Compliant infrastructure using infrastructure as code
How do you make sure that your infrastructure is compliant? And how do you make sure that the infrastructure stays compliant during the promotion across all environments? The only answer is infrastructure as code!
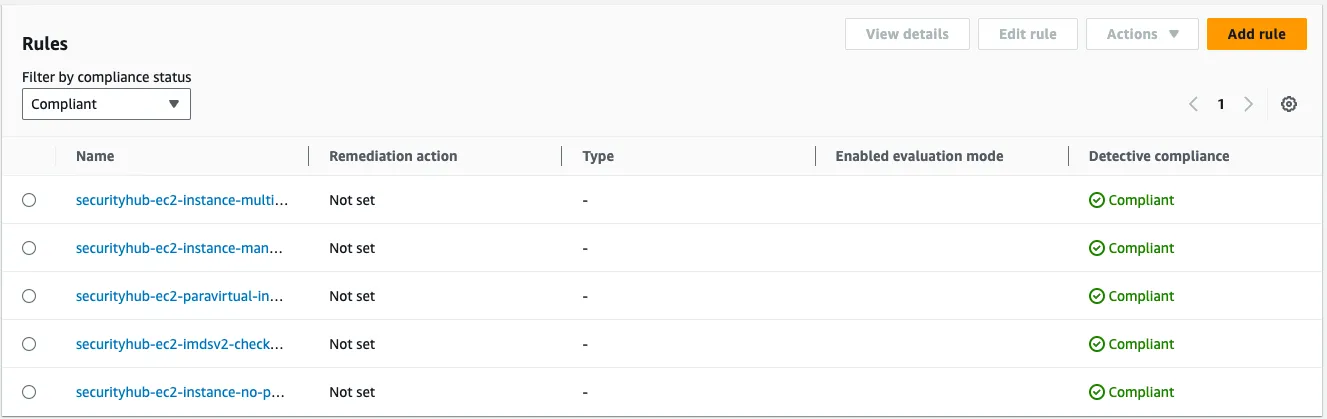
- ec2-instance-multiple-eni-check, this control checks if Amazon EC2 instance uses multiple ENI/EFA. This control will pass if single network adapters is used.
- ec2-paravirtual-instance-check, this control checks if the EC2 virtualization type is paravirtual. The control fails for an EC2 instance if
virtualizationTypeis set toparavirtual. - ec2-instance-no-public-ip, this control checks whether EC2 instances have a public IP address. The control fails if the publicIp field is present in the instance configuration. This control applies to IPv4 addresses only.
- ec2-imdsv2-check, this control checks if your EC2 instances have IMDSv2 configured. The control passes if HttpTokens is set to required for IMDSv2. The control fails if HttpTokens is set to optional.
- ec2-instance-managed-by-ssm, this control checks if the EC2 instances are managed by SSM
- AmazonSSMManagedInstanceCore, enables the instance to be managed by SSM.
- AmazonInspector2ManagedCispolicy, enables the ability to perform the CIS baseline scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Role:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action: sts:AssumeRole
Principal:
Service: ec2.amazonaws.com
ManagedPolicyArns:
- arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore
- arn:aws:iam::aws:policy/AmazonInspector2ManagedCispolicy
InstanceProfile:
Type: AWS::IAM::InstanceProfile
Properties:
Roles:
- !Ref Roleyum update -y --security option in the user-data.1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Security group for the test instance
VpcId: "{{resolve:ssm:/landingzone/vpc/vpc-id}}"
SecurityGroupEgress:
- Description: Allow outbound connectivity to port 443.
IpProtocol: tcp
FromPort: 443
ToPort: 443
CidrIp: 0.0.0.0/0
LaunchTemplate:
Type: AWS::EC2::LaunchTemplate
Properties:
LaunchTemplateData:
IamInstanceProfile:
Arn: !GetAtt InstanceProfile.Arn
ImageId: "{{resolve:ssm:/aws/service/ami-amazon-linux-latest/amzn2-ami-hvm-x86_64-gp2}}"
InstanceType: t3.micro
SecurityGroupIds:
- !Ref InstanceSecurityGroup
MetadataOptions:
HttpTokens: required
UserData:
Fn::Base64: !Sub |-
#!/bin/bash -x
yum update -y --security
Instance:
Type: AWS::EC2::Instance
Properties:
LaunchTemplate:
LaunchTemplateId: !GetAtt LaunchTemplate.LaunchTemplateId
Version: !GetAtt LaunchTemplate.LatestVersionNumber
SubnetId: "{{resolve:ssm:/landingzone/vpc/private-subnet-1-id}}"
1
2
3
sh-4.2$ uname -r
4.14.336-253.554.amzn2.x86_64
sh-4.2$1
2
3
4
5
sh-4.2$ amazon-linux-extras | grep kernel
49 kernel-5.4 available [ =stable ]
55 kernel-5.10 available [ =stable ]
62 kernel-5.15 available [ =stable ]
sh-4.2$1
sh-4.2$ sudo amazon-linux-extras install kernel-5.151
sudo reboot- Create your own up to date base AMI.
- Use the Amazon Linux 2023 AMI with a newer kernel version.
