AWS re:Inforce 2024 re:Cap
AWS re:Inforce, annual security-oriented event finished last week, and in this article, Wojtek recaps the most important themes and takeaways from there.
So what exactly is AWS re:Inforce 2024?
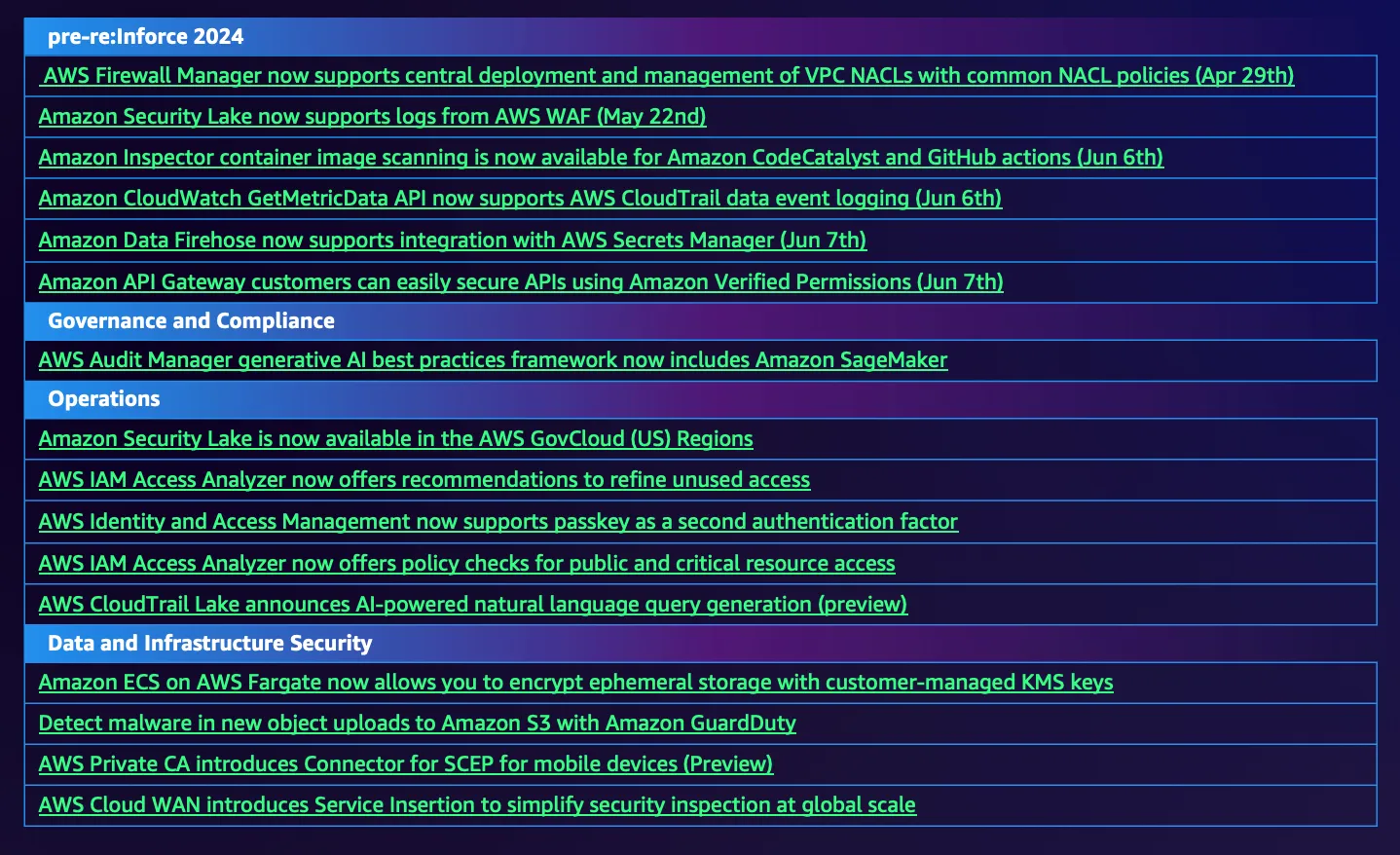
