
AWS open source newsletter, #195
A round up of the latest open source news, projects, and events that every open source developer should know about.
amazon-sqs-python-extended-client-lib
Demos, Samples, Solutions and Workshops
domain-specific-genai-chatbot-with-serverless
generate-s3-accelerate-presigned-url
amazon-eks-running-webassembly
The best from around the Community
Harnessing Karpenter: Transforming Kubernetes Clusters with Argo Workflows
Optimize Amazon EKS Costs with Karpenter and Stormforge
Everything Open April 16th-18th, Gladstone Australia
AWS Summit London April 24th, EXCEL London
OpenSearchCon Europe May 6th-7th, Berlin Germany
Cortex Every other Thursday, next one 16th February
OpenSearch Every other Tuesday, 3pm GMT
safeaws checks your AWS CLI commands before they are run, for more details including a short demo video of this in action.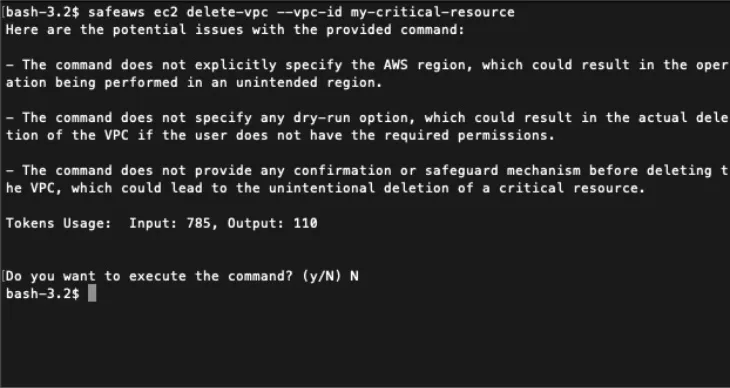
Instead of calling it type-safe, I decided to go with type-friendly, because the library is still in an early stage, and is not 100% type-safe. Under the hood, Tsynamo compiles the built queries into AWS SDK v3 commands. I feel that Tsynamo simplifies the AWS SDK API quite a lot since the developer doesn't have to mess around with condition/filter