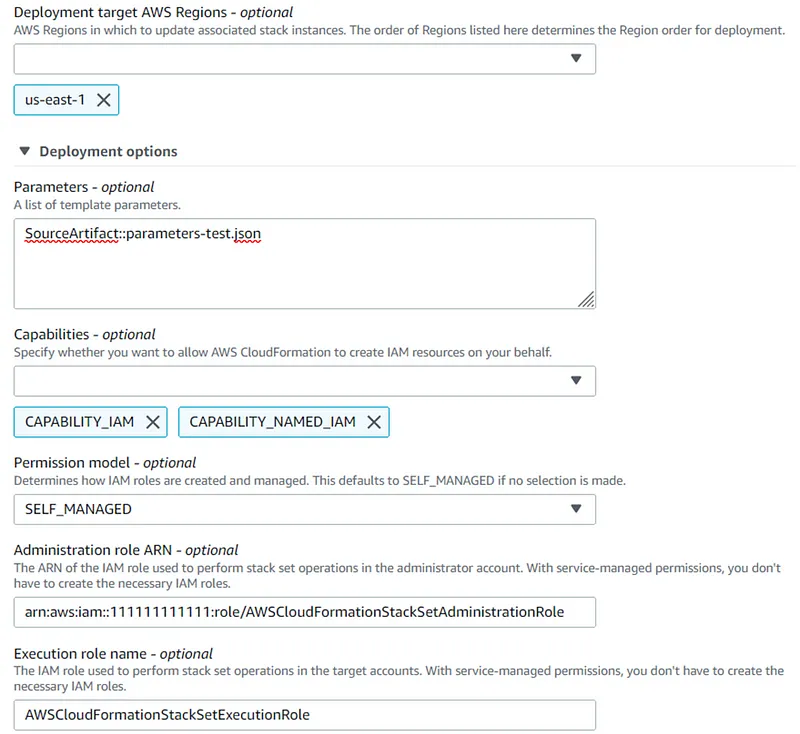
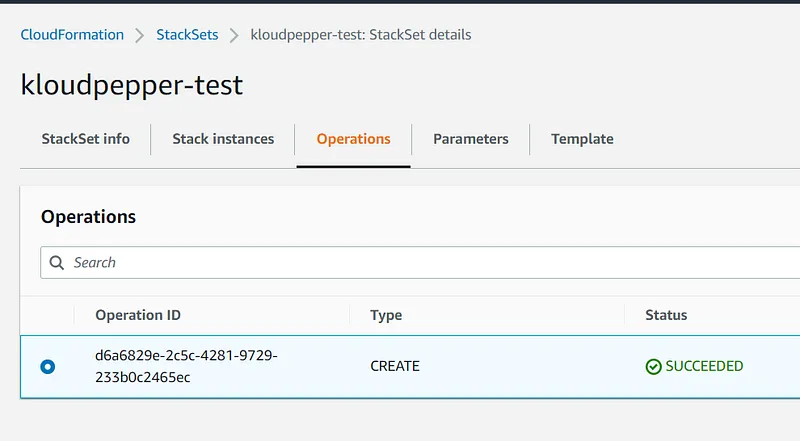
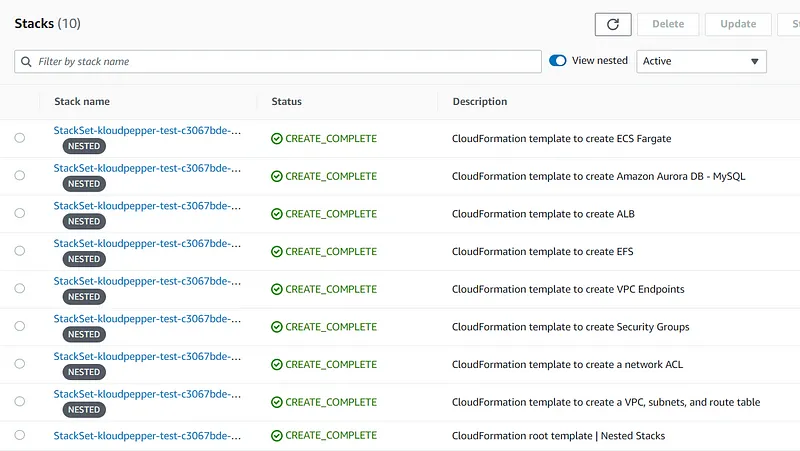
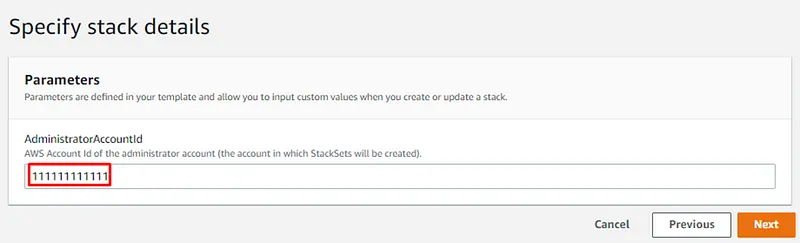
- AWS CloudFormation (Stack Set) service will be used in the central account ID:111111111111 to provision and manage the resources in the target accounts: dev-ID:222222222222, prod-ID:333333333333