The Most Important Announcements
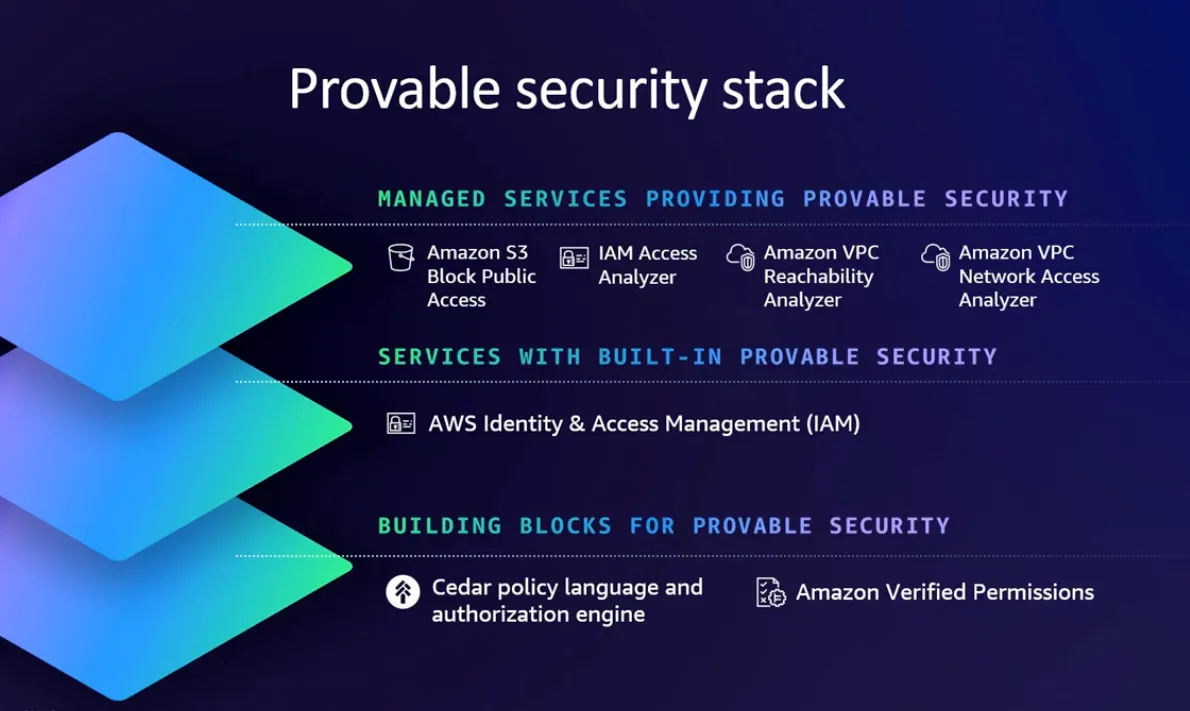
Provably secure authorization (SEC201-INT)
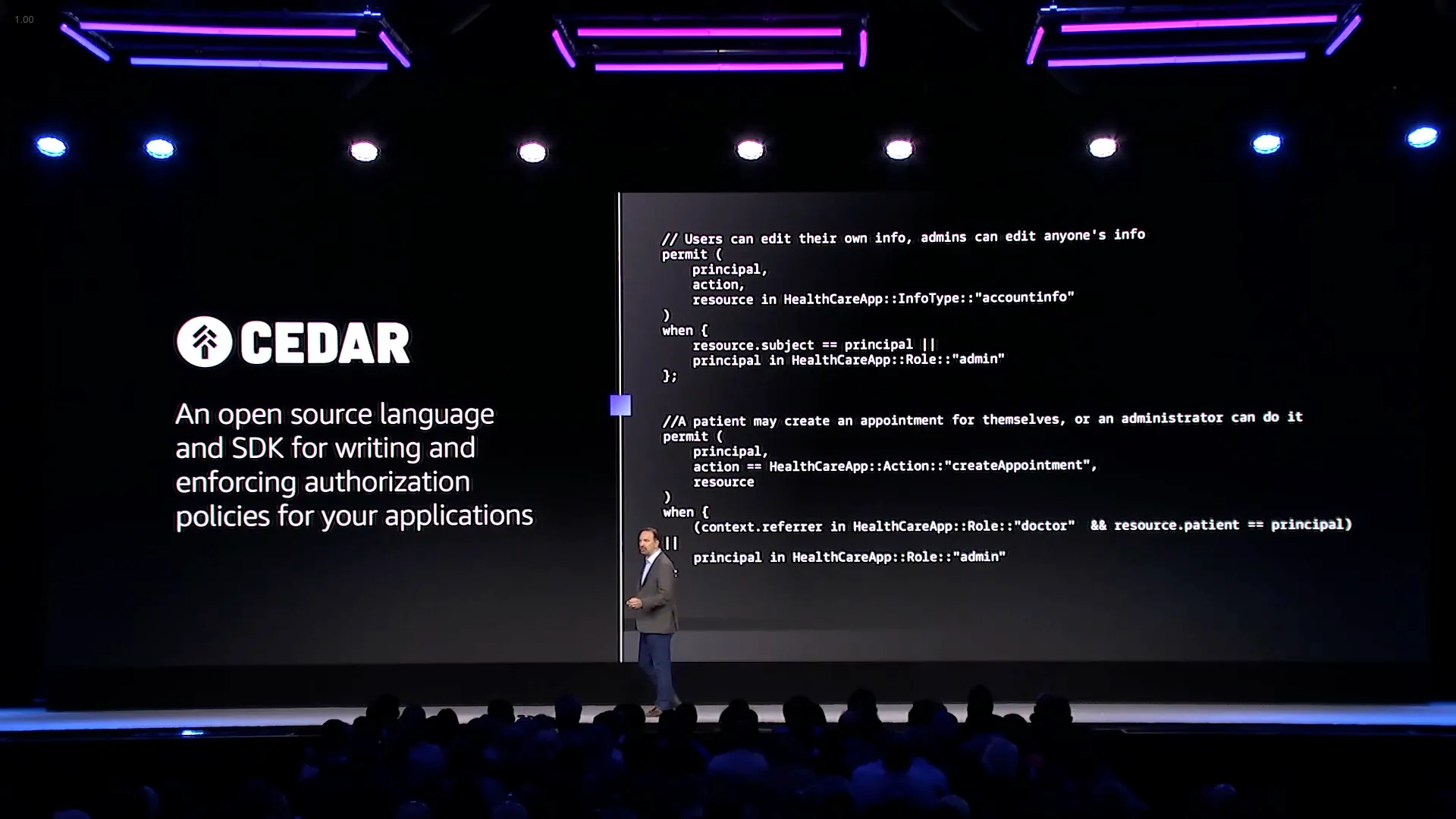
Access management: Customer use of Cedar policy & Verified Permissions (IAM201)