expressions or attribute names/values themselves, and as a bonus gets autocompletion for building the queries!
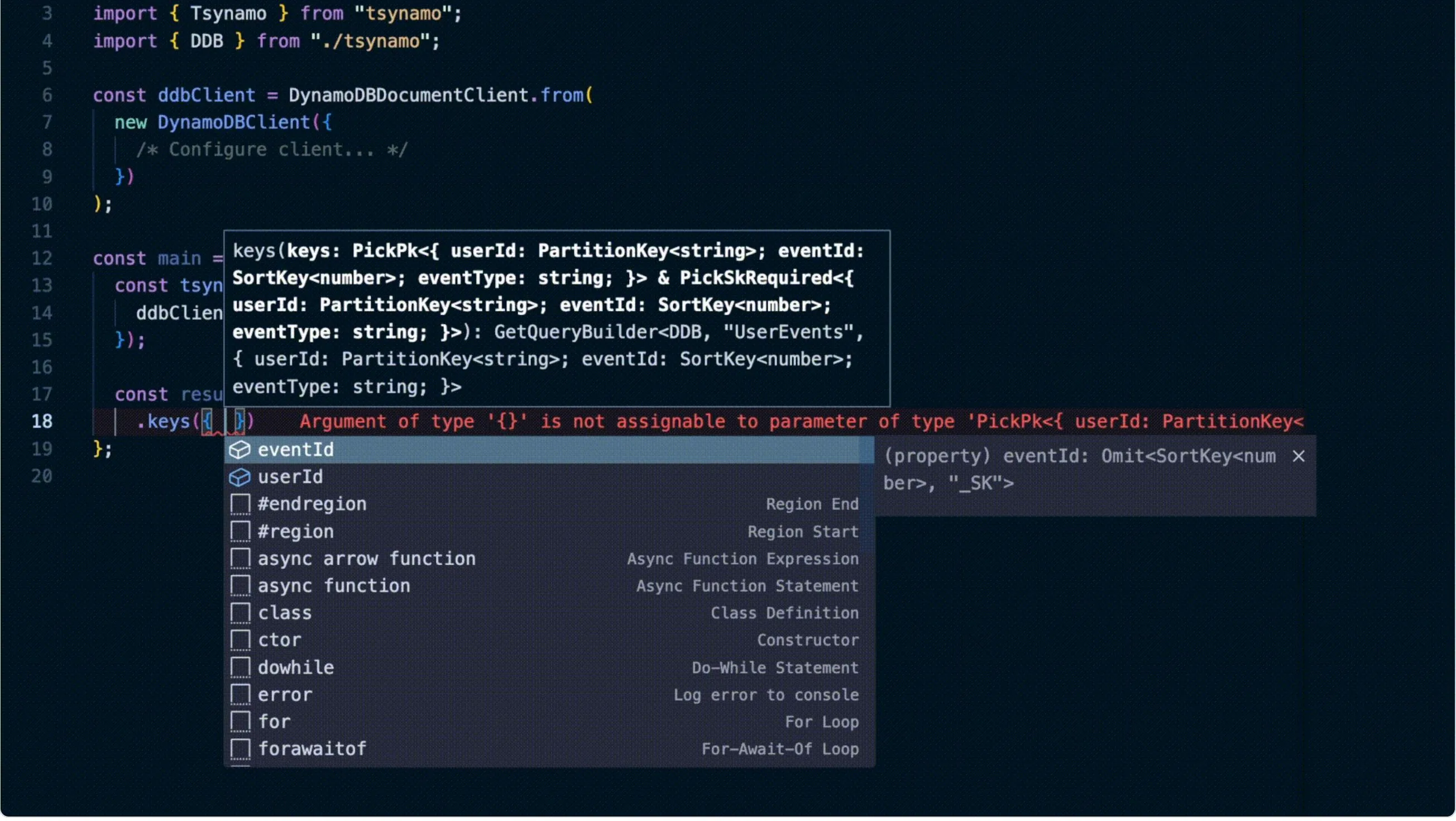
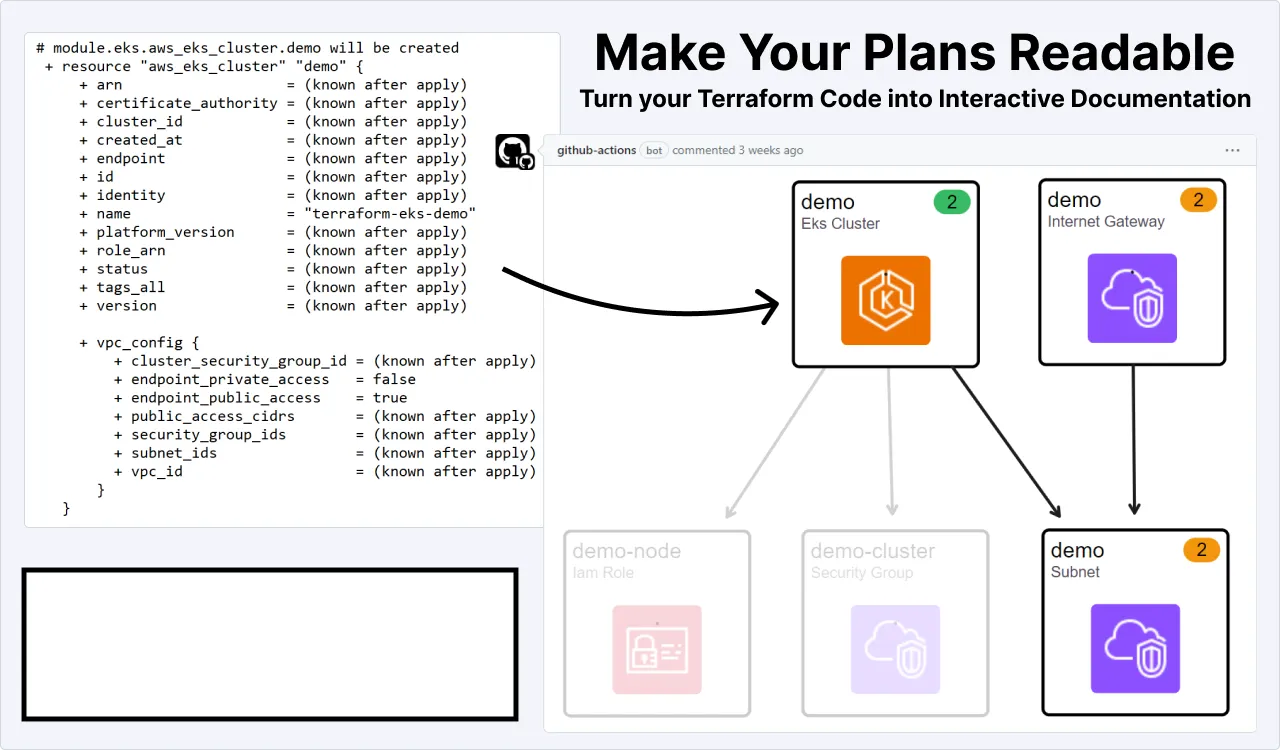
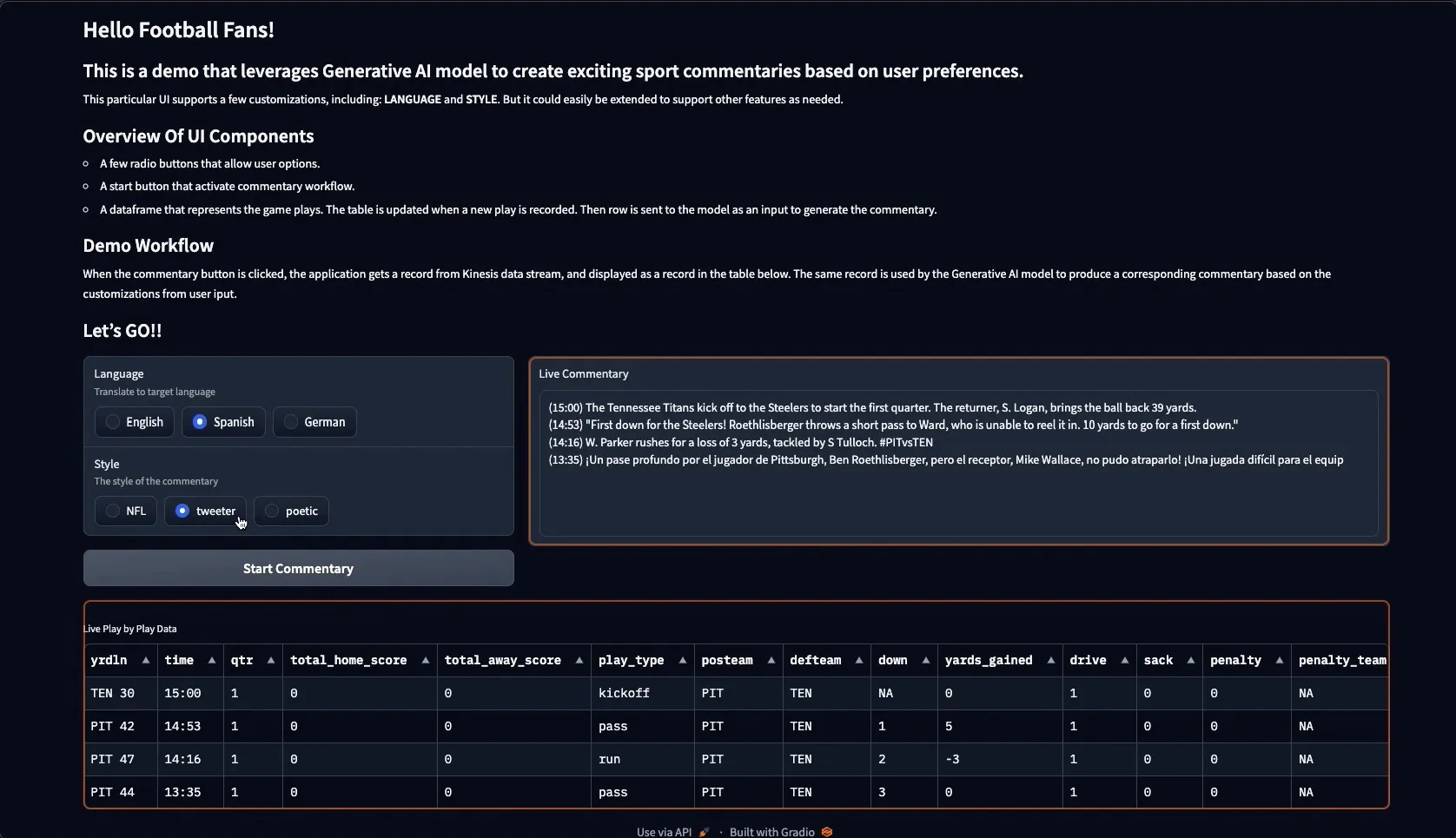
- Amazon EKS-Optimized Amazon Linux 2023 AMIs Now Availablewalks you through the new Amazon Linux 2023 AMIs that you can now use with your kubernetes clusters, including things you should be aware of
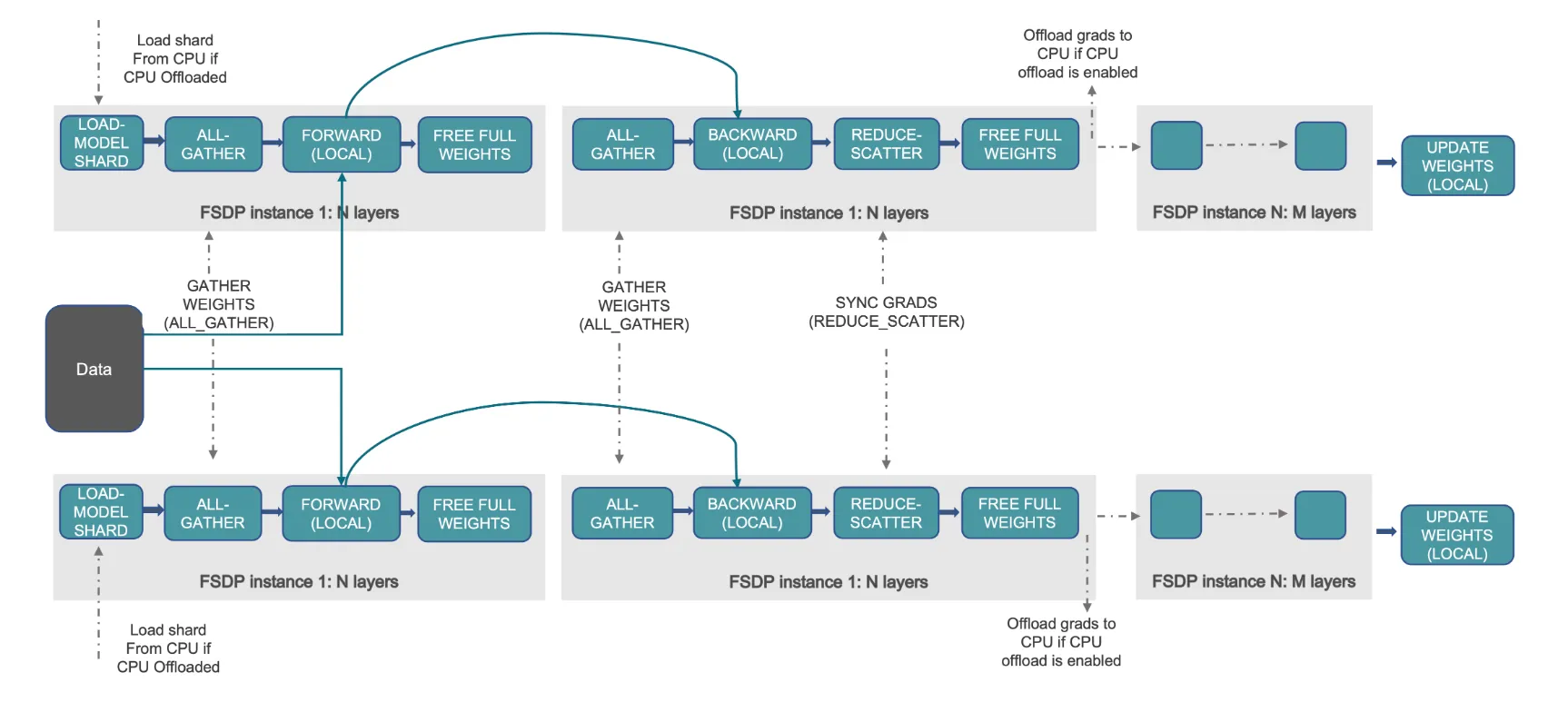
- Scale LLMs with PyTorch 2.0 FSDP on Amazon EKS – Part 2provides a detailed walk through of the PyTorch Fully Sharded Data Parallel (FSDP) library, showing you how it can help you train larger models more efficiently [hands on]