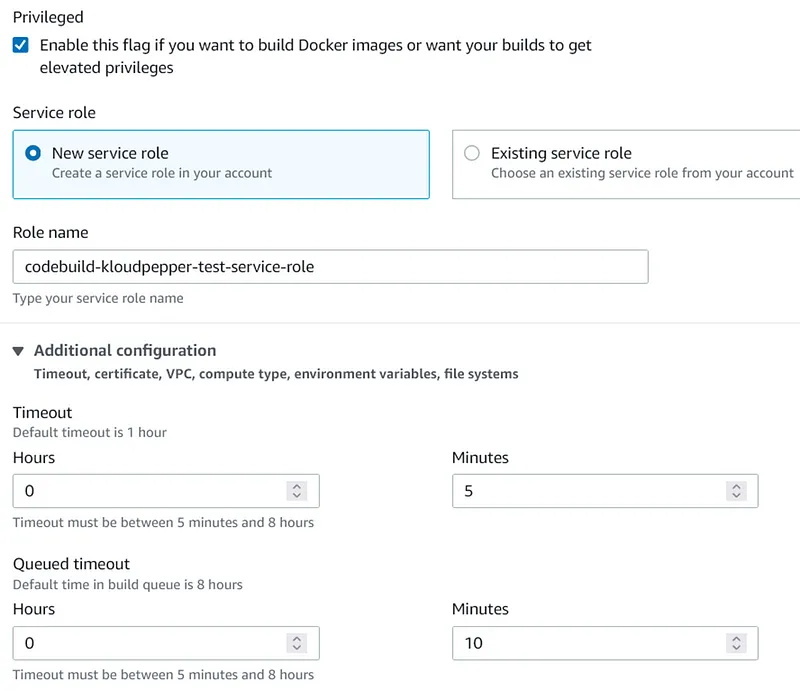
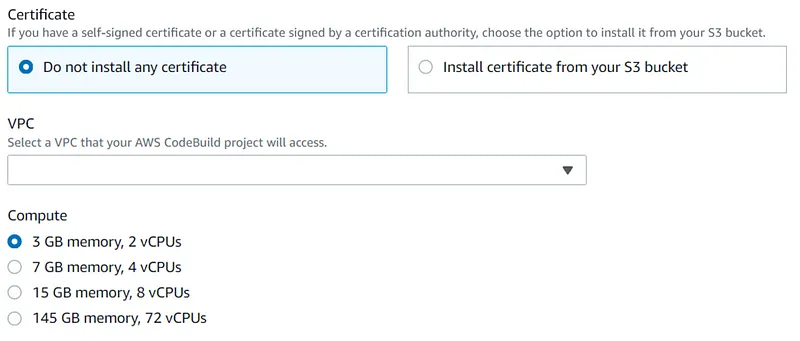
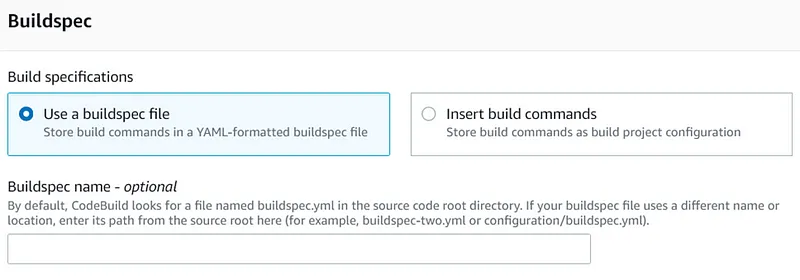
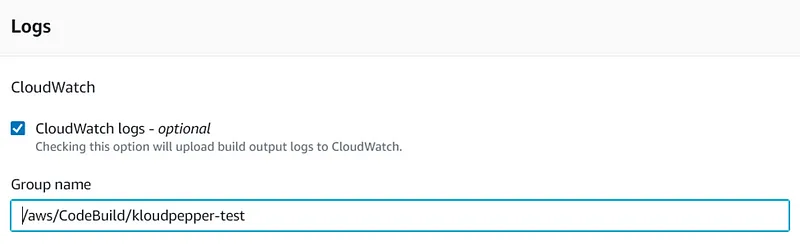
- CodeBuild service must be used to perform a test and thus be able to check the availability of the deployed environment.