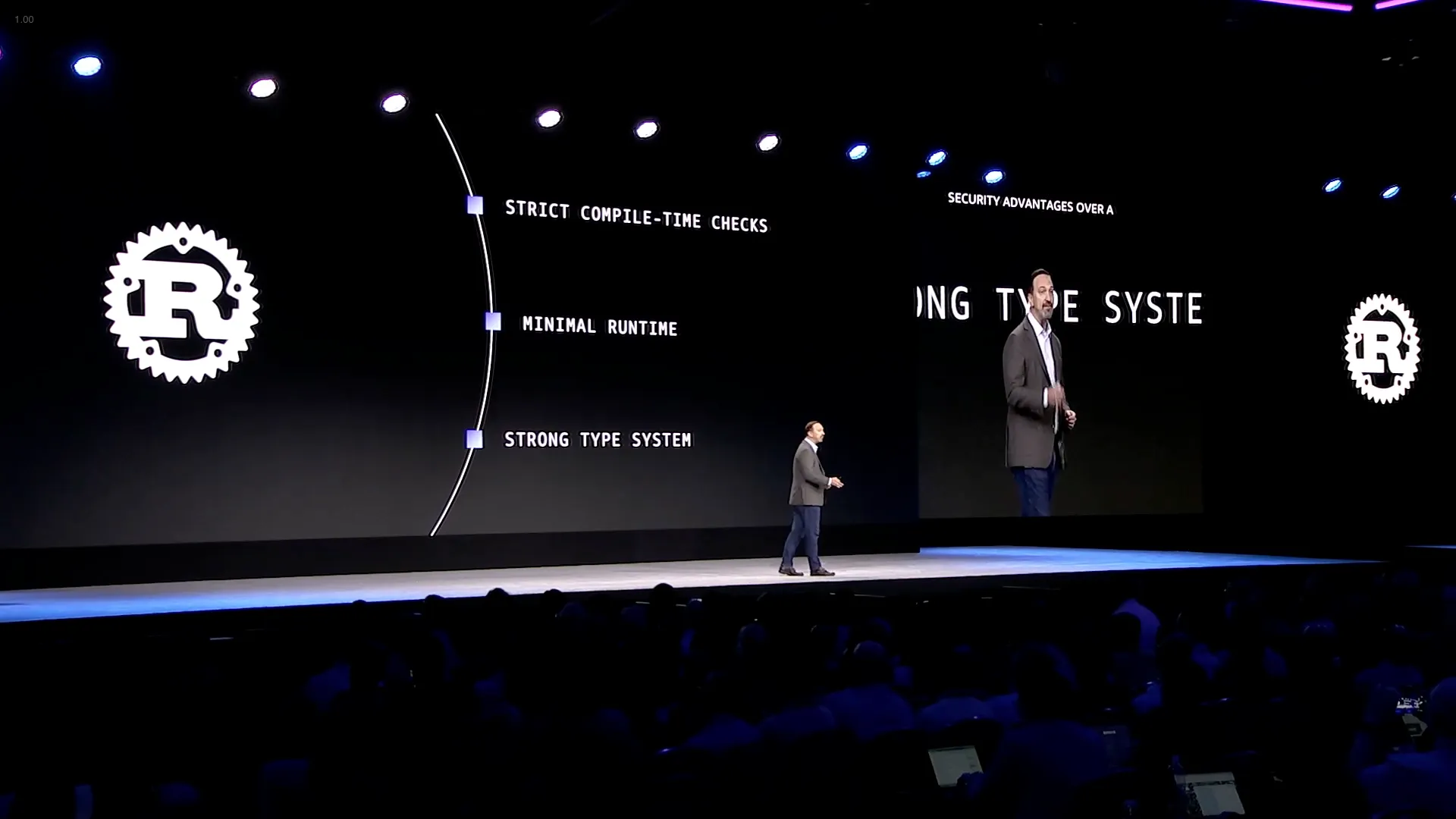
Strengthen open source software supply chain security: Log4Shell to xz (APS303)




Any opinions in this post are those of the individual author and may not reflect the opinions of AWS.