- Adding Storage using OpenEBS on EKS Anywhere shows you how OpenEBS can leverage the existing storage on nodes in an EKS Anywhere cluster to provide persistence support for the workloads [hands on]
- How Snap Inc. secures its services with Amazon EKS explores Snap’s cloud infrastructure, showing how it has evolved from running a monolith inside Google App Engine, to micro-services deployed in Kubernetes across AWS and GCP
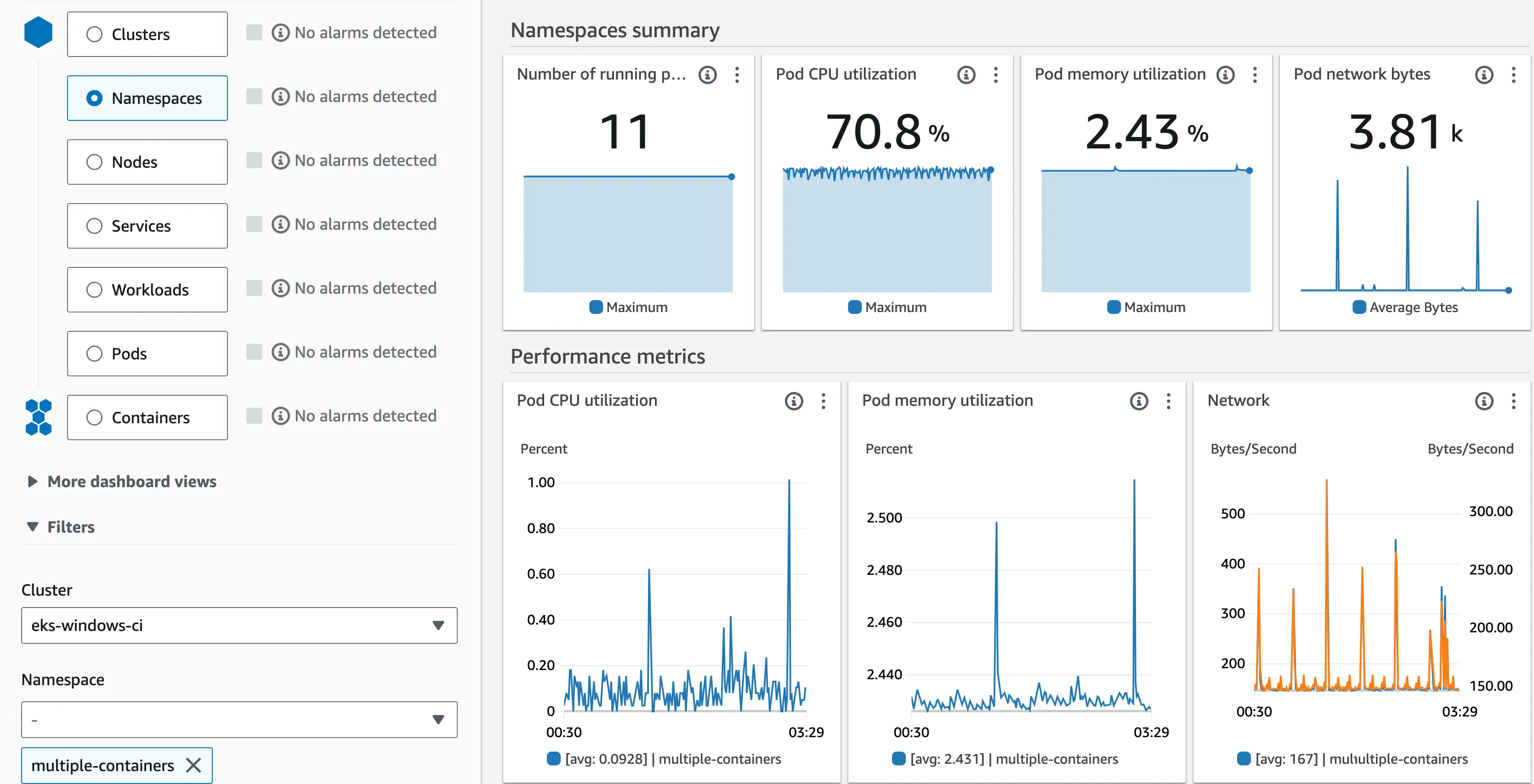
- Announcing Amazon CloudWatch Container Insights for Amazon EKS Windows Workloads Monitoring walks