111111111111 and 222222222222 with the correct IDs that you have in your accounts. Also, you must modify the Resource value to the correct ARN (Bucket's ARN):1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
{
"Version": "2012-10-17",
"Id": "Policy1644732224428",
"Statement": [
{
"Sid": "Stmt1644732214596",
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws:iam::111111111111:root",
"arn:aws:iam::222222222222:root"
]
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::kloudpepper-test/*"
}
]
}
https://github.com/kloudpepper/IaC/blob/main/CloudFormation/extras/AWSCloudFormationStackSetExecutionRole.yml
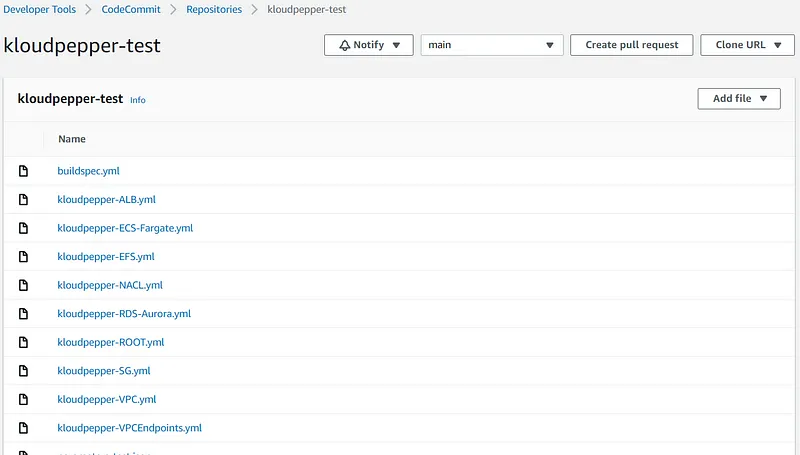
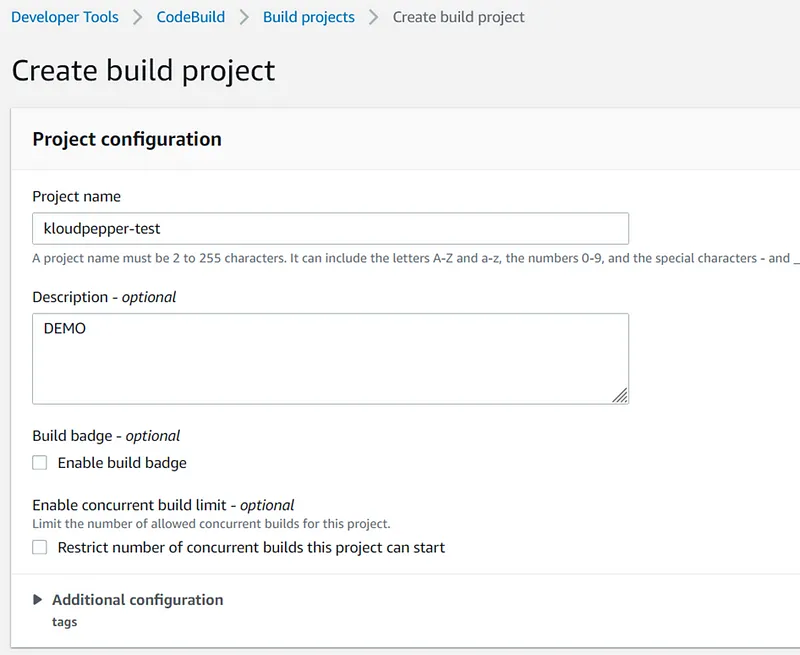
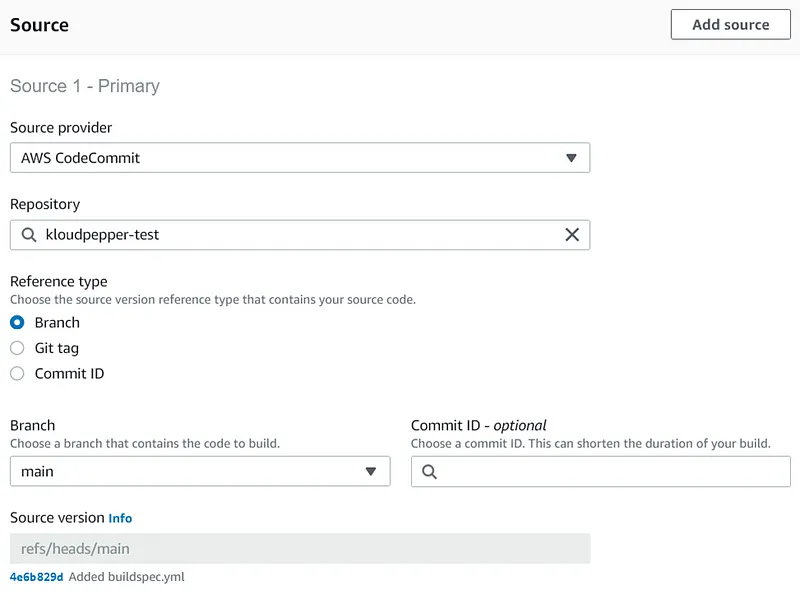
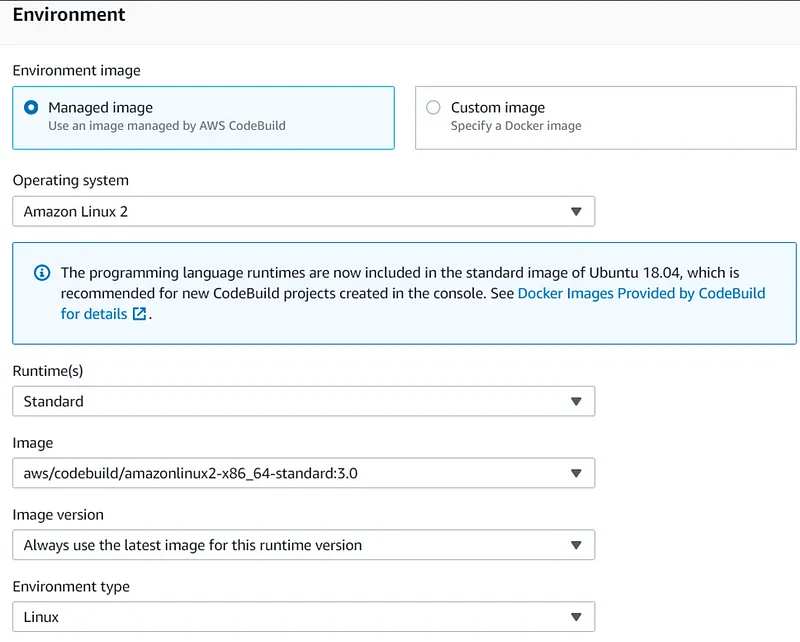
222222222222 ID with the valid destination account ID:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": [
"arn:aws:iam::222222222222:role/AWSCloudFormationStackSetExecutionRole"
],
"Action": [
"sts:AssumeRole"
]
}
]
}