Better Threat Detection with CloudWatch and Generative AI
Enhance AWS threat detection with CloudWatch Logs and Generative AI. Explore a Streamlit app that retrieves logs, sends data to an LLM, and displays recommendations.
streamlit for creating the user interface, boto3 for interacting with AWS services, json for handling JSON data, and botocore.exceptions for catching AWS-related exceptions. The title "CloudWatch Log Analyzer" is set for the Streamlit application, and a session client for CloudWatch Logs is created.us-east-1 if available, or the first available region if us-east-1 is not accessible. A dropdown menu is created for selecting the region, with the default region preselected if available.prompt_data. A client for the Bedrock Runtime service is created to interact with the LLM.summarize_article function takes the prompt_data as input and constructs a prompt configuration object with instructions for the LLM. The log data is included in the prompt, and the LLM is tasked with analyzing the data and providing recommendations for AWS WAF rules. The invoke_model method is used to send the prompt configuration to the Bedrock Runtime API. The LLM's response is received and parsed to extract the summary.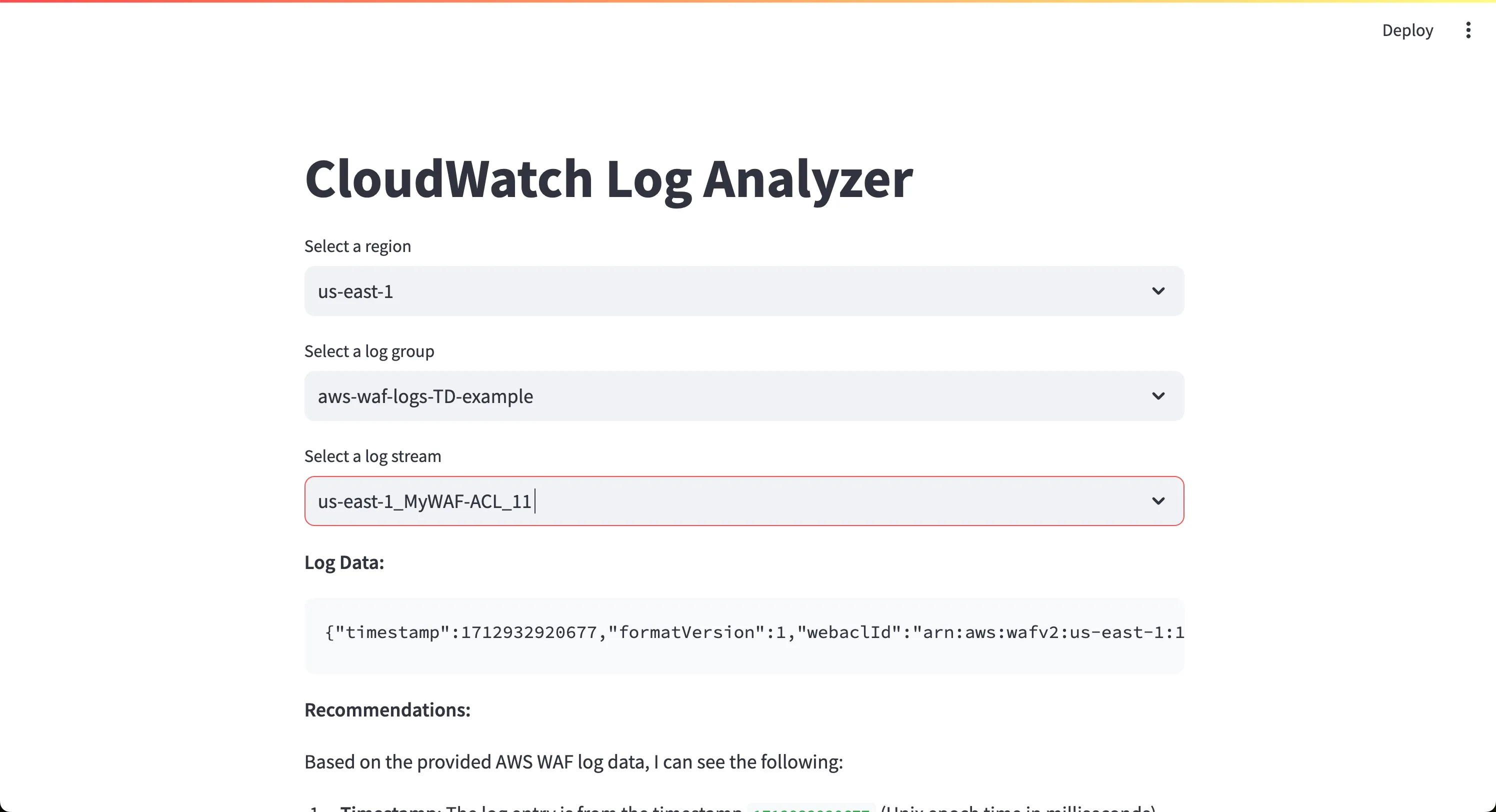
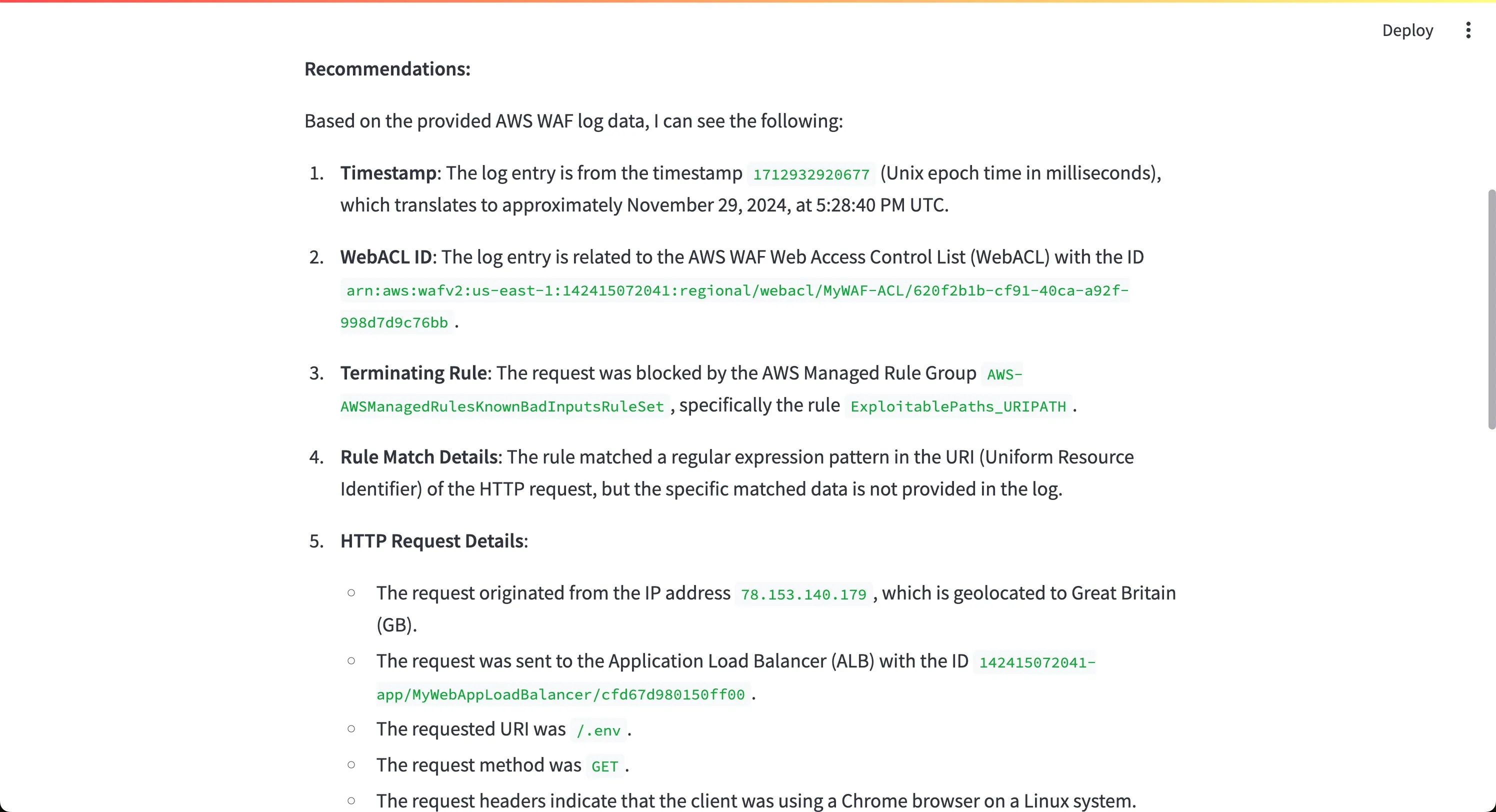
/.env being identified as a potential exploitation attempt by the ExploitablePaths_URIPATH rule in the AWS-AWSManagedRulesKnownBadInputsRuleSet rule group.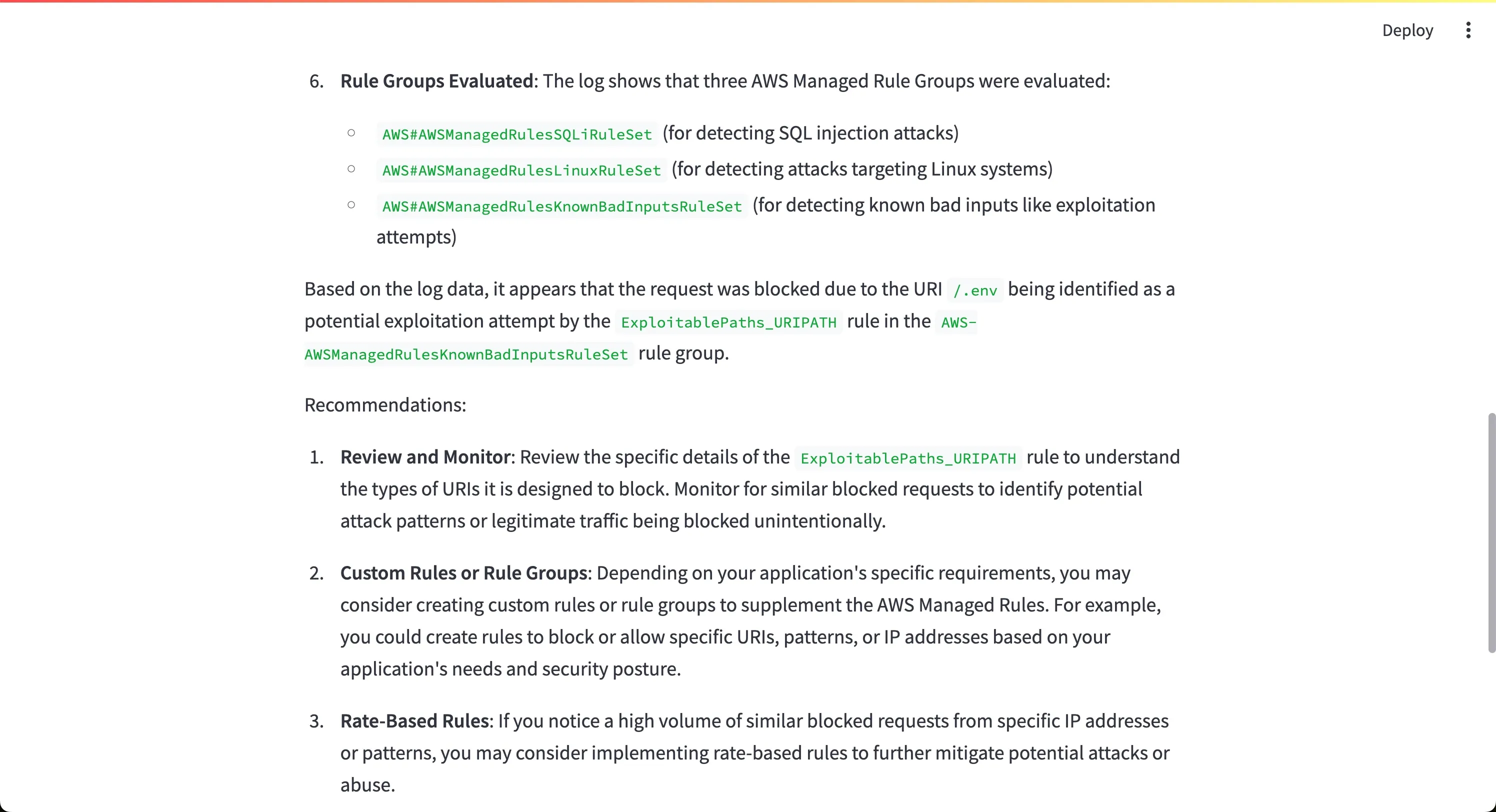
Any opinions in this post are those of the individual author and may not reflect the opinions of AWS.