you through the process of enabling Container Insights for your Amazon EKS Windows cluster [hands on]
- Replicate data between partitioned and non-partitioned tables using trigger functions in Amazon RDS for PostgreSQL or Amazon Aurora PostgreSQL shows you how to replicate data between partitioned and non-partitioned tables using trigger functions [hands on]
- Achieve faster switchover for Amazon RDS Blue/Green Deployments with large number of connections looks at some of the improvements you can see which will reduce overall down time during your Blue/Green MySQL deployments [hands on]
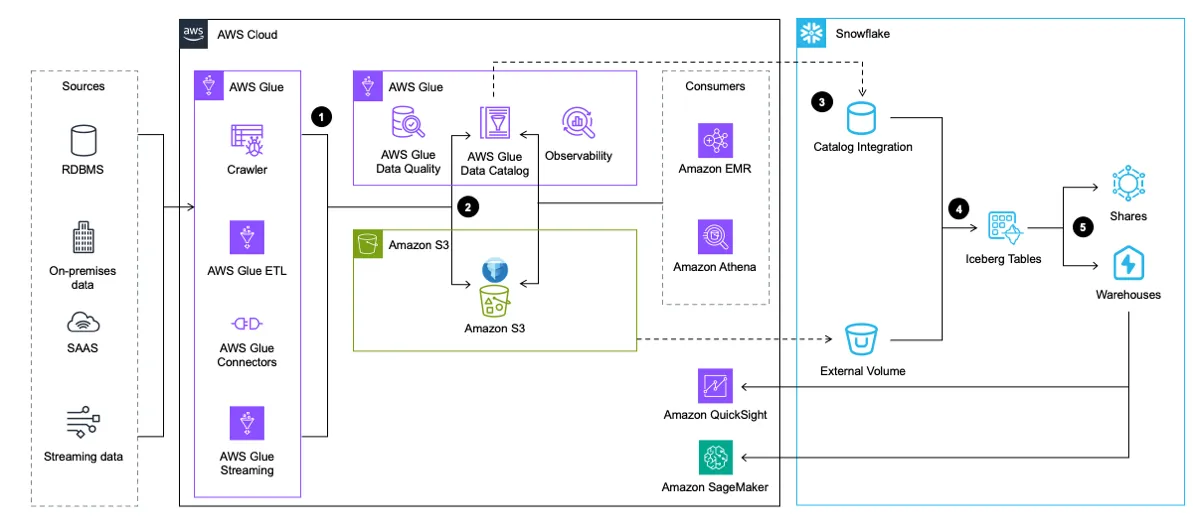
- Use Apache Iceberg in your data lake with Amazon S3, AWS Glue, and Snowflake explores a couple of architecture patterns for implementing Apache Iceberg in a data lake for better interoperability across AWS and Snowflake
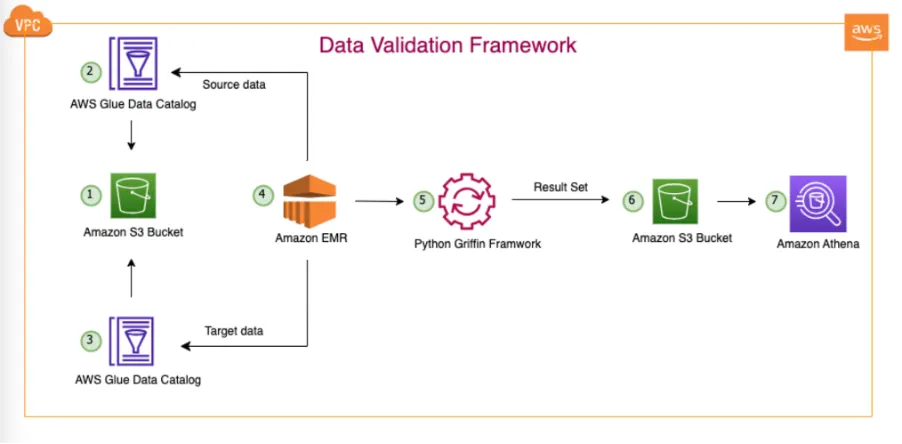
- Automate large-scale data validation using Amazon EMR and Apache Griffin is a step-by-step process to validate large datasets using Amazon EMR and Apache Griffin, and open source library for data quality that supports both batch and streaming mode [hands on]
Any opinions in this post are those of the individual author and may not reflect the opinions of AWS.